Alcoholics Anonymous (AA) uses _____ steps in their program. Please choose the correct answer from the following choices, and then select the submit answer button. Answer choices
Answers
Alcoholics Anonymous (AA) uses 12 steps in their program. There are various other treatment options available for individuals struggling with addiction.
These steps are a set of principles that are meant to help individuals overcome their addiction to alcohol and achieve long-term sobriety. The 12 steps include admitting powerlessness over alcohol, turning to a higher power for help, taking a moral inventory, admitting wrongdoings, making amends, and helping others who suffer from addiction.
The program is based on the belief that alcoholism is a disease that can only be managed by abstaining from alcohol and changing one's way of life. AA meetings are held worldwide, and individuals attend to share their experiences, strength, and hope with others who are struggling with addiction.
The 12-step program has been effective for many individuals in achieving and maintaining sobriety. However, it is important to note that it may not be the best fit for everyone. There are various other treatment options available for individuals struggling with addiction, and it is important to find the right program that meets one's specific needs and goals.
Learn more about program :
https://brainly.com/question/14368396
#SPJ11
Related Questions
When first designing an app, all of the folldwing are important EXCEPT
A. debugging
B. determining how a user would interact with the app.
C. determining the purpose of the app
D. identifying the target audience
Answers
Answer:
B
Explanation:
Determining how the user could interact with the app varies person to person, the others are essential to creating apps though.
Write a sub program to find the factors of a supplied number
Answers
Answer:
There are two options I can think of for you,
(Qbasic Code)
To Find the Factors of Given Number:
CLS
INPUT "Enter any number"; n
FOR i = 1 TO n
x = n MOD i
IF x = 0 THEN
PRINT i;
END IF
NEXT i
END
To Find the Factors of Given Number Using COMMON SHARED:
DECLARE SUB factor ()
COMMON SHARED n
CLS
CALL factor
END
SUB factor
INPUT "Enter any number"; n
FOR i = 1 TO n
x = n MOD i
IF x = 0 THEN
PRINT i;
END IF
NEXT i
END SUB
Everything you do online is recorded in the cloud, but you can choose to erase it, as you have control over your digital footprint.
Group of answer choices
Answers
True. When you use online services or browse the internet, your activities can leave a digital footprint
What does this include?This encompasses details like your past internet activity, virtual communications, and any other information that might be saved on remote servers or in online storage.
As a person, you possess some authority over the reflection of your online presence. You possess the option to eliminate specific information or accounts, modify your privacy preferences, or restrict the extent of your online disclosures.
Although it may be difficult to completely delete all digital records, being proactive can assist in controlling and reducing your online presence.
Read more about digital footprint here:
https://brainly.com/question/17248896
#SPJ1
What best describes the development of 3-D graphics in the video game industry?
Responses
The ability to create them existed in the 1960s, but their use in the gaming industry has never really become popular.
The ability to create them existed in the 1960s, but their use in the gaming industry has never really become popular.
The ability to create them did not exist until the 1990s, but they became widespread as soon as the technology was there.
The ability to create them did not exist until the 1990s, but they became widespread as soon as the technology was there.
The ability to create them did not exist until the 2000s, and while they are easy to do, they are not widespread.
The ability to create them did not exist until the 2000s, and while they are easy to do, they are not widespread.
The ability to create them existed in the 1970s, but their use in the gaming industry did not become widespread until the 1990s.
Answers
The development of 3-D graphics in the video game industry dates back to the early 1970s, with the ability to create them existing at that time . However, their use in the gaming industry did not become widespread until the 1990s. Since then, advancements in technology have made it easier to create 3-D graphics, and they have become a standard feature in many video games.
which of the following can you apply to change the way a smartart graphic looks? question 11 options: a) smartart border b) smartart theme c) smartart design d) smartart style
Answers
The option to change the way a SmartArt graphic looks is d) SmartArt style. SmartArt styles allow customization of the overall appearance, including color, shape, layout, and formatting effects.
