Disk fragmentation causes reduced disk performance because the disk read/write heads must move longer distances. A) True B) False.
Answers
The given statement "Disk fragmentation causes reduced disk performance because the disk read/write heads must move longer distances" is option A. True because fragmented files consolidate them into contiguous blocks, allowing the read/write heads to access data more efficiently.
When files are fragmented, their data is divided into smaller pieces and scattered across different physical locations on the disk. This fragmentation disrupts the sequential and contiguous layout of data, which is optimal for the disk read/write heads to access data quickly. When a file is fragmented, the disk read/write heads needs to seek and move to different locations on the disk to retrieve each fragmented piece of the file.
This results in increased seek times and longer latencies, as the read/write heads need to physically traverse longer distances across the disk's surface. The longer seek times introduce delays in accessing data, leading to reduced disk performance. In addition to increased seek times, disk fragmentation also affects the disk's throughput. As fragmented files are scattered across the disk, the read/write heads need to constantly reposition themselves, causing additional overhead.
This constant repositioning further slows down the data transfer rate and overall disk performance. To mitigate the performance impact of disk fragmentation, it is recommended to regularly defragment the disk. By reducing the need for extensive head movement, defragmentation helps improve disk performance by minimizing seek times and enhancing data throughput. Therefore, the correct answer is option A.
know more about disk fragmentation here:
https://brainly.com/question/31935553
#SPJ11
Related Questions
Anyone who uses search engines should be aware that the content of their searches could become public.
True or false
Answers
The given statement "Anyone who uses search engines should be aware that the content of their searches could become public." is true.
Using search engines does come with the risk that the content of searches could potentially become public. While search engine providers generally prioritize user privacy and take measures to safeguard user data, it is still important for individuals to be aware of the potential risks and exercise caution when conducting searches.
Search engine data collection: Search engines collect data about users' search queries, including the terms they search for, the time and date of the searches, and sometimes the user's IP address or location. This data is typically used to improve search results and provide personalized recommendations.
Data retention: Search engines may retain this search data for varying periods of time, depending on their privacy policies and legal obligations. Even if the data is initially anonymized, there is a possibility that it could be linked back to individual users through other means.
Data breaches: While search engines implement security measures to protect user data, data breaches can still occur. In the event of a breach, search data could potentially be exposed to unauthorized parties, including the content of users' searches.
Legal requests and government surveillance: Search engines may be subject to legal requests or government surveillance, which could lead to the disclosure of user search data. In certain jurisdictions, search engines may be required to comply with court orders or government demands to provide access to user data.
Third-party data sharing: Search engines often have partnerships or advertising networks that may collect user data for targeted advertising purposes. This data sharing could involve sharing search history or search preferences with third parties, potentially exposing the content of searches to external entities.
Given these factors, it is important for individuals to understand that there is a potential risk that the content of their searches could become public. While search engines strive to protect user privacy, it is advisable to exercise caution, be mindful of the information being searched for, and consider using additional privacy-enhancing measures, such as using encrypted search engines or virtual private networks (VPNs), if desired.
For more such questions on search engines, click on:
https://brainly.com/question/512733
#SPJ8
what type of error occurred??

Answers
Answer:
Syntax Error.
Explanation:
n
Which of the following is not a goal of a persuasive speaking?
a. to motivate to action
b.
to change attitudes, beliefs, or values
to strengthen or weaken attitudes, beliefs, or values
d. to define, demonstrate, or instruct
C.
Answers
Answer: D. to define, demonstrate, or instruct.
Explanation:
Persuasive speaking is the form of speaking that we usually engage in. It is used to convince people. As individuals, we usually engage in persuasive speaking. We argue about different things and try to convince the other person to agree with us.
Th goals of persuasive speaking is to motivate to action, to change attitudes, beliefs, or values and to strengthen or weaken attitudes, beliefs, or values.
It should be noted that the goal of persuasive speaking isn't to to define, demonstrate, or instruct. Therefore, the correct option is D.
Answer:
Simple Answer: D
Three popular types of ____ are handheld computers, PDAs, smart phones.
Answers
Answer:
portable media players, and digital cameras
Explanation:
Three popular types of mobile devices are handheld computers, PDAs, and smart phones.
What are smart phones?Smart phones can be defined as hybrid versions of mobile devices that are designed and developed to have more features, so as to enable them run different applications, functions and tasks with the aid of software applications such as web browsers, multimedia player, etc.
In Computer technology, three popular types of mobile devices are handheld computers, PDAs, and smart phones.
Read more on smart phones here: https://brainly.com/question/15867542
#SPJ2
Which of the strategies below are likely to increase audience attention?
