given the following er diagram (where a is connected to r with a regular line, and r is connected to b with a bold line with a regular arrow), which of the following statements are true? a) true false r connects each entity in a to at least one entity in b (b) true false r connects each entity in a to at most one entity in b (c) true false r connects each entity in b to at least one entity in a (d) true false r connects each entity in b to at most one entity in a g
Answers
For the ER diagram (where A is connected to R with a regular line, and R is connected to B with a bold line with a regular arrow), the following statements are true:
True: R connects each entity in A to at most one entity in B.
True: R connects each entity in B to at least one entity in A.
Thus, the correct option is (B) and (C).
The regular line connecting entity A with entity R indicates a one-to-many relationship, i.e., one entity A can be connected with several entities R. The bold line with the regular arrow connecting entity R with entity B indicates a one-to-one relationship, i.e., one entity R is connected with at most one entity B.
To learn more about "er diagram", visit; https://brainly.com/question/31143445
#SPJ11
Related Questions
Write a for loop that sets each array element in bonusscores to the sum of itself and the next element, except for the last element which stays the same. Be careful not to index beyond the last element.
Answers
We can easily iterate an array and add each element to an accumulating variable to determine the sum of all the elements in the array.
The result of S = sum(A) is the total number of elements in A along the first array dimension whose size is not 1. Sum(A) returns the sum of the elements if A is a vector. Sum(A) provides a row vector holding the sum of each column if A is a matrix. The loop is used to repeatedly run the block of code in accordance with the condition stated in the loop. It entails repeated execution of the same code, which helps to traverse an array's items while also saving code.
Learn more about array here-
https://brainly.com/question/19570024
#SPJ4
How fast can nsa computers at the time of the movie attempt guesses at a password?
Answers
A computer can think of more than 100,000,000,000 passwords per second.
What are a computer's primary purposes?A computer system's four primary equipment operations are input, processing, storage, and output. The following tasks are routinely performed by computers as part of their functions: obtaining, processing, returning, and storing data. Computer devices can be categorized as input devices, processing devices, output devices, and storage devices, in that order, to assist computer systems in carrying out these tasks. A function is a derived type because the type of the data it returns determines its type. Arrays, pointers, enumerated types, structures, and unions are the other derived types. Bool, char, int, extended, float, double, long double, complex, etc. are examples of basic types.
To learn more about computers, refer to:
https://brainly.com/question/21474169
#SPJ4
1)write a python program to check wheter the given number is even or odd
2) write a python program to add any 5 subjects makrs, find sum and average (average=sum/5)
3)write a python program to print numbers from 1 to 100 using loops
Answers
Answer:
n = 16
if n%2:
print('{} is odd'.format(n))
else:
print('{} is even'.format(n))
m1 = 5
m2 = 4
m3 = 6
m4 = 8
m5 = 9
sum = m1+m2+m3+m4+m5
average = sum/5
print("The sum is {}, the average is {}". format(sum, average))
for i in range(1, 101): print(i, end=",")
Explanation:
Above program does all three tasks.
Answer:
1) num1 = int(input("Enter the number to be checked: "))
if num1%2==0:
print("Your number is an even number!")
else:
print("Your number is not even!")
2) maths = int(input("Enter your maths mark: "))
english = int(input("Enter your english mark: "))
social = int(input("Enter your social mark: "))
science = int(input("Enter your science mark: "))
computer = int(input("Enter your computer mark: "))
Sum = maths + english + social + science + computer
average = Sum / 5
print("Sum of your marks are:",Sum)
print("average of your marks are:",average)
3) num = 0
while num <= 99:
num+=1
print(num)
Explanation:
Welcome.
Fill in the blank: Sticker sheets are useful in a design system because _____.
designers can work faster and avoid rework
Answers
Answer:
Sticker sheets are useful in a design system because they enable designers to quickly and easily copy and paste components into new designs, reducing the amount of time needed to create designs and avoiding the need for rework.
Explanation:
They enable designers to produce reusable visual components that are consistent with the brand, enhancing user experience all around.
Technical definition sheet: What is it?A technical data file (TDS) is just a document that comes with a product and contains a variety of details about the item. Technical data sheets frequently feature information about the product's composition, usage guidelines, technical specifications, typical applications, cautions, and product images.