The correct answer is d) SmartArt style. SmartArt styles allow you to change the appearance of a SmartArt graphic by applying different combinations of color, shape, and formatting effects. By selecting a SmartArt graphic and applying a different style, you can quickly change its overall look and feel. SmartArt styles provide options for different color schemes, layouts, and other design elements that can enhance the visual impact of the graphic.
Learn more about SmartArt graphics here:
https://brainly.com/question/14311044
#SPJ11
What does CRM stand for in Big Data Analytics?
Answers
Answer: Customer Relationship management
Explanation: did it last year and it was correct
What do you understand by ISA? Does the external auditor follow
ISA or any regulatory body in conducting their audit? (150
words)
Answers
ISA stands for International Standards on Auditing. These standards are a set of globally recognized audit guidelines developed by the International Auditing and Assurance Standards Board (IAASB).
These standards aid in the achievement of international consistency and quality in auditing practices and provide for an objective methodology that auditors can use to measure the effectiveness of the audit process. It is relevant for both internal and external auditing.Internal auditors are in charge of verifying a company's accounts, processes, and systems. An internal auditor's function is to ensure that a company's financial data is correct, secure, and that all procedures are followed. Internal auditors should be familiar with ISA and use it to help guide their work.External auditors, on the other hand, are auditors who are not employed by the company they are auditing. External auditors must follow all ISA principles and guidelines to perform a fair and objective audit of a company's financial statements. External auditors are obliged to follow the auditing regulations and procedures of any regulatory body in addition to following ISA guidelines, as the auditing process is overseen by a number of regulatory bodies.In conclusion, the ISA provides guidelines that both internal and external auditors must follow. External auditors are required to comply with all ISA principles, regulations, and procedures in addition to the auditing guidelines of regulatory bodies.
To know more about Standards, visit:
https://brainly.com/question/31979065
#SPJ11
The unit has you writing a script that ends each level when a sprite gets to the right edge of the screen. Propose another “level completed” solution where the levels ends when the player hits a certain part of the screen WITHOUT relying on coordinates. Describe your solution, including the code blocks you would use instead of coordinates.
Answers
Answer:
I would make a system to go to the next level of the game without using coordinates by creating a finish line for each level that is a color like green or red. When the player’s sprite hits the finish line, it will activate a part of the code which will make the next level appear. To do this I will use an if statement. If the sprite is touching green, it will move to the next backdrop. This will create a way to go to the next level without using coordinates.
Explanation:
This is what i put as the answer, hope it helps! Dont forget to change it a little bit so you dont get flagged and stuff.
still consider using anomaly detection for intrusion detection. let's analyze a case. suppose alice's computer has 4 files (not realistic but for easy calculation...), and here are some data:
Answers
It is still recommended to use anomaly detection for intrusion detection. Anomaly detection is a method used in intrusion detection systems to identify unusual behavior that could be indicative of a security breach. It involves monitoring network traffic and system activity for any patterns or behaviors that deviate from the norm.
By identifying these anomalies, security analysts can investigate and respond to potential threats before any damage is done. In the case of Alice's computer, let's say she has four files. Using anomaly detection, her system activity would be monitored for any unusual behavior such as attempts to access or modify files that are not normally accessed, or connections to unknown or suspicious IP addresses.
If such behavior is detected, an alert is triggered, and security analysts can investigate the source of the anomaly to determine if it is a legitimate threat or a false positive. Anomaly detection is particularly useful in detecting zero-day attacks, which are previously unknown exploits that have not yet been identified by signature-based detection methods. Overall, anomaly detection is an important tool in an organization's security arsenal, and should be used in conjunction with other security measures such as firewalls, antivirus software, and intrusion prevention systems. Anomaly detection is a proactive approach to security that involves monitoring system activity for any deviations from the norm. It is used to identify potential security threats that may not be detected by traditional signature-based methods. By using anomaly detection, organizations can detect and respond to security breaches before they cause any significant damage. In the case of Alice's computer, anomaly detection would be used to monitor her system activity for any unusual behavior that could be indicative of a security breach Yes, anomaly detection can be used for intrusion detection in this case. Anomaly detection is a technique used to identify unusual patterns or behaviors that deviate from the norm. In the context of intrusion detection, it can help identify potential threats or intrusions on Alice's computer by analyzing the activities related to her 4 files. Establish a baseline: First, we need to create a baseline of normal activities or behaviors for Alice's computer. This could include file access patterns, file modifications, and network activities.
