Any description of the goods which is made part of the basis of the bargain creates an express warranty that the goods shall conform to the description.
True
False
Answers
Any description of the goods which is made part of the basis of the bargain creates an express warranty that the goods shall conform to the description is true
What is express warranty?This sort of warranty is commonly seen on product packaging or warranty cards. An express warranty can be created by any statement, promise, description of goods, or sample which must conform to the guarantee claimed by a seller while selling any product
Elements in an express warranty case may include: The plaintiff purchased a product. The defendant gave an express warranty by way of a description of the product, a promise, or a fact. The product failed to perform according to the seller's description
An express warranty can take several different forms, whether spoken or written, and is basically a guarantee that the product will meet a certain level of quality and reliability. If the product fails in this regard, the manufacturer will fix or replace the product for no additional charge
To learn more about express warranty refers to:
brainly.com/question/15564074
#SPJ4
Related Questions
During which two phases of website development do developers construct diagrams to understand the website better?
gathering information
planning
design
development
launch
Answers
add code to define an hbox layout that is centered with an id of hbox and 10 pixels between controls. inside the hbox, add 2 buttons, with text open and close, and ids of open and close. clicking on either button triggers a call to the event handler flip method
Answers
To define an hbox layout that is centered with an id of hbox and 10 pixels between controls, you can use the following code:
```
```
This code creates an hbox element with an id of "hbox", and specifies that the controls within the hbox should be centered (using the "pack" attribute) and spaced 10 pixels apart (using the "spacing" attribute).
To add the two buttons with text "open" and "close" and ids of "open" and "close" to the hbox, you can use the following code:
```
```
This code creates two button elements with ids of "open" and "close", and text labels of "Open" and "Close", respectively. The "onclick" attribute is set to call the "flip()" method when either button is clicked.
To implement the "flip()" method, you can use the following code:
```
function flip() {
// Code to toggle the state of the buttons or perform other actions
}
```
This code defines a JavaScript function called "flip()", which can be used to toggle the state of the buttons or perform other actions as needed. You can add your own custom logic to this function to achieve the desired behavior when the buttons are clicked.
To define an hbox layout centered with an ID of "hbox" and 10 pixels between controls, along with the required buttons, follow these steps:
1. First, create the hbox layout and set its properties:
```xml
```
This creates an hbox layout with an ID of "hbox", sets spacing between controls to 10 pixels, and aligns the layout to the center.
2. Next, add the two buttons inside the hbox layout with the specified properties:
```xml
```
These lines add two buttons with IDs "open" and "close", text "Open" and "Close" respectively, and set the "onAction" attribute to call the "flip" method when either button is clicked.
3. Finally, close the hbox layout:
```xml
```
Putting it all together, your code should look like this:
```xml
```
This code defines an hbox layout centered with an ID of "hbox" and 10 pixels between controls, adds two buttons with text "Open" and "Close", and IDs of "open" and "close". Clicking on either button triggers a call to the event handler "flip" method.
To know more about JavaScript visit:
https://brainly.com/question/28448181
#SPJ11
_________________ is a set of commands used to control a databases, which includes security.
Answers
DCL or Data Control Language is a set of commands used to control a databases, which includes security. A data control language (DCL) is a computer programming language with syntax intended to manage access to data kept in databases.
It is specifically a component of Structured Query Language (SQL). Data Control Language is one of the logical groupings of SQL Commands. The predominant language used by relational database management systems is SQL. You can put data into a database, delete or change data there, or retrieve data from a database by using SQL commands. Database systems use SQL, but many also contain proprietary extensions of their own that are typically only used within the database system.
Learn more about database https://brainly.com/question/6447559
#SPJ4
You are writing an algorithm and want to tell the computer what to do if the user does not perform an action. Which type of statement should you include in your algorithm?
Answers
Answer:
If-else statements.
Explanation:
If-else statements, also know as selection statements help computer programs make dicision on how to handle different events or inputs.
pseudo code will look something like this:
if (condition):
do 1, 2, 3, ...
else:
do 4, 5 , 6, ...
If-else statements, also know as selection statements help computer programs make dicision on how to handle different events or inputs.
What is Algorithm?In either hardware-based or software-based routines, algorithms function as a detailed sequence of instructions that carry out predetermined operations sequentially.