What does the word "sheets" mean?Paper each is typically rectangular in appearance. especially: equipment specifically engineered for printing. (2) : a mounted plant specimen on a relatively thin, rectangular sheet of paper. a 100,000 sheet important to the advancement.
To know more about Sheets visit :
https://brainly.com/question/30277396
#SPJ4
which of the following not an example of written communication?
Answers
A conversation between co-workers is not an example of written communication as it involves verbal communication. The correct option is D.
What is written communication?The exchange of information or messages via written words is referred to as written communication. All spoken and written communications fall under this category.
Emails, memos, letters, reports, notes, social media posts, and text messages are all examples of written communication.
Because spoken words are involved, a conversation between coworkers would not qualify as a written communication example.
Thus, the correct option is D.
For more details regarding written communication, visit:
https://brainly.com/question/10664960
#SPJ9
Your question seems incomplete, the probable complete question is:
Which of the following is NOT an example of written communication?
Tweets
Blogs
Emails
A conversation between co-workers
Some one help pls will mark brainless !!!!!
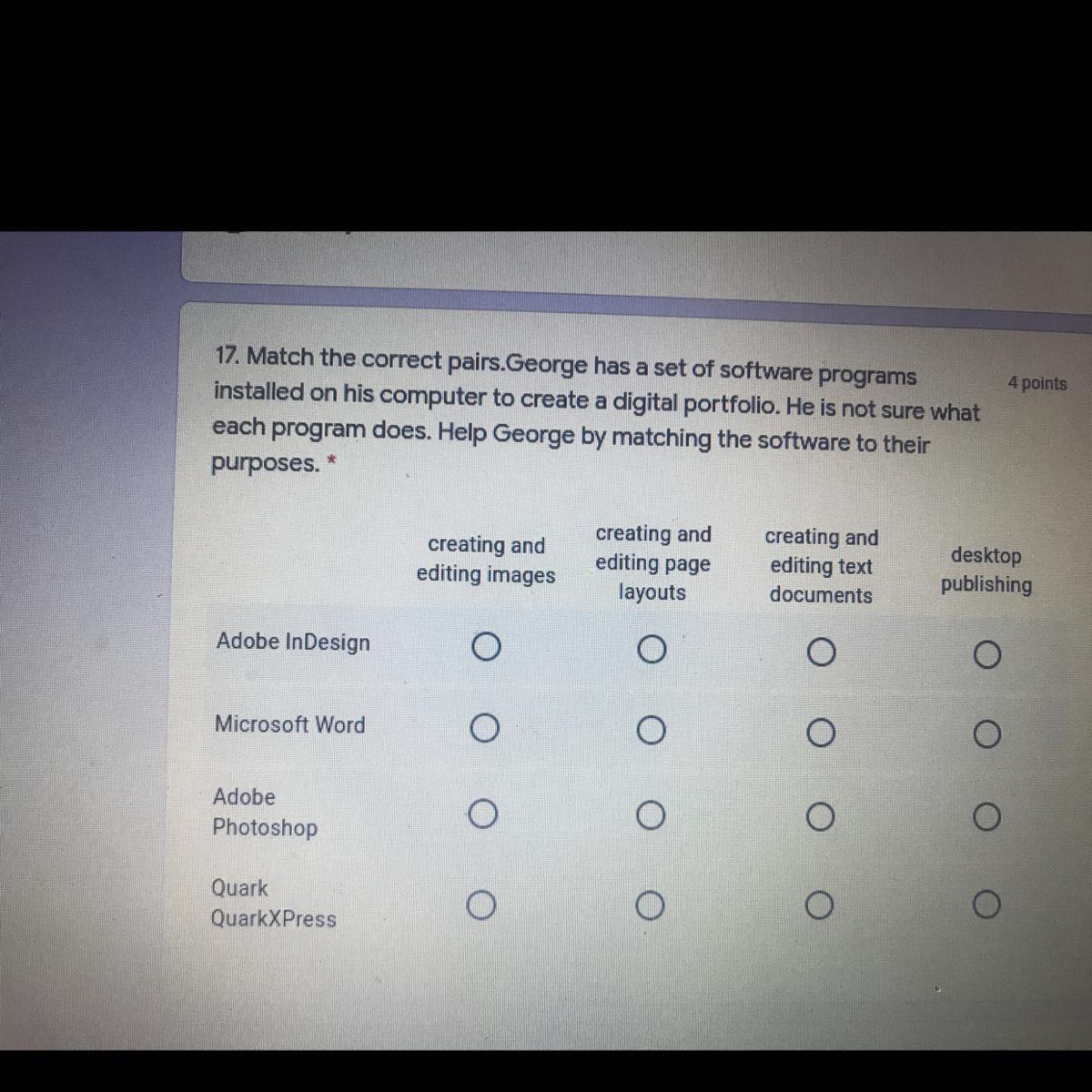
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
Could 13.5\text{ cm}, 8.0\text{ cm},13.5 cm,8.0 cm,13, point, 5, start text, space, c, m, end text, comma, 8, point, 0, start text, space, c, m, end text, comma and 3.5\text{ cm}3.5 cm3, point, 5, start text, space, c, m, end text be the side lengths of a triangle?