To know more about detection visit:
https://brainly.com/question/28284322
#SPJ11
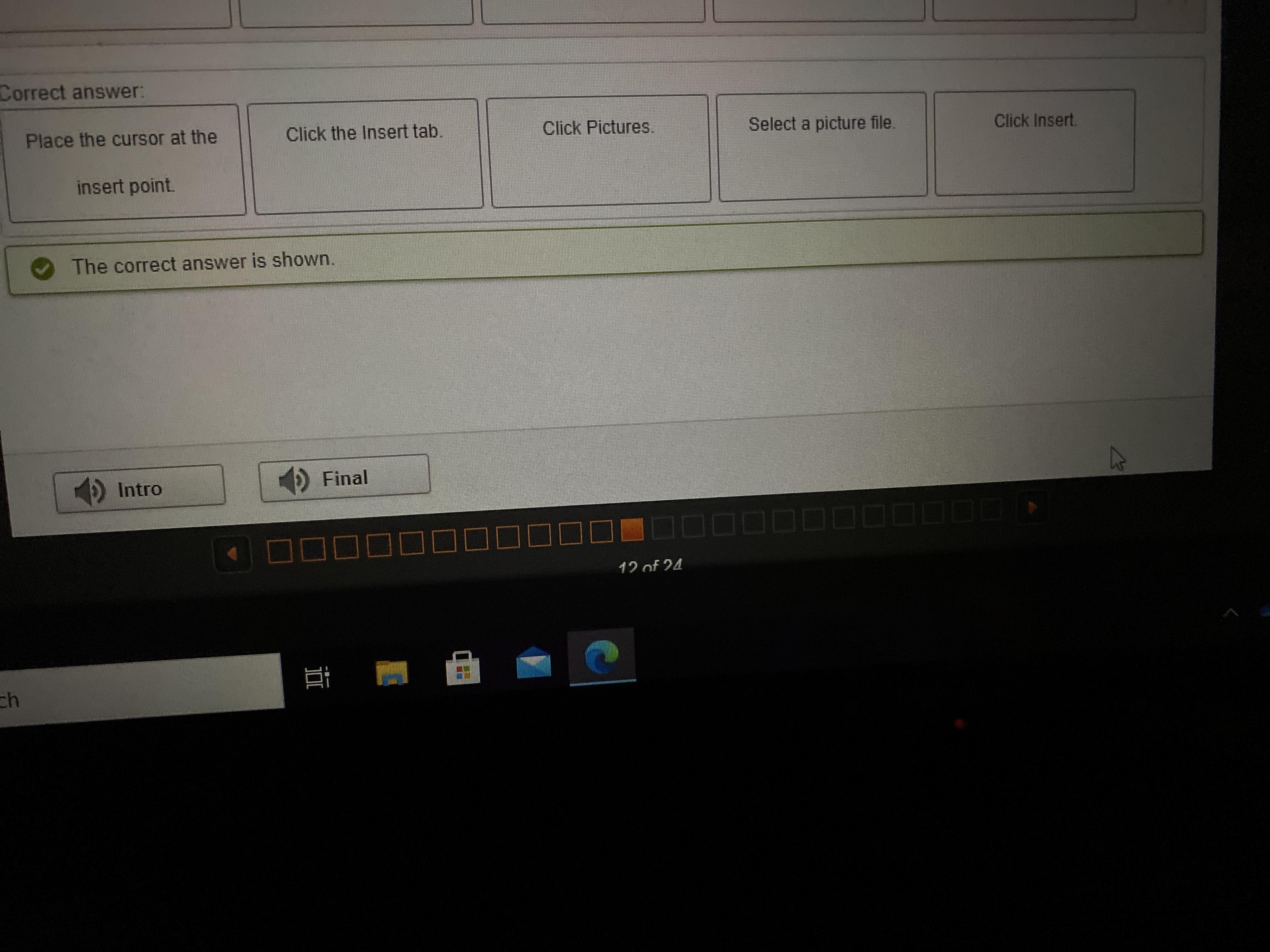
Describing How to Insert a Picture in a Document
What are the correct steps for inserting a picture into a Word 2016 document?