All aspects of information technology employ algorithms extensively. A simple technique that resolves a recurring issue is typically referred to as an algorithm in mathematics and computer science. Algorithms are essential to automated systems because they serve as specifications for processing data.
An algorithm may be employed for simple tasks like sorting lists of numbers or for more challenging ones like suggesting user content on social media. The starting input and instructions for an algorithm's computation are often provided.
Therefore, If-else statements, also know as selection statements help computer programs make dicision on how to handle different events or inputs.
To learn more about Statement, refer to the link:
https://brainly.com/question/2285414
#SPJ7
All of the following are part of problem-solving tasks except . group of answer choices O define the problem O increase revenuesO specify evaluation criteria O implement solutions O evaluate alternatives
Answers
Answer:
Increase revenues
type two statements that use nextint() to print 2 random integers between (and including) 100 and 149. end with a newline. ex: 112 102 note: for this activity, using one statement may yield different output (due to the interpreter calling randgen.nextint() in a different order). use two statements for this activity.
Answers
Here are the two statements that use nextint() to print 2 random integers between (and including) 100 and 149. end with a newline
:Statement 1:print(randgen.nextInt(50) + 100);This statement will print a random integer between 100 and 149, inclusive.Statement 2:print(randgen.nextInt(50) + 100);This statement will print another random integer between 100 and 149, inclusive.These two statements use the nextInt() method to generate two random integers between (and including) 100 and 149.
The nextInt() method returns a pseudorandom, uniformly distributed int value between 0 (inclusive) and the specified value (exclusive), so we need to add 100 to it to get a value between 100 and 149 (inclusive). We are using two separate print statements because using one statement may yield different output due to the interpreter calling randgen.nextint() in a different order.
To know more about integers visit:
https://brainly.com/question/29834242
#SPJ11
Write a program in Python to compare between two numbers and print a message a greater than b.
Answers
Answer:
a = input("Enter the first number: ") b = input("Enter the second number: ") # if a is b: - Compares id's, and can cause inconsistencies. Use == instead. if a == b: print "Both inputs are equal" else: print "Your input is not equal."
List out analog computer
Answers
Answer:
1. Wall clocks.
2. Analog watches
3. Measuring instruments with callibration
Explanation:
Place the following STEM inventions in the correct chronological order, from the earliest to the most recent discovery.
Talking doll - Summly app - Blissymbol printer - circular saw
talking doll, circular saw. Blissymbol printer, Summly app
circular saw, Blissymbol printer, talking doll, Summly app
circular saw, talking doll, Blissymbol printer, Summly app
talking doll, Summly app, Blissymbol printer, circular saw
Answers
If I’m right, can you mark me brainliest please?
Answer:
c
Explanation:
lol
How do you identify quality resources on the Internet? There are 4 correct answers. Select each answer.
Question 3 options:
Check the information for accuracy by looking for references or searching for the same information with another source.
Determine if the information seems to balance pros and cons. If it's difficult to tell the difference between facts and opinions, the website may not be research based.
Determine who wrote the information. Anyone can post to the internet.
Find out when the information was published or edited last. The facts could be out of date.
When you conduct an Internet search, observe where the website is in the list of search results. The websites listed first are the most reliable resources.
Answers
Answer:
Every option except option E.) is true. I hope this helps! :)
your sdi nitrox diver certification allows you to use nitrox mixtures whose oxygen content ranges as high as 40 percent (ean40)?
Answers
Your sdi nitrox diver certification allows you to use nitrox mixtures whose oxygen content ranges as high as 40 percent (ean40).
The above statement is True.
What is a nitrox mixture?
Any mixture of nitrogen and oxygen gases, excluding trace gases, is referred to as nitrox. Included in this is atmospheric air, which consists largely of argon but also contains around 21% oxygen, 78% nitrogen, and 1% other gases.
Nitrox is a tool that can be useful when used properly, but deadly when not, just like every other piece of equipment and information a diver carries. With everything else being equal and the gas supply permitting, the nitrox has the goal to extend your no-stop dive time so that you can have longer dives and/or shorter surface intervals.
To learn more about nitrox, use the link given
https://brainly.com/question/28343107
#SPJ4
what kind of tag will give additional info about your webpage
Answers
Answer:
The LINK tag
Explanation:
Answer:
The LINK tag
Instead of producing a clickable link, the <link> tag tells the browser that there is some additional information about this page located in a different file.