choose 1 answer:
Answers
Yes, they could be the side lengths of a triangle.
Yes, the side lengths 13.5 cm, 8.0 cm, and 3.5 cm can form a triangle. To determine if these lengths create a valid triangle, we can use the Triangle Inequality Theorem. The theorem states that for any triangle, the sum of the lengths of any two sides must be greater than the length of the remaining side. In this case:
1. 13.5 cm + 8.0 cm > 3.5 cm (21.5 cm > 3.5 cm)
2. 13.5 cm + 3.5 cm > 8.0 cm (17 cm > 8.0 cm)
3. 8.0 cm + 3.5 cm > 13.5 cm (11.5 cm > 13.5 cm)
All three conditions are satisfied, so the given side lengths can form a triangle.
To know more about triangle visit:
https://brainly.com/question/2773823
#SPJ11
If it’s a tcp connection, which is the first segment that computer 1 needs to build?
Answers
Hi! I'd be happy to help with your question. If it's a TCP connection, the first segment that Computer 1 needs to build is the SYN (Synchronize) segment.
Computer 1 initiates the TCP connection by sending a SYN segment to Computer 2. The SYN segment contains an initial sequence number.Computer 2 receives the SYN segment and sends a SYN-ACK (Synchronize-Acknowledge) segment back to Computer 1, containing an acknowledgement number and its own initial sequence number.Computer 1 receives the SYN-ACK segment and sends an ACK (Acknowledge) segment back to Computer 2 to complete the TCP three-way handshake.In summary, the first segment that Computer 1 needs to build in a TCP connection is the SYN segment.
Learn more about TCP connection: https://brainly.com/question/27960058
#SPJ11
In this module you learned about making decisions. You learned about the syntax and rules used to develop programs containing decisions and how the logic can make your programs more robust.
Draw a flowchart for a program that shows the logic for a program that generates a random number and the player tries to guess it.
There are NO LOOPS, NO Functions(other than the random number generator) and NO MODULES at this point. Everything at this point is in sequence(Line-By-Line). You can add comments at the beginning of each block to explain what the code is doing..
Declare the variables and data types used
import random (Generate random integers using Python randint() - AskPython )
You want to add the code so the player can enter their name, then display a welcome message using their name.
You also want to display a message that describes what the program will do.
The program should allow the player to guess the number that was randomly generated.
Display a message indicating whether the player’s guess was too high, or too low.
When your program ends, thank the person for playing and display "Game Over"
Complete the Python code using IDLE Editor.
Complete the flowchart. Upload the exported PDF to the Blackboard assignment area by clicking on the Browse My Computer button below the text editor.
Answers
A flowchart for a program that shows the logic for a program that generates a random number and the player tries to guess it, and declares the variables and data types used, imports random (Generate random integers using Python randint() - AskPython), and displays a message that describes what the program will do.
Let's see the solution step-by-step:
Step 1: Importing the random module and declaring variables import randomplayer = input("Enter your name:")# Declare variables and data types usedrandom_number = random.randint(1,100)guess = 0print(f"\nWelcome {player}, let's play a game!")print("I am thinking of a number between 1 and 100. Can you guess it?")
Step 2: Starting the game with while loop. The game will continue until the player guesses the number. The player has to guess the number, and the program should give feedback if the guess is too high or too low, using if statements.while guess != random_number: guess = int(input("\nTake a guess: ")) if guess > random_number: print("Too high, try again!") elif guess < random_number: print("Too low, try again!")
Step 3: Printing the output If the player guesses the number, the program will end with a message thanking the person for playing and displaying "Game Over".print("\nCongratulations, you guessed the number!")print(f"Thank you for playing, {player}!")print("Game Over")
Step 4: FlowchartPlease see the attached file for the flowchart.