Click Insert.
Click Pictures.
Select a picture file.
Click the Insert tab.
Place the cursor at the
insert point.
Helllpppp
Answers
Answer:
Explanation:
Right answer
do you think fintechs, in general, will make trading markets more or less volatile? be specific and provide solid defense in your post for the position you take
Answers
I believe that overall FinTechs will reduce the volatility of trading markets in the future.
What does reduce volatility means?
Volatility is frequently used to describe the degree of risk or uncertainty associated with the magnitude of variations in a security's value. A security's value may potentially range over a wider range of values if its volatility is higher. This implies that the security's price can fluctuate sharply in either direction over a brief period of time. A security's value will not change significantly and will be more stable if its volatility is lower.
FinTechs employ technology to improve the function of finance and boost the effectiveness of operations in the financial and investing industries. Technology may be employed in financial trading, and it has a lot of benefits and conveniences to offer.
There are benefits in terms of efficiency, accessibility, cost effectiveness, and speed for different trading market participants. The settings and circumstances for market volatility are greatly diminished and diluted by the integration and convergence of all these components.
Additionally, a lot of FinTechs are using blockchain technology, which makes up for the shortcomings of the centralized system it replaces. It should be noted that one of the main causes of market volatility is the use of a centralized system. Blockchain is based on a decentralized system, which significantly reduces market volatility.
Additionally, FinTechs eliminate unnecessary legal and financial red tape, which enables the hosting of real-time secondary markets. FinTechs implement a safe and unquestionable infrastructure based on mathematical principles, which reduces the level of volatility in the trading markets.
Learn more about Volatility click here:
https://brainly.com/question/29394588
#SPJ4
Which is a correctly formatted Python tuple? [12, "circle", "square"] {"n":12, "shape1": "circle", "shape2": "square"} (12, "circle", "square") 12 circle square
Answers
Answer:
(12, "circle”, “square")
Explanation:
Python is a computer programming language that is used to write programs. In the python programming language, the Tuple is a data type that can be defined inside a parentheses "()". It is of immutable kind which means the elements inside the parentheses cannot be changed once the elements are inserted inside the tuple. It is also defined by "()" or by predefined function, tuple().
In the context, the correct format of python tuple is : (12, "circle”, “square").
Answer:
(12, "circle”, “square")
Explanation:
Q)What software application is the most effective tool to create charts of data? *
a)Word Processing software
b)Spreadsheet software
c)Photo editing software
d)Desktop Publishing software
Answers
Answer:
b) spreadsheet software
Which feature is used to change how a presentation moves from slide to slide?
Answers
Answer:
Click Slide Sorter on the View menu. On the Window menu, click Arrange All to display both presentations. Click the slide you want to move, and drag it to the other presentation. If you want to copy the slide across then hold down Ctrl as you drag the slide.