Responses
Use similar animation styles on each slide.
Use similar animation styles on each slide.
Avoid the use of animations.
Avoid the use of animations.
Use consistent transitions.
Use consistent transitions.
Match special effects to content.
Match special effects to content.
Use lots of different animation styles on each slide.
Use lots of different animation styles on each slide.
Vary the use of transitions for each slide.
Vary the use of transitions for each slide.
Answers
Answer:
A, B, and C
Explanation:
Use similar animation styles on each slide
Use consistent transitions.
Match special effects to content.
Which is a type of artificial neural network (ann) that includes many layers to deal with complex problems that may have very large data sets?
Answers
Answer:
Deep Learning
Explanation:
The kind of artificial neural network (ann) that includes many layers to deal with complex problems that may have very large data sets is called a Deep neural network.
What is an artificial neural network?Artificial neural networks, more commonly referred to as neural networks or neural nets, are computer architectures that draw inspiration from the biological neural networks seen in animal brains.
Artificial neurons, which are a set of interconnected units or nodes that loosely resemble the neurons in a biological brain, are the foundation of an ANN.
Deep Learning is a type of artificial neural network (ann) that has several layers to handle complicated issues that may have very big data sets. Deep neural networks use advanced math modeling to interpret input in complicated ways.
Learn more about artificial neural networks here:
https://brainly.com/question/19537503
#SPJ2
Help me. its due tonight

Answers
b- national service !
you are querying a database that contains data about music. each album is given an id number. you are only interested in data related to the album with id number 3. the album ids are listed in the album id column.you write the following sql query, but it is incorrect. what is wrong with the query?
Answers
The SQL query provided for the question is incorrect. In order to understand the error and to correct it, let's first look at the SQL query provided:
SELECT *FROM music
WHERE album_id = 3;
The above SQL query is incorrect because the query doesn't contain any table name. The table name is missing in the FROM clause. The FROM clause specifies the name of the table from where the data is required. In the given query, only the column name is specified, but the table name is missing.In this situation, the query must have the table name from which we want to retrieve data. Therefore, the correct SQL query for this would be:
SELECT *FROM album
WHERE album_id = 3;
In the above query, we have used the table name as "album" instead of "music". The table "album" contains the data about the album and its properties, which include album_id. So, we use the correct table name, which helps the database to look for the required data in the specified table.
Learn more about SQL here:
https://brainly.com/question/30901861
#SPJ11
What do you think is the role of technology, specifically the
Information Systems in the packaging industry? (describe in 250 to
300 words)
Answers
Information Systems have transformed the packaging industry by streamlining operations, automating processes, improving inventory management, ensuring quality control, enabling traceability, and facilitating data analysis. By embracing technology, packaging companies can enhance their competitiveness, meet customer demands, and adapt to the evolving market landscape.
Information Systems have revolutionized the packaging industry, providing numerous benefits to manufacturers, suppliers, and consumers.
1. Firstly, technology enables automation in packaging processes, reducing manual labor and increasing productivity. Automated packaging machines can handle tasks such as filling, sealing, labeling, and palletizing, leading to faster and more accurate packaging operations.
Through the use of barcode or RFID tracking systems, companies can monitor and track inventory levels, ensuring timely replenishment and minimizing stockouts or excess inventory. Real-time data on inventory status enables efficient supply chain management and reduces operational costs.2. Quality control is another crucial aspect in the packaging industry, and technology plays a vital role in ensuring product integrity.
3. Automated inspection systems can detect defects, inconsistencies, or contaminants in packaging materials or finished products, ensuring compliance with quality standards and reducing the risk of faulty packaging reaching consumers.
4. Information Systems also enable traceability throughout the packaging process, ensuring transparency and accountability.
By integrating production data, lot numbers, and expiration dates, companies can trace products back to their origins, facilitating recalls, managing expiration dates, and addressing quality concerns promptly.5. Lastly, technology empowers data analysis and decision-making in the packaging industry. Advanced analytics tools can process large volumes of data to identify patterns, trends, and opportunities for improvement. This data-driven approach helps optimize packaging designs, reduce waste, improve sustainability, and enhance overall operational efficiency.
Learn more about traceability here:
https://brainly.com/question/33451052
#SPJ11
what is the minimum cable specification that supports 1000 mbps ethernet?
Answers
which method of an exception object will provide information about the chain of method calls that led to the exception? group of answer choices printcallstack() getcallstack() printstacktrace() getstacktrace()
Answers
The method that provides information about the chain of method calls that led to an exception is called printStackTrace().