Who is the founder of C language?
Answers
Answer:
Dennis Ritchie is the founder of C language.
When designing a security-in-depth strategy, security measures such as firewalls, vpns and sll would be examples of what type of control?.
Answers
In the designing of a security-in-depth strategy, security measures such as VPNs, SSL, and firewalls are examples of security controls.
Security controls are primarily developed to protect information systems from potenial security risks. Security controls are countermeasures and parameters that safeguard information systems against malicious security threats. Given the vast growing rate of cyberattacks, data security controls are considered vital secuirty meusre today more than ever. VPNs, SSL, and firewalls are some examples of security control.
VPNs: Virtual Private Networks (VPNs) establish a private and secure online connection to the Internet. With VPNs data traffic, IP address, and location of users remain hidden.
SSL: Secure Socket Layer (SSL) establishes an encrypted connection between a server and a client - such as a website and a browser. SSL authenticates the identity of a website and enables an encrypted connection.
Firewalls: A firewall refers to a network security device that monitors and filters outgoing and incoming network traffic based on preset security rules.
You can learn more about Security Controls at
https://brainly.com/question/27960062
#SPJ4
Which part of project management involves determining the overall work? Breakdown Incomes Scope Time
Answers
Answer:
Incomes
Explanation:
Project management has to do with the process of achieving a set goal with the help of a team within a specified time. Most times, the main problem that comes with project management is completing the project within the available constraints.
No project can start up without funds, which in this case is called income and this is the part of the project that determines the overall work.
Answer:
It's not income I just got it wrong I'm not really sure but I would assume it is breakdown I'm sorry if I'm wrong if I'm right please reward me brain list.
Surrendering to digital distractions will likely result in learning more material. O False True
Answers
Answer:True
Explanation:
coment on this if your user starts with dida
Answers
Answer:
oh sorry i needed points but i have a friend whos user starts with dida
Explanation:
OPERATION SHEET 6.2.2 Given the Neccesary tools materials and equipment identify the common faults and errors of computer when you detached the following Keyboard-PS/2 Mouse-PS/2 Hard disk- IDE cable Floppy disk drive-IDE cable Room disk-IDE CABLE

Answers
Answer: NO MORE TYPING! NO MORE CLICKING! NO MORE MEMORY! NO MORE OPERATING!
b) State 4 purposes of word
processing
Answers
Creating, editing, saving and printing documents.
Copying, pasting, moving and deleting text within a document.
Formatting text, such as font type, bolding, underlining or italicizing.
Creating and editing tables.
question 7 you want to access the cli (command line interface) of a linux terminal at work from your apple laptop at home. you have the proper client installed on your laptop. what needs to be installed on the remote linux machine?
Answers
To access the CLI of a Linux terminal at work from your Apple laptop at home, you need to have an SSH server installed on the remote Linux machine.
This will allow secure remote access using the proper client you already have installed on your laptop.In order to access the CLI of a Linux terminal at work from your Apple laptop at home, you would need to have the proper client installed on your laptop. As for the remote Linux machine, you would need to have an SSH server installed and configured in order to establish a secure connection between your laptop and the Linux terminal. This will allow you to access the command line interface remotely and execute commands on the Linux machine from your laptop.
Learn more about Linux here
https://brainly.com/question/30176895
#SPJ11
To access the CLI of a Linux terminal from an Apple laptop at home, the remote Linux machine needs to have an SSH (Secure Shell) server installed and running.
SSH is a network protocol that enables encrypted communication between the client and server while connecting to a distant machine. Many Linux distributions have an SSH server by default, although it may not be activated or configured to accept external connections.
To enable SSH access on the remote Linux computer, the system administrator must set up the SSH server to accept remote connections and, if applicable, any firewall rules to allow SSH traffic. In addition, the administrator may be required to establish user accounts and configure SSH keys for authentication.
Once the SSH server is fully configured, the user may connect to the distant Linux system and access the CLI using an SSH client on their Apple laptop. To establish the SSH connection, the user must know the IP address or hostname of the remote Linux computer and submit their login credentials. Once connected, the user may use their Apple laptop's terminal to perform commands on the remote Linux machine.
To learn more about Secure Shell, visit:
https://brainly.com/question/13888182
#SPJ11
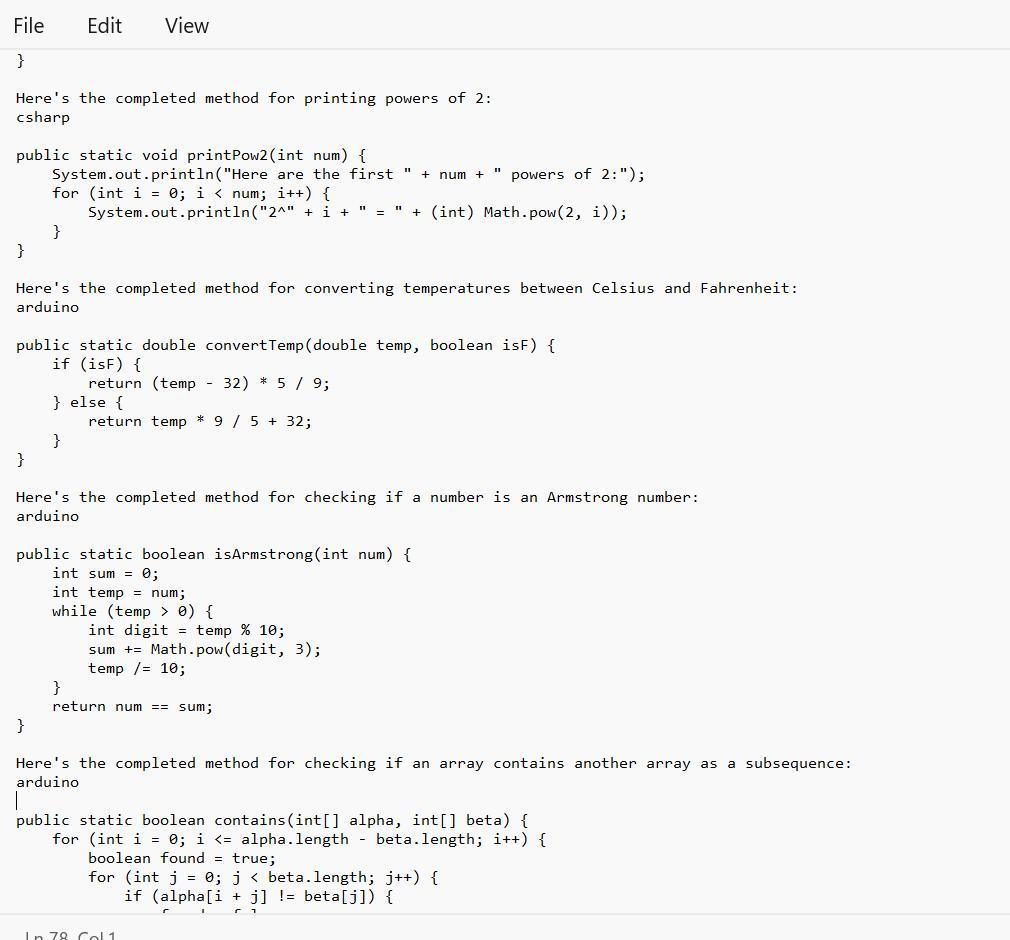
Java Coding help please this is from a beginner's class(PLEASE HELP)
Prior to completing a challenge, insert a COMMENT with the appropriate number.

Answers
Given in the images are the completed method that one can be able to use for a linear search on an array:
What is the Java Coding?The given text provides several programming code that bear completing the work of different styles.
Note tnat Each system has a specific set of conditions that need to be met in order to give the anticipated affair.
Therefore, code range from simple codes similar as performing a direct hunt on an array or publishing a board with a given size and pattern, to more complex codes similar as checking if one array contains another array in a successive and ordered manner.
Learn more about Java Coding from
https://brainly.com/question/18554491
#SPJ1
See text below
1) Complete the method: public static int simpleSearch(int[] nums, int value), that performs a linear (sequential) search on the array parameter, and returns the index of the first occurrence the of value parameter. Return -1 if value doesn't exist in nums.
simpleSearch(new int[] {8, 6, 7, 4, 3, 6, 5), 7) >>> 2
//2 is index of the value 7
2) Complete the method: public static void squareBoard(int num), that prints an num by num board with a '#' character in every position.
squareBoard(2) >>>
3) Complete the method: public static void checkerBoard(int num), that prints an num by num board with a '# character in every position in a 'checkerboard' fashion.
checker Board(3) >>>
4) Complete the method: public static void printPow2(int num), that prints num powers of 2 (including O), given the supplied number. Use String concatenation to print like this:
//with a call of printPow2(4):
Here are the first 4 powers of 2:
2^8 = 1
2^1 = 2
2^2 = 4
238
5) Complete the method: public static double convertTemp/double temp, boolean isF), that performs a Celsius to Fahrenheit conversion (and vice versa) when called. The parameter isF will be supplied as true if temp is in Fahrenheit.
6) Complete the method: public static boolean isArmstrong(int num), that returns true if the supplied number is an "Armstrong number". An Armstrong number is a number for which the sum of the cubes of its digits is equal to the number itself. Modulus and integer division will help.
IsArmstrong (371) >>> true //3*3*3+7*7*7+ 1*1*1 == 371
7) Difficulty level HIGH: Complete the method: public static boolean contains(int[] alpha, int[] beta). that returns true if the sequence of elements in beta appear anywhere in alpha. They must appear consecutively and in the same order. You'll need nested loops for this.
contains(new int[] {1, 2, 1, 2, 3), new int[] {1, 2, 3}) >>> true
contains (new int[] 1, 2, 1, 2, 3, 1), new intf (1, 1, 3, 1)) >>> false


What type of general commands allow a security tester to pull information from a Web server using a web browser?
Answers
The type of general commands that allow a security tester to pull information from a Web server using a web browser are HTTP requests. HTTP stands for Hypertext Transfer Protocol, and it's the primary protocol used to communicate between web browsers and servers. There are several types of HTTP requests, including GET, POST, PUT, DELETE, and HEAD.
A security tester can use a web browser to send GET requests to a web server to get information such as HTML pages, pictures, and other resources. POST requests can be used to send information to a server, such as login credentials or form data. PUT requests are used to update existing server resources, whereas destroy requests are used to destroy server resources. HEAD requests are similar to GET requests in that they get only the response headers, which might be useful for determining the server's status.
A security tester can use HTTP requests to retrieve information from a web server and evaluate it for vulnerabilities such as SQL injection or cross-site scripting (XSS). However, it's important to note that security testing should only be performed on systems that the tester has permission to test, to avoid any legal or ethical issues.
To learn more about HTTP requests, visit:
https://brainly.com/question/30427343
#SPJ11
How are game designers linked with game players?
A.
In order to be a game player, you must be a game designer.
B.
In order to be a game designer, you must have extensive experience playing video games.
C.
Game designers must survey potential game players before creating a new game.
D.
Game designers create a narrative that game players can shape and become personally involved in.
Answers
The way in which game designers linked with game players is that: D. Game designers create a narrative that game players can shape and become personally involved in.
What is a game development tool?A game development tool can be defined as a set of specialized software programs that are used by game developers (programmers) for the design and development of a game such as the following:
EmulatorGame engineModeling toolLevel editorScripting toolAdditionally, the four (4) team responsibilities that are required to create a game include the following:
The game designer create the rules and characters.The programmer writes an executable set of instructions (code).The artist choose colors and design each characters.The game designers create a narrative that game players can shape.Read more on game development here: https://brainly.com/question/13956559
#SPJ1
help plz
1. Write a function to return the larger of two numbers entered from two user inputted values, where the user inputs are entered after the displays of “First Entry =” and “Second Entry = ”. The numbers should be decimal values (not just integers).
2. Write a function to return the word that is first alphabetically from two user inputted text entries, where the user inputs that text by entering their own words after the displays of “First Entry =“ and “Second Entry =“. Remember that you can use the operators with strings. (You can assume that the user only inputs lower case words.)
Answers
1.
first = float(input("First Entry = "))
second = float(input("Second Entry = "))
def func(num1, num2):
return max(num1, num2)
print(func(first, second))
2.
first = input("First Entry = ")
second = input("Second Entry = ")
def func(word1, word2):
return sorted([word1,word2])[0]
print(func(first, second))
I hope this helps!
In this exercise we have to use the knowledge of computational language in python to write the following code:
The code can be found in the attached image.
That way, to find it more easily we have the code like:
First code:first = float(input("First Entry = "))
second = float(input("Second Entry = "))
def func(num1, num2):
return max(num1, num2)
print(func(first, second))
Second code:first = input("First Entry = ")
second = input("Second Entry = ")
def func(word1, word2):
return sorted([word1,word2])[0]
print(func(first, second))
See more about python at brainly.com/question/26104476


In __________ write, the data are stored in the cache, and control returns to the caller.
Answers
In an asynchronous write, the data are stored in the cache, and control returns to the caller.
An asynchronous write is a write operation that does not block the caller until the data is actually written to the underlying storage. The data is instead stored in the cache, and control returns to the caller. When the data is eventually written to the underlying storage, the write is said to be "completed".
Asynchronous writes can be useful in situations where blocking the caller is not desirable, or where the time to complete the write is not known in advance. For example, an application that is writing data to a slow storage device may choose to use an asynchronous write in order to avoid blocking the caller while the data is being written.
Learn more about Asynchronous write here:
https://brainly.com/question/10057909
#SPJ4
HELP ME
what is the full form of BYE,AIDS,ASCC
Answers
Can somoene explain the function of-
def __init__():
In python programming language
Answers
Answer:
def is a keyword used to define a function, placed before a function name provided by the user to create a user-defined function
__init__ is one of the reserved methods in Python. In object oriented programming, it is known as a constructor. Python will call the __init__() method automatically when you create a new object of a class, you can use the __init__() method to initialize the object’s attributes.
Example code:
class Person:
def __init__(self, name, age):
self.name = name
self.age = age
p1 = Person("John", 36)
print(p1.name)
print(p1.age)
Summary
Use the __init__() method to initialize the instance attributes of an object. The __init__() doesn’t create an object but is automatically called after the object is created.After thoroughly evaluating a supplier, many organizations summarize evaluations using a supplier ____ matrix-a type of weighted scoring model.
Answers
After thoroughly evaluating a supplier, many organizations summarize evaluations using a supplier evaluation matrix-a type of weighted scoring model.
What is evaluation matrix?This is a tool, used to measure proposals, submitted by suppliers. It is basically meant to rank proposals based on defined criteria so that the best can be chosen.
In evaluation matrix, a score is assigned to each criteria that was considered under different categories and then the supplier with the highest score is selected to do business with.
Using evaluation matrix assess the suitability of suppliers to the business, who can work with the business for a long time hence, an essential tool for planning and organizing an evaluation.
Learn more about evaluation matrix here: https://brainly.com/question/15071654
#SPJ1
Create a class CapacityManager to manage restaurant dining capacity. You should provide a public constructor that allows the capacity of the restaurant to be set as an int when the CapacityManager is created. You don't need to provide either a getter or a setter for the capacity, which will not change.
Answers
The CapacityManager class is designed to manage the dining capacity of a restaurant. It provides a public constructor that accepts an integer value representing the capacity of the restaurant. The capacity value is set during the creation of the CapacityManager object and does not need to be changed or accessed using getters or setters.
The implementation of the CapacityManager class in Java:
public class CapacityManager {
private final int capacity;
public CapacityManager(int capacity) {
this.capacity = capacity;
}
// Other methods and functionalities can be added here
// Example method to check if the restaurant is at full capacity
public boolean isFull() {
// Implementation logic to check if the number of occupied seats is equal to the capacity
// Return true if full, false otherwise
return false;
}
}
In this implementation, the CapacityManager class has a private instance variable capacity of type int, which is set through the constructor. The capacity variable is marked as final to indicate that its value cannot be changed once set.
The constructor public CapacityManager(int capacity) allows the capacity of the restaurant to be set as an int when creating an instance of the CapacityManager class.
The example also includes a method isFull() as an example functionality. This method can be used to check if the restaurant is at full capacity based on some logic that determines the number of occupied seats.
The implementation of this method may vary depending on the specific requirements and business rules of the restaurant's capacity management.
To learn more about constructor: https://brainly.com/question/14616046
#SPJ11
Select the three type of undesirable software.
virus
firewall
peer-to-peer
nannyware
adware
malware
VPN
Answers
Virus, Adware, Malware