Explanation:
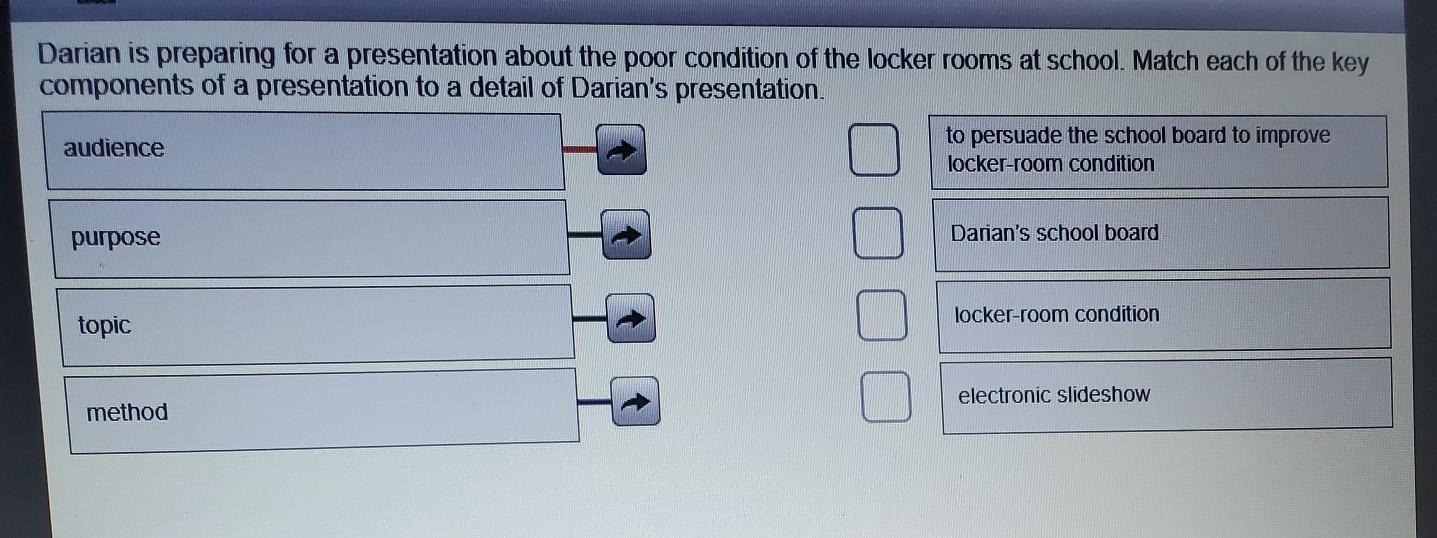
Darian is preparing for a presentation about the poor condition of the locker rooms at school. Match each of the key components of a presentation to a detail of Darian's presentation. audience to persuade the school board to improve locker-room condition purpose Darian's school board locker-room condition topic a electronic slideshow method can anyone
Answers
Answer:
Purpose - To paurswade the board to change the conditions of the locker room
Topic - Locker room condition
Method - Electronic Slideshow
Audience - School Board
Choose which type of translator you would use to develop a program written in a high-level programming language. Give three reasons to support your choice.
Answers
Answer:
Compilers
Explanation:
A compiler takes the source code as a whole and translates it into object code all in one go. Once converted, the object code can be run unassisted at any time. This process is called compilation.
Compilers have several advantages:
-Compiled programs run quickly, since they have already been translated.
-A compiled program can be supplied as an executable file. An executable file is a file that is ready to run. Since an executable file cannot be easily modified, programmers prefer to supply executables rather than source code.
-Compilers optimise code. Optimised code can run quicker and take up less memory space
hope this helped :D
The type of translator that you would use to develop a program written in a high-level programming language is known as Compiler.
What is a high-level programming language?The high-level programming language may be defined as a significant abstraction from the details of computer operation. It is designed to be easily understood by humans and for this reason, they must be translated by another software
A compiler significantly accepts the source code as a whole and successfully translates it into object code all in one go through the process of compilation. Compilers have several advantages. Some of them are as follows:
It compiled programs that run because they are already being successfully translated.A compiled program can be directly interpreted as an executable file that typically executes all essential and necessary functions.These compilers optimize code which improves performance, Reduced system load, protection for source code and programs, and improves productivity and quality.Therefore, the type of translator that you would use to develop a program written in a high-level programming language is known as Compiler.
To learn more about Compiler, refer to the link:https://brainly.com/question/27049042
#SPJ2
You must analyze data on a digital camera's internal memory. You plan to connect your forensic computer to the camera using a USB cable. What should you do to ensure that you do not modify data on the camera
Answers
A read-only device known as a forensic disk controller or a hardware write-blocker enables users to access the data on a questionable device without running the risk of changing or destroying the data.
What initial care should be taken with a mobile device to protect data?The easiest approach to handle a mobile device and protect data is to keep it powered on while enclosing it in a Faraday cage.