When an exception occurs, it creates an exception object that contains information about the error, including the methods that were called leading up to the error. By calling the printStackTrace() method on the exception object, you can print this information to the console or a log file. This can be useful for debugging and understanding the cause of the error. The other options listed (printcallstack(), getcallstack(), getstacktrace()) are not valid methods for retrieving this information. It's important to handle exceptions properly in your code to avoid unexpected errors and to provide useful feedback to the user.
To know more about debugging visit:
brainly.com/question/31534133
#SPJ11
How do I make the text and heading different colors?
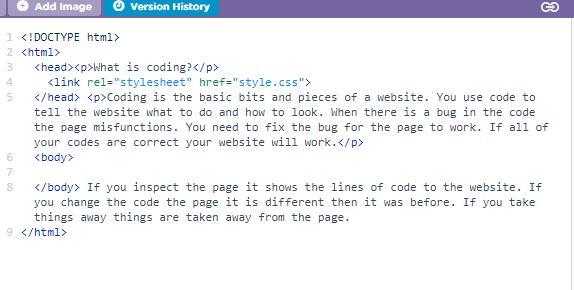
Answers
Answer: do u have word if you do go to font and u can change ur font
Explanation:
How do you answer this ?

Answers
Answer:
Just put True or false for your answer
Explanation:
Use a Dictionary
What type of targeting is being used by an ad network that delivers ads targeted by age, gender, and net worth?
Answers
The type of targeting being used by an ad network that delivers ads targeted by age, gender, and net worth is demographic targeting.
Demographic targeting is a form of audience segmentation where ads are tailored and delivered based on specific demographic characteristics of the target audience. In this case, the ad network is using age, gender, and net worth as criteria to refine the targeting of their ads. By considering these demographic factors, the ad network aims to reach users who fall within certain age groups, genders, and income brackets that align with the desired target audience for the advertised products or services.
Demographic targeting is a widely used strategy in digital advertising technology because it allows advertisers to focus their marketing efforts on specific consumer segments that are more likely to be interested in their offerings. By targeting ads based on age, gender, and net worth, advertisers can tailor their messages and creative content to resonate with the characteristics and preferences of their target audience. This helps optimize the effectiveness and efficiency of ad campaigns by reaching the right people with the right message at the right time.
It is worth noting that while demographic targeting can be valuable for reaching specific consumer segments, it is important to handle such targeting ethically and in compliance with privacy regulations to ensure that user data is used responsibly and with proper consent.
Learn more about technology here:
brainly.com/question/9171028
#SPJ11
The quick access toolbar can be customized, but the ribbon can not be customized. True or false?.
Answers
Answer:
False
Explanation:
_______ is the use of software to assist in the creation, analysis, and modification of the design of a component or product.
Answers
Answer:
C) Computer-aided Design
Explanation:
Options:
a. Computer-aided engineering
b. Computer-aided evaluation
c. Computer-aided design
d. Computer-aided manufacturing
C) Computer-aided design is correct answer
(Hope this helps can I pls have brainlist (crown)☺️)
(JAVA PLS)
Your job in this assignment is to write a program that takes a message as a string and reduces the number of characters it uses in two different set ways. The first thing your program will do is ask the user to type a message which will be stored as a String. The String entered should be immediately converted to lowercase as this will make processing much easier. You will then apply two different algorithms to shorten the data contained within the String.
Algorithm 1
This algorithm creates a string from the message in which every vowel (a, e, i, o, and u) is removed unless the vowel is at the very start of a word (i.e., it is preceded by a space or is the first letter of the message). Every repeated non-vowel character is also removed from the new string (i.e., if a character appears several times in a row it should only appear once at that location). So for example the string "I will arrive in Mississippi really soon" becomes "i wl arv in mssp rly sn".
After applying this algorithm, your program should output the shortened message, the number of vowels removed, the number of repeated non-vowel characters removed, and how much shorter the shortened message is than the original message. The exact format in which the program should print this information is shown in the sample runs.
Algorithm 2
This algorithm creates a string by taking each unique character in the message in the order they first appear and putting that letter and the number of times it appears in the original message into the shortened string. Your algorithm should ignore any spaces in the message, and any characters which it has already put into the shortened string. For example, the string "I will arrive in Mississippi really soon" becomes "8i1w4l2a3r1v2e2n1m5s2p1y2o".
After applying this algorithm, your program should output the shortened message, the number of different characters appearing, and how much shorter the shortened message is than the original message. The exact format in which the program should print this information is shown in the sample runs.