To learn more about flowchart:
https://brainly.com/question/31697061
#SPJ11
Which of the following is not one of the ranges of IP addresses defined in RFC 1918 that are commonly used behind a NAT server?
a. 192.168.0.1 - 192.168.255.254
b. 172.16.0.1 - 172.31.255.254
c. 10.0.0.1 - 10.255.255.254
d. 169.254.0.1 - 169.254.255.254
Answers
The correct answer is option d. 169.254.0.1 - 169.254.255.254 is not one of the ranges of IP addresses defined in RFC 1918 used in a NAT server.
How to find which range of IP addresses are not used behind NAT server?Options a, b, and c are all part of the private IP address ranges defined in RFC 1918.
These ranges are reserved for private networks and are not routable on the public internet.
Option d, on the other hand, is the range reserved for Automatic Private IP Addressing (APIPA), which is a feature used by some operating systems when they are unable to obtain an IP address from a DHCP server.
It is not typically used for private networks behind a NAT server.
Therefore, 169.254.0.1 - 169.254.255.254 is not one of the ranges of IP addresses defined in RFC 1918 that are commonly used behind a NAT server.
Learn more about IP addresses
brainly.com/question/31026862
#SPJ11
what is a compter crime?
Answers
Answer:
Cy***rcrime, also called computer cr**me, the use of a computer as an instrument to further illegal ends, such as committing fr4ud, traf**icking in child por****graphy and intellectual property, stealing id
Individuals are taught how to avoid falling prey to cybercriminals through
End-user education
Cybercrime
Good practice continuity
Network security
Answers
Answer:
I think it's End_user education
Explanation:
A. End - User Education
its Correct.
ome people argue that we can consider the whole address space as one single block in which each range of addresses is a sub-block to this single block. Elaborate on this idea. What happens to sub netting if we accept this concept? (5 Marks)
Answers
The idea that the whole address space can be considered as one single block, with each range of addresses as a sub-block, is referred to as "supernetting" or "classless inter-domain routing" (CIDR). If we accept this concept, sub-netting becomes more flexible and efficient as it allows for the allocation of variable-sized address blocks, enabling better address space utilization.
In traditional subnetting, IP addresses were divided into fixed-sized blocks, such as Class A, Class B, and Class C networks. This led to inefficient utilization of address space as organizations were assigned blocks larger than what they actually needed, resulting in address wastage.
With supernetting or CIDR, the address space is viewed as a single block, and addresses are allocated based on the actual requirements of each organization. Subnets can be created with varying sizes, allowing for more efficient utilization of addresses. This flexibility in address allocation leads to better management of IP addresses and helps address the issue of address exhaustion.
In summary, accepting the concept of considering the entire address space as one single block allows for supernetting or CIDR, which enhances the flexibility and efficiency of address allocation. It leads to better address space utilization and helps mitigate the problem of address exhaustion.
You can learn more about sub-netting at
https://brainly.com/question/28256854
#SPJ11
Please show work with excel formulas
Esfandairi Enterprises is considering a new three-year expansion project that requires an initial fixed asset investment of \( \$ 2.18 \) million. The fixed asset will be depreciated straightline to z
Answers
The annual straight-line depreciation expense for the fixed asset is $726,667.
To calculate the annual straight-line depreciation expense, we need to divide the initial fixed asset investment by the useful life of the asset. In this case, the initial fixed asset investment is $2.18 million and the project's duration is three years.
Using the straight-line depreciation method, the annual depreciation expense is determined by dividing the initial investment by the useful life:
Depreciation Expense = Initial Investment / Useful Life
Depreciation Expense = $2,180,000 / 3
Depreciation Expense = $726,667
This means that Esfandairi Enterprises can expect an annual depreciation expense of $726,667 for the three-year duration of the project.
Learn more about fixed asset
brainly.com/question/14392032
#SPJ11
matt is supervising the installation of redundant communications links in response to a finding during his organization's bia. what type of mitigation provision is matt overseeing?
Answers
The type of mitigation provision is matt overseeing is installing a redundant computer system.
What is mitigation provision?
A mitigation provision is a clause in a contract that requires one party to take reasonable steps to mitigate damages that may be caused by the other party's breach of the contract. Under the code's mitigation provisions, a bar to an assessment, credit, or refund imposed by the expiration of a statute of limitations or other rule of law can be waived.
Matt is overseeing the installation of redundant communications links in response to a finding during his organization's business impact analysis (BIA). This is an example of proactive mitigation, which is activity taken in advance of an incident to reduce its potential severity.
To learning more about mitigation provision
https://brainly.com/question/28138888
#SPJ4
What two names are given to UDP blocks of communication?
Answers
The two names given to UDP blocks of communication are datagrams and packets.
Datagram refers to a self-contained unit of data that is transmitted over a network and contains all the necessary information for its delivery, including source and destination addresses. It is a fundamental component of the User Datagram Protocol (UDP) that provides an unreliable, connectionless service for transmitting datagrams between network hosts.
A packet, on the other hand, is a similar unit of data that is used in various network protocols, including UDP and TCP (Transmission Control Protocol). A packet contains not only the data to be transmitted but also additional information such as header information, error detection codes, and other control information necessary for its successful transmission and reception. Unlike datagrams, packets can be guaranteed to arrive at their destination, as they are transmitted using connection-oriented protocols like TCP that ensure their reliable delivery.
In summary, datagrams and packets are both essential units of data used in network communication, with datagrams being used in connectionless, unreliable protocols like UDP, and packets being used in connection-oriented protocols like TCP. Understanding the differences between these terms is crucial for network engineers and administrators to effectively manage and troubleshoot network issues.
know more about User Datagram Protocol here:
https://brainly.com/question/20038618
#SPJ11
which of the following types of constraints is used to enforce referential integrity?
Answers
The type of constraint used to enforce referential integrity is the Foreign Key constraint. The purpose of foreign key constraints is to ensure that the values in the foreign key column(s) match the values in the referenced primary key column(s).
A foreign key is a column or a set of columns in a database table that refers to the primary key of another table. It establishes a relationship between two tables, where the values in the foreign key column(s) must match the values in the referenced primary key column(s).
By defining a foreign key constraint, you ensure that the values in the foreign key column(s) of a table are valid and exist in the referenced primary key column(s) of another table.
This constraint helps maintain data integrity and prevents inconsistencies or orphaned records in relational databases. So foreign key is used to enforce the referential integrity.
To learn more about referential integrity: https://brainly.com/question/17128955
#SPJ11
Northern trail outfitters has the case object set to private. the support manager raised a concern the reps have a boarder view of data than expected and can see all cases on their groups dashboards. what could be causing reps to have inappropriate access to data on dashboards
Answers
The option that could be causing reps to have inappropriate access to data on dashboards is known to be Dynamic Dashboards.
What is a Dynamic dashboards?Dynamic dashboards is known to be a tool that helps all user to be able to view the data they are known to have access to.
Note that in the case above about Northern trail outfitters, the option that could be causing reps to have inappropriate access to data on dashboards is known to be Dynamic Dashboards.
see options below
Northern Trail Outfitters has the Case object set to private. The support manager raised a concern that reps have a broader view of data than expected and can see all cases on their group's dashboards.
What could be causing reps to have inappropriate access to data on dashboards?
A. Public Dashboards
B. Dashboard Subscriptions
C. Dynamic Dashboards
D. Dashboard Filters
Learn more about Dashboards from
https://brainly.com/question/1147194
#SPJ1
Which of the following is NOT an example of soft skill?
A- leadership
B- Creativity
C- Computer programming skills
D- Time management

Answers
What are some innovative research ideas for Onshore/Offshore hybrid wind turbines?
I was thinking whether it could be integrated with AI technologies, Pv Cells, thermoelectric plates, piezoelectric etc etc
please give me some inspirations
Answers
Some innovative research ideas for onshore/offshore hybrid wind turbines include integrating AI technologies for advanced control and optimization, incorporating PV cells for hybrid energy generation, utilizing thermoelectric plates for waste heat recovery, and exploring the potential of piezoelectric materials for vibration energy harvesting.
One innovative research idea is to integrate AI technologies into onshore/offshore hybrid wind turbines. AI algorithms can be used to optimize turbine performance by analyzing real-time data and making adjustments to maximize energy production and efficiency. AI can also enable predictive maintenance, allowing for proactive identification of potential issues and minimizing downtime.
Another idea is to incorporate photovoltaic (PV) cells into the hybrid wind turbines. By combining wind and solar energy generation, these turbines can generate power from both sources, maximizing energy output and improving the overall reliability and stability of the system.
Additionally, exploring the use of thermoelectric plates in hybrid wind turbines can enable the recovery of waste heat generated by the turbine. This waste heat can be converted into electricity, enhancing the overall energy efficiency of the system.
Furthermore, researchers can investigate the application of piezoelectric materials in hybrid wind turbines for vibration energy harvesting. These materials can convert mechanical vibrations caused by wind turbulence into electrical energy, supplementing the power output of the turbine.
These innovative research ideas highlight the potential for integrating AI technologies, PV cells, thermoelectric plates, and piezoelectric materials into onshore/offshore hybrid wind turbines to enhance their performance, energy generation capabilities, and efficiency.
Learn more about AI technologies here:
https://brainly.com/question/30089143
#SPJ11
a network requires at least three computers and a shared resource. group of answer choices true false
Answers
True. A network requires at least three computers and a shared resource.
In order to establish a network, a minimum of three computers and a shared resource are necessary. A network enables the computers to communicate and share information, files, or services with each other. The shared resource could be a printer, a file server, an internet connection, or any other component that can be accessed and utilized by multiple computers within the network. Having at least three computers allows for connectivity and interaction between multiple nodes, creating a networked environment where data can be transmitted and shared.
Learn more about network here:
https://brainly.com/question/29350844
#SPJ11
Choose the words that complete the sentences.
A_______
is used to edit raster images.
A_______
is used to edit vector images.
A_______
is used to control a scanner or digital camera.
Answers
Answer:
A paint application
is used to edit raster images.
A drawing application
is used to edit vector images.
A digitizing application
is used to control a scanner or digital camera.
Explanation:
got it right on edg
my baby's always dancin' and it wouldn't be a bad thing
But I don't get no loving and that's no lie
We spent the night in Frisco at every kinda disco
From that night I kissed our love goodbye
Don't blame it on the sunshine
Don't blame it on the moonlight
Don't blame it on the good times
Blame it on the boogie
Don't blame it on the sunshine
Don't blame it on the moonlight
Don't blame it on the good times
Blame it on the boogie
That nasty boogie bugs me, but somehow how it has drugged me
Spellbound rhythm gets me on my feet
I've changed my life completely, I've seen the lightning leave me
And my baby just can't take her eyes off me
Don't blame it on the sunshine
Don't blame it on the moonlight
Don't blame it on the good times
Blame it on the boogie
Don't you blame it on the sunshine
Don't blame it on the moonlight
Don't blame it on the good times
Blame it on the boogie, woo
I just can't, I just can't
I just can't control my feet
I just can't, I just can't
I just can't control my feet
I just can't, I just can't
I just can't control my feet
I just can't, I just can't
I just can't control my feet
Sunshine
Don't blame it on the moonlight
Don't blame it on the good times
Blame it on the boogie
Don't blame it on the sunshine
Don't blame it on the moonlight
Don't on the good times
Blame it on the boogie
This magic music grooves me, that dirty rhythm fools me
The Devil's gotten to me through this dance
I'm full of funky fever, a fire burns inside me
Boogie's got me in a super trance
Don't blame it on the sunshine
Don't blame it on the moonlight
Don't blame it on the good times
Blame it on the boogie
Don't you blame it sunshine
Don't blame it on the moonlight
Don't blame it on the good times
Blame it on the boogie
Aow!
Sunshine
Hoo!
Moonlight
Yeah
Good times
Mmm!
Boogie
You just gotta sunshine
Yeah
Moonlight
Good times
Good times
Boogie
Don't you blame it sunshine
You just gotta moonlight
You just wanna good times
Yeah, oh boogie
Blame it on yourself
(Sunshine)
Ain't nobody's fault
(Moonlight)
But yours and that boogie
(Good times)
All night long
(Boogie)
Can't stop that boogie
(Sunshine)
Ain't nobody's fault
(Moonlight)
But yours and that boogie
(Good times)
Dancin' all night long
(Boogie)
Blame it on yourself
(Sunshine)
Ain't nobody's fault
(Moonlight)
But yours and that boogie, boogie, boogie
Answers
Answer: This isn't even a question.
Explanation: I have no idea how to answer these song lyrics.
A video conferencing application isn't working due to a Domain Name System (DNS) port error. Which record requires modification to fix the issue?
Answers
Answer:
Service record (SRV)
Explanation:
Service records (SRV record) are data records stipulating specifications of the DNS such as the port numbers, servers, hostname, priority and weight, and IP addresses of defined or cataloged services servers.
The SRV record is the source of information and the search site about the
location of particular services as such an application i need of such services will look for a related SRV record
A configured SRV is the source of the ports and personal settings for a new email client, without which the parameters set in the email client will be incorrect.
which is the best software program
Answers
Answer:
The question "which is the best software program" is quite broad, as the answer can depend on the context and what you're specifically looking for in a software program. Software can be developed for a myriad of purposes and tasks, including but not limited to:
- Word processing (e.g., Microsoft Word)
- Spreadsheet management (e.g., Microsoft Excel)
- Graphic design (e.g., Adobe Photoshop)
- Video editing (e.g., Adobe Premiere Pro)
- Programming (e.g., Visual Studio Code)
- 3D modeling and animation (e.g., Autodesk Maya)
- Database management (e.g., MySQL)
- Music production (e.g., Ableton Live)
The "best" software often depends on your specific needs, your budget, your experience level, and your personal preferences. Therefore, it would be helpful if you could provide more details about what kind of software you're interested in, and for what purpose you plan to use it.
undefined operator '*' for input arguments of type 'function_handle'
Answers
Answer:
Explanation:
It seems you are encountering an error due to using the multiplication operator (*) with input arguments of type 'function_handle'. This error occurs because the '*' operator is not defined for function handles.
To resolve this issue, you should evaluate the functions using their respective input arguments first, and then apply the '*' operator to the resulting values.
To know more about the operator click here:
https://brainly.com/question/31932456
#SPJ11
Don is creating a very long document, and he would like to create an introductory page that contains the title of the document and the name of the author along with the date.
Answers
Answer:
This is a very good choice, to do so Don can insert a cover page. He can go to the options menu, pick the "insert" lash, and then to the "pages" square in the far left of the toolbox. There he will find a "cover page" section that will automatically add a cover page at the beginning of the document.
Explanation:
The reasons for this answer are that in the first place, it is very difficult to go o the first page of the document and move everything down because the format would be lost. Then, he would require to edit everything. It would also result in the same in case he only added a white page and started writing. So he needs a specific object that wouldn't damage the format if edited on the first page.
A(n) __________ structure is a structure that causes a statement or a set of statements to execute repeatedly.
Answers
Answer:
you cant do anything with the start of the question unless you explained more about it
Explanation:
Signalling and Communication railway
Q5 (a) Justify the importance of the Telecommunication System and figure out the general telecommunication network architecture inclusive of the main sub-systems. (10 marks)
Answers
The Telecommunication System plays a crucial role in the railway industry, providing essential communication services for efficient and safe operations.
The general telecommunication network architecture in railways consists of several main sub-systems. Firstly, the Backbone Transmission Network (BTN) serves as the backbone infrastructure, providing high-capacity and reliable communication links across the railway network. It enables the transmission of voice, data, and video signals between different locations, including signaling systems, train control centers, and operational management centers. Secondly, the Radio System (RS) ensures wireless communication within the railway system. It allows for clear and instant voice communication between train operators, dispatchers, and other railway staff. The RS provides coverage across the railway network, utilizing dedicated frequency bands and protocols to maintain reliable communication integrity. Additionally, the Public Address System delivers important announcements and messages to passengers and staff within railway stations and trains. It utilizes speakers, amplifiers, and control panels to broadcast clear and intelligible audio information, ensuring effective communication with passengers and facilitating smooth operations. Overall, the Telecommunication System and its network architecture are vital components of the railway industry, enabling seamless communication, enhancing operational safety, and improving the passenger experience.
Learn more about [telecommunication systems ] here:
https://brainly.com/question/29685173
#SPJ11
¿como la imagen organiza la realidad?
Answers
Answer:
Las imágenes son las percepciones visuales que las personas tienen respecto de la realidad que los rodea. Así, a través de la visión, las personas pueden interpretar el contexto en el cual se encuentran inmersos, organizando los distintos componentes de la realidad en la cual desarrollan sus vidas, para poder comprender entonces de qué modo proceder ante las diferentes eventualidades de la vida.
Es decir que, a través de las imágenes, y en conjunto con las demás percepciones sensoriales, los seres humanos pueden contextualizarse en un entorno en el cual se desenvuelven, organizando su vida y su realidad a futuro.