What program is used to image a disk for forensic purposes?The Autopsy and the Sleuth Kit are probably the two most well-known forensics toolkits. The Sleuth Kit is a command-line tool that does forensic examination of hard drive and smartphone forensic photos.
To know more about forensic disk visit:-
https://brainly.com/question/9692470
#SPJ4
3.5 code practice
grade = str(input("What year of high school are you in?: "))
if ("grade ==Freshman"):
print("You are in grade: 9")
elif ("grade == Sophomore"):
print("You are in grade: 10")
elif ("grade == Junior"):
print("You are in grade: 11")
elif ("grade == Senior"):
print("You are in grade: 12")
else:
print("Not in High School")
It keeps printing your are in grade 9. Why?
Answers
The fixed code is shown below. input() function already returns string that's why you don't have to convert string again. Also the syntax in if-else scope is wrong.
grade = input("What year of high school are you in?: ")
if(grade.lower()=="freshman"):
print("You are in Grade 9.")
elif(grade.lower()=="sophomore"):
print("You are in Grade 10.")
elif(grade.lower()=="junior"):
print("You are in Grade 11.")
elif(grade.lower()=="senior"):
print("You are in Grade 12.")
else:
print("Wrong input!")
Microsoft defender smartscreen prevented an unrecognized app from starting.
a. True
b. False
Answers
a. True. It is accurate to say that Microsoft Defender SmartScreen stopped an unauthorized app from running. When Windows finds an unidentified or possibly dangerous application.
The SmartScreen function stops it from running in order to safeguard the system from threats. Microsoft Defender, a built-in antivirus and security program in Windows 10 and subsequent editions, includes the SmartScreen function. A security tool called Microsoft Defender SmartScreen guards Windows users from harmful malware and phishing attacks. It is an integrated feature of Microsoft Edge, Microsoft Internet Explorer, and the Windows operating system that scans downloaded files and web pages against a database of known harmful websites and programs. When a person tries to download .
learn more about Microsoft here:
https://brainly.com/question/26695071
#SPJ4
Which meathod is used to create customized report
Answers
Answer:
0of the same thing as the other one example of a democracy
Explanation:
one day I was the first person to get a call from o
Answer: TestNG has provided an ability to implement 'IReporter' an interface which can be implemented to generate a customized report by users. It has 'generateReport ()' method which will be invoked after all the suite has completed its execution and gives the report into the specified output directory. Syntax for generateReport () method:
Explanation:
Imagine that you are participating in a project discussion for your community. write down at least three techniques that you can adopt in order to become an active listener.
become an active listener.
Answers
Active listening, responsive listening, and attentive listening are the three modes of effective listening. You can improve your listening accuracy and decrease the likelihood of misunderstanding by being aware of these modes.
Which method might an active listener employ?expressing concern To demonstrate understanding, paraphrase. using nonverbal cues, such as nodding, eye contact, and forward leaning, to demonstrate understanding. I see, I know, I sure, thank you, and I understand are succinct verbal affirmations.
What characterizes a good active listener?You must pay close attention to a speaker in order to understand what they are saying, then you must react to what they are saying, consider what they are saying, and remember what they said. As a result, the speaker and listener remain actively involved in the conversation.
To know more about affirmations visit:-
brainly.com/question/17705362
#SPJ4
What is operating System? Graphically explain the categorias
of operating System. Also mention the type of operating
System you are using
in your home.
Answers
Answer:
.............................................................. ..........
Privacy principles need to be balanced against the
private information. Select 2 options.
O financial
ethical
O corporate
D societal
political
benefit that comes from the automated collection of

Answers
In the case above about Privacy principles, the balanced needs to be
Societal.
What does privacy mean?The presence of informational privacy rights implies that people are said to be under a duty or not to make known information or to hinder unauthorized use of their information by others.
Note that when Privacy principles is balanced against Societal benefit that comes from the automated collection of private information. , the world will be at peace.