Sample Run 1
Type the message to be shortened
This message could be a little shorter
Algorithm 1
Vowels removed: 11
Repeats removed: 2
Algorithm 1 message: ths msg cld b a ltl shrtr
Algorithm 1 characters saved: 13
Algorithm 2
Unique characters found: 15
Algorithm 2 message: 4t2h2i4s1m5e2a1g1c2o1u3l1d1b2r
Algorithm 2 characters saved: 8
Sample Run 2
Type the message to be shortened
I will arrive in Mississippi really soon
Algorithm 1
Vowels removed: 11
Repeats removed: 6
Algorithm 1 message: i wl arv in mssp rly sn
Algorithm 1 characters saved: 17
Algorithm 2
Unique characters found: 13
Algorithm 2 message: 8i1w4l2a3r1v2e2n1m5s2p1y2o
Algorithm 2 characters saved: 14
Answers
import java.util.Scanner;
public class JavaApplication54 {
public static int appearance(String word, char letter){
int count = 0;
for (int i = 0; i < word.length(); i++){
if (word.charAt(i) == letter){
count++;
}
}
return count;
}
public static void main(String[] args) {
Scanner scan = new Scanner(System.in);
System.out.println("Type the message to be shortened");
String message = scan.nextLine();
message = message.toLowerCase();
int volCount = 0, repCount = 0, num = 0;
char prevC = ' ';
String vowels = "aeiou";
String newMessage = "";
for (int i = 0; i < message.length(); i++){
char c = message.charAt(i);
if (vowels.indexOf(c) != -1 && prevC == ' '){
newMessage += c;
}
else if (vowels.indexOf(c) == -1 && prevC != c){
newMessage += c;
}
else if (vowels.indexOf(c) != -1){
volCount ++;
}
else{
repCount++;
}
prevC = c;
}
System.out.println("Algorithm 1");
System.out.println("Vowels removed: "+volCount);
System.out.println("Repeats removed: "+repCount);
System.out.println("Algorithm 1 message: "+newMessage);
System.out.println("Algorithm 1 characters saved: "+(message.length() - newMessage.length()));
String uniqueMessage = "";
for (int i = 0; i<message.length(); i++){
char w = message.charAt(i);
if (uniqueMessage.indexOf(w)== -1 && w!=' '){
uniqueMessage += appearance(message,w)+""+w;
num++;
}
}
System.out.println("Algorithm 2");
System.out.println("Unique characters found: "+num);
System.out.println("Algorithm 2 message: "+uniqueMessage);
System.out.println("Algorithm 2 characters saved: "+(message.length() - uniqueMessage.length()));
}
}
I hope this helps!
Which of the following are universally common items that are synced between a mobile device and a larger computer? (Choose three.)
A. Office documents
B. Contacts
C. Operating system files
D. Email
E. Configuration settings
F. Apps
Answers
Answer:
email ur answer plllllllllllll mark me brainlest.......... .........………....….Which finger types the highlighted keys?

Answers
Answer:
Index
Explanation:
The index finger lays positioned upon the 4 key.
In terms of Reward power, what is
the power of big media and how has it changed given technological
changes in the
last twenty years?
Answers
Reward power refers to the power an individual possesses to offer rewards or benefits to others as an incentive to influence their behavior.
The big media is a term used to refer to the large media outlets or companies that control the flow of information to the public. It includes television networks, radio stations, newspapers, and other forms of mass media. The power of big media in terms of reward power has increased significantly in the last twenty years due to technological changes and advancements.The introduction of new technologies such as the internet, social media platforms, and mobile devices has enabled big media to reach a wider audience than ever before.
As a result, the power of these companies has increased, and they now have a greater influence over public opinion and behavior. They use their reward power to offer incentives to their audience in exchange for their loyalty or support. This includes rewards such as free subscriptions, exclusive content, and discounts on products or services.Technological changes have also made it easier for big media to collect data on their audience's behavior and preferences.
This data can be used to tailor their content to meet the specific needs and interests of their audience. By doing so, they can increase their reward power and maintain their dominance in the industry.Overall, the power of big media in terms of reward power has increased significantly in the last twenty years due to technological advancements. They use their reward power to influence the behavior of their audience and maintain their dominance in the industry.
Learn more about networks :
https://brainly.com/question/31228211
#SPJ11
What file extension corresponds to a sas dataset?
a. .sas
b. .xlsx
c. .txt
d. .csv
e. .xls
f. .sas7bdat
g. .dat
Answers
The file extension that corresponds to a SAS dataset is f. .sas7bdat.
This file extension is specific to SAS (Statistical Analysis System) software and is used to store structured data. The .sas7bdat extension represents a binary format that contains the actual data and metadata associated with a SAS dataset.
Other file extensions listed in the question, such as .sas, .xlsx, .txt, .csv, .xls, and .dat, are used for different file formats and are not specific to SAS datasets. It is important to use the correct file extension when working with SAS datasets to ensure compatibility and accurate data representation.
To know more about file visit:
https://brainly.com/question/32971966
#SPJ11
Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
look at the answer above mine
Answers
Answer:
ok will do
Explanation:
but hi again friend
In the future, where will an increasing majority of data come from?
Answers
In the future, where will an increasing majority of data come from the cloud.
Where will more of data come from?A lot of Data volumes is said to increase and thus it will move or migrate to the cloud.
Note that the majority of big data experts were said to have agree that the numbers of generated data will grow very fast in the future and it will be one that its growth can come from social data, machine data or transactional data.
Learn more about data from
https://brainly.com/question/19243813
introduction of waste management
Answers
Answer:
Waste management (or waste disposal) includes the activities and actions required to manage waste from its inception to its final disposal. ... Waste management deals with all types of waste, including industrial, biological and household. In some cases, waste can pose a threat to human health.
FIRST ANSWER GETS BRAINLIEST IM GIVING 30 POINTS!!!! Select the correct answer. Emma's project team has to create an application within a short period of time. After a few considerations, the team decided to go ahead with the RAD model. How does the RAD model decrease development time? A. by using automated tools and reusing existing code B. by gathering all requirments in the first phase of the project C.by testing at the end of the life cycle D. by producing detailed documentation
Answers
Answer:
RAD model enables rapid delivery as it reduces the overall development time due to the reusability of the components and parallel development. ... Iteration time can be short with use of powerful RAD tools. Productivity with fewer people in a short time. Reduced development time.
The RAD model decreases development time by using automated tools and reusing existing code. which is the correct answer would be option (A).
What is the RAD model?The RAD model stands for Rapid Application Development. It is an implementation of an incremental model. The components or functions of the RAD model are created in concurrently as if they were mini-projects. The developments are timed, delivered, and then integrated into a functional prototype.
Because of component reusability and simultaneous development, the RAD approach offers quick delivery. Iteration time can be reduced by using strong RAD tools. Productivity with fewer individuals in a short period of time. Development time has been decreased.
Thus, the RAD model decrease development time by using automated tools and reusing existing code.
Hence, the correct answer would be option (A).
To learn more about the RAD model click here:
https://brainly.com/question/28903361
#SPJ2
two different datasets with the same mean will also have the same standard deviation. true or false
Answers
False. Two different datasets with the same mean can have different standard deviations.
Standard deviation measures the spread of a dataset, while mean represents the central tendency. Therefore, datasets with different variances can have the same mean. For example, a dataset with values close to the mean will have a lower standard deviation than a dataset with values farther away from the mean, even if they have the same mean. It's important to consider both the mean and standard deviation when analyzing datasets.
learn more about datasets here:
https://brainly.com/question/31190306
#SPJ11
1 What do you understand by navigation through form?
Answers
Answer:
A navigation form is simply a form that contains a Navigation Control. Navigation forms are a great addition to any desktop database. Microsoft Access offers several features for controlling how users navigate the database.
which table style option shows the field names when it is checked?
Answers
The table style option that shows the field names when it is checked is the "Header Row" style.
When you select this option, the first row of the table is treated as the header row and displays the field names for each column in the table. This style option is particularly useful when working with large tables that have many columns, as it makes it easy to identify which column each field belongs to. It also helps to ensure that the table is well-organized and easy to read.
To apply the "Header Row" style to a table, simply select the table and then click on the "Design" tab in the Table Tools section of the Ribbon. From there, you can select the "Header Row" option to display the field names in the first row of the table.
In addition to the "Header Row" style, there are several other table style options available in software Microsoft Word that can be used to customize the appearance of tables. These include options for shading, borders, and font styles, among others. By experimenting with different table styles, you can create tables that are both functional and aesthetically pleasing.
Learn more about software :
https://brainly.com/question/1022352
#SPJ11
Where are options to add a border around the outside of a chart found?
Design tab in the Chart Layout gallery
Format tab in the Shape Styles group
Layout tab in the Background group
Insert tab in the Format gallery
Answers
Answer:
Format tab in the Shape Styles group
Explanation:
The border can be added around the chart which could be of various types including dashed, dotted or plane line.
The border can be added around the chart by moving the cursor over the shape styles section of the ribbon. This gives instant border around the chart and for customization, you can click the format tab below chart tools tab. Now click the Shape outline button. We can also select the style and size of the border.
Thus, the selected option is the correct answer.
Answer:
B.
Explanation:
I do smart.