Learn more about Privacy principles from
https://brainly.com/question/10524592
#SPJ1
Beth wants to add information to her powerpoint presentation that is hidden from her audience and only she will see. which feature should she use? a. notes pane b. title slide c. normal view d. slide sorter view
Answers
For information that Beth wants to keep private from her audience and only see, she should add it to her PowerPoint presentation using the Notes pane.
Microsoft's PowerPoint presentation software enables users to design and deliver captivating presentations. It provides a selection of tools and features to assist users in producing presentations with a professional appearance using a range of material kinds, including text, photos, videos, and charts. PowerPoint is frequently used in a variety of contexts, including business meetings, academic lectures, and individual presentations, thanks to its user-friendly interface and customizable templates. In order to improve the presenting experience, it also provides elements like animations, transitions, and speaker notes. PowerPoint presentations can be given live, online, or via email, and they can be stored in a variety of file formats. Ultimately, PowerPoint is a flexible tool that may assist users in engaging their audience and effectively communicating ideas.
Learn more about PowerPoint here:
https://brainly.com/question/30038509
#SPJ4
You are planning a program to find the maximum heart rate recommended for patrons of a gym where you have a part-time job. One formula for calculating
the maximum heart rate is the difference between 220 and the patron's age.
You are testing for accuracy.
If a patron is 15 years old, what is the maximum heart rate?
Answers
The program would look like:
age = int(input("What's your age? "))
print(f"Your maximum heart rate is {220 - age}.")
If we input 15 as the age, the maximum heart rate is 220 - 15, which equals 205
The maximal heart rate is 220 minus 15, which is 205 if we enter 15 as the age.
What is meant by patrons?A patron is a special guardian, protector, or supporter of the arts as defined in definition. A wealthy or influential ally of an artist.
A patron is someone who frequently uses a business's services or makes financial contributions to another person or cause, such as an arts patron. A customer is someone who goes to the same restaurant every week, for instance.
Formal someone who often visits a particular restaurant, hotel, or other business. This parking lot is for customers only. synonyms and comparable words. a stay in a hotel or guesthouse. Bookable.
The word patron comes from the Latin pater or patr- meaning "father." Think of how a father is supposed to financially support his kids. A patron of the arts is someone who shows his appreciation or support for the arts by donating money to arts organizations.
Thus, The maximal heart rate is 220 minus 15,
For more details about patrons, click here:
https://brainly.com/question/16783674
#SPJ5
What is NOT a basic font category? A. Serif B. Sans-Serif C. Subtle-Serif D. Script
Answers
Answer:
I would say C.
Mobile phones are storehouse of knowledge and wisdom. And they are hazardous too.. write an article on the topic "The benefits and harms of mobile phones".
Answers
Answer:
Cellphones emit radiation.
Explanation:
Scientists did a study proving that cellphones emit radiation which is bad for humans.
i need help on what im doing wrong

Answers
Answer:
The error is that you're trying to convert a string with letters inside into an int. What happens if a user type in 'a' instead of '1'? 'a' is not a number so the int('a') would fail and give you an error. Make you add a line to check whether the input a number or not.
Explanation:
Change your code to
DEorAP = input("Is it AP or DE?")
if DEorAP.isdigit()
DEorAP = int(DEorAP)
SIMILAR TYPES OF FILES CAN BE PLACED INTO GROUP CALLED
Answers
FOLDERS are groups that can be used to group together similar types of files.
What is meant by FOLDERS?A folder may contain files or other directories (called "Subfolders"). Users can make folders to suit their organizational style.
Your files are stored and organized in folders. You can make as many folders as you need, as well as subfolders, which are folders inside other folders.
A file folder, often known as a folder, is a type of folder used to organize and safeguard documents and cash. Paper papers are kept in file folders, which are typically made of a sheet of thick paper stock or another thin but rigid material that has been folded in half.
A virtual storage space used to store and organize computer files is called a folder (or directory). A folder may also include other folders (known as subfolders).
To learn more about FOLDERS refer to:
https://brainly.com/question/20262915
#SPJ4
What is the purpose of a web server? What is the purpose of a web browser?
Answers
Answer: the purpose of a web browser is to help answer and needed questions, and to get to sites.
Explanation: