if you are using the bubble sort algorithm to sort an array in descending order, the smaller values move toward the endT/F
Answers
False. In the bubble sort algorithm, the larger values "bubble" towards the end of the array, as in each iteration, adjacent elements are swapped if they are in the wrong order.
In the bubble sort algorithm, the array is sorted in ascending order by default, but it can be modified to sort in descending order. The algorithm works by repeatedly comparing adjacent elements and swapping them if they are in the wrong order. When sorting in descending order, the larger values will gradually "bubble" towards the beginning of the array. This is because in each iteration, if an adjacent pair is found in the wrong order (with the smaller element appearing before the larger element), they are swapped. This process continues until the array is fully sorted in descending order, with the larger values positioned towards the beginning.
Learn more about bubble sort algorithm here:
https://brainly.com/question/13161938
#SPJ11
Related Questions
BIm computer class I need answers please

Answers
Answer:
I think the 3RD
Explanation:
The reason why I think that is because the other once are not written correctly.
Explanation: For formal letters, you always want to write out the entire date, including the full month.
unless implemented by iframe as non script, the tag tester tool browser icon will activate only on pages with the tag manager implemented.falsetrue
Answers
It is false that unless implemented by iframe as non script, the tag tester tool browser icon will activate only on pages with the tag manager implemented.
The tag tester application A browser icon, sometimes known as a tag debuger or tag inspector, is a functionality that some browser extensions or development tools provide.
Its primary goal is to assist developers and marketers in debuging and analysing the tags and scripts used on a webpage.
The presence of a tag management implementation on a webpage does not affect the activation of the tag tester tool browser icon.
Browser extensions or developer tools often give the tag tester tool browser icon, which allows users to analyse and debug tags and scripts running on a webpage. It has nothing to do with the presence or deployment of a tag management.
Thus, the given statement is false.
For more details regarding browser, visit:
https://brainly.com/question/19561587
#SPJ4
What are 3 similarities and 3 differences between live theatre and film/videos -Drama Class
Answers
1. Theatre is live. Film has been captured in the past. We only see after the making process is done.
2.You have chance for improvement in each theatre shows but its impossible in Films. Once film is done its done.
3.Normally Theatre is cheaper, films are costly.
Similarities-
1.Theatre and films both are arts, so many varieties of arts melt into theatre or film to make it happen.
2.Theatre and films both are very effective medium of communication.
3.Theatre and films both are considered as great form of Entertainment.
Which of these jobs would be most appropriate for someone who majors in information systems? A. Managing a group of programers B. Creating a cloud based customer service application app C. Providing telephone tech support D. Designing a database for an online retailer.
Answers
Answer:
B. Creating a cloud based customer service application app
Explanation:
Information Systems is described as an "academic study of various systems encompassing a particular reference associated with the complementary networks and information of the software and hardware that different organizations and people use to collect, create, process, distribute, and filter data.
The information system includes an integrated pair of different components for storing, collecting, and processing data, along with this, it is utilized for providing knowledge, information, and digital products.
In the question above, the correct answer is option-B.
cloudy computing would like to allow users to relate records to other records of the same object. what type of relationship is this?
Answers
Cloud computing would like to allow users to relate records to other records of the same object by using a Self-relationship.What is Cloud Computing Cloud computing is the on-demand availability of computer resources, particularly data storage and computing power, without direct user management.
In layman's terms, this implies that any individual can access computer resources from any location with internet access, making it possible to create a single, central repository of information that can be accessed by multiple users in real-time.
This provides the user with a platform for easy access to computing power and the storage of information. The use of cloud computing technology eliminates the need for costly and complex hardware and infrastructure for businesses and organisations.
To know more about computing visit:
https://brainly.com/question/32297638
#SPJ11
1)Which tool can you use to find duplicates in Excel?
Select an answer:
a. Flash Fill
b. VLOOKUP
c. Conditional Formatting
d. Concatenation
2)What does Power Query use to change to what it determines is the appropriate data type?
Select an answer:
a.the headers
b. the first real row of data
c. data in the formula bar
3)Combining the definitions of three words describes a data analyst. What are the three words?
Select an answer:
a. analysis, analyze, and technology
b. data, programs, and analysis
c. analyze, data, and programs
d. data, analysis, and analyze
Answers
The tool that you can use to find duplicates in Excel is c. Conditional Formatting
b. the first real row of datac. analyze, data, and programsWhat is Conditional Formatting?Excel makes use of Conditional Formatting as a means to identify duplicate records. Users can utilize this feature to identify cells or ranges that satisfy specific criteria, like possessing repetitive values, by highlighting them.
Using conditional formatting rules makes it effortless to spot repeated values and set them apart visually from the other information. This function enables users to swiftly identify and handle identical records within their Excel worksheets, useful for activities like data examination and sanitation.
Read more about Conditional Formatting here:
https://brainly.com/question/30652094
#SPJ4
You need to replace the motherboard on a laptop. Which two items should you disconnect or remove first
Answers
The process of giving the user the result of processing is called
Answers
Your question is answered output.
Output is a state when computer completed at processing the user's wants or inputted data. Your smartphone display, speaker is an output device, even it's not a big computer.
Hope this helps :)
There is a feature that allows you to lock the document, to avoid others making changes. t/f
Answers
Answer:
true
Explanation:
i have the same class
Answer:true
Explanation:
I took the test and it was correct
A _____ is a block of code containing standard SQL statements and procedural extensions that is stored and executed at the DBMS server.
Answers
Answer:
Persistent Stored Module (PSM).
Explanation:
Which code is easier to learn, Python or C++. And which one is better than the other in your opinion
Answers
when a process is reading/writing a memory location (i.n. a variable), can other processes read or modify the same memory location?
Answers
It is important for programmers to understand the concurrency model of their chosen language and platform and use appropriate synchronization techniques to ensure safe access to shared memory locations.
It depends on the specific programming language and operating system being used. In some cases, other processes may be able to read or modify the same memory location, leading to potential data integrity issues and race conditions. However, many modern programming languages and operating systems provide mechanisms such as locks and semaphores to prevent multiple processes from accessing the same memory location simultaneously, ensuring data consistency and preventing conflicts. When a process is reading/writing a memory location (e.g., a variable), other processes can potentially read or modify the same memory location. However, this can lead to issues such as race conditions or data inconsistency. To prevent these problems, mechanisms like mutual exclusion and synchronization techniques are used to ensure safe and accurate access to shared memory.
Learn more about synchronization techniques here:
https://brainly.com/question/27906996
#SPJ11
give me rationale about brake system???
Answers
The brake system in a vehicle plays a critical role in ensuring safety, control, and efficient operation.
Here are some rationales for the importance of a well-designed and functioning brake system:
1)Safety: The primary purpose of the brake system is to provide reliable and efficient stopping power, allowing the driver to slow down or bring the vehicle to a complete stop when necessary.
A properly functioning brake system is crucial for avoiding accidents, preventing collisions, and protecting the driver, passengers, and others on the road.
2)Control and Handling: A well-designed brake system enhances the driver's control over the vehicle.
It enables smooth deceleration and allows for precise modulation of braking force, providing better handling and maneuverability.
This allows the driver to respond to changing road conditions, traffic situations, and emergencies effectively.
3)Energy Conversion: The brake system converts kinetic energy into thermal energy through friction, allowing the vehicle to reduce its speed or stop.
This energy conversion process is essential for managing the vehicle's speed and preventing excessive heat buildup in the braking components.
4)Performance and Responsiveness: An efficient brake system ensures prompt response and reliable performance, allowing the driver to trust the brakes when needed.
It should provide consistent braking force, even under different driving conditions such as wet or slippery surfaces.
A well-designed brake system improves the overall driving experience by instilling confidence and predictability in the braking process.
5)Maintenance and Longevity: Regular maintenance of the brake system, including inspections, pad and rotor replacements, and fluid flushes, is crucial for its longevity and optimal performance.
A properly maintained brake system minimizes the risk of component failure, extends the lifespan of brake components, and reduces the chances of costly repairs.
For more questions on brake system
https://brainly.com/question/30262553
#SPJ8
Please help with this error message

Answers
This likely has nothing to do with your for loop. Before we get into the error, let's discuss arguments.
Your methods are given arguments when you declare them. For instance, your shuttle method has two arguments.
public void shuttle(int spaces, int beepers){
}
spaces and beepers are the two arguments. When you call these methods, for instance,
shuttle();
You must include the arguments.
shuttle(1,2);
You have these errors because you're not supplying the methods with arguments.
please give me a answer correctly

Answers
Answer:
C. Bob (Robert) Gaskins.
A. The selected cell.
C. The title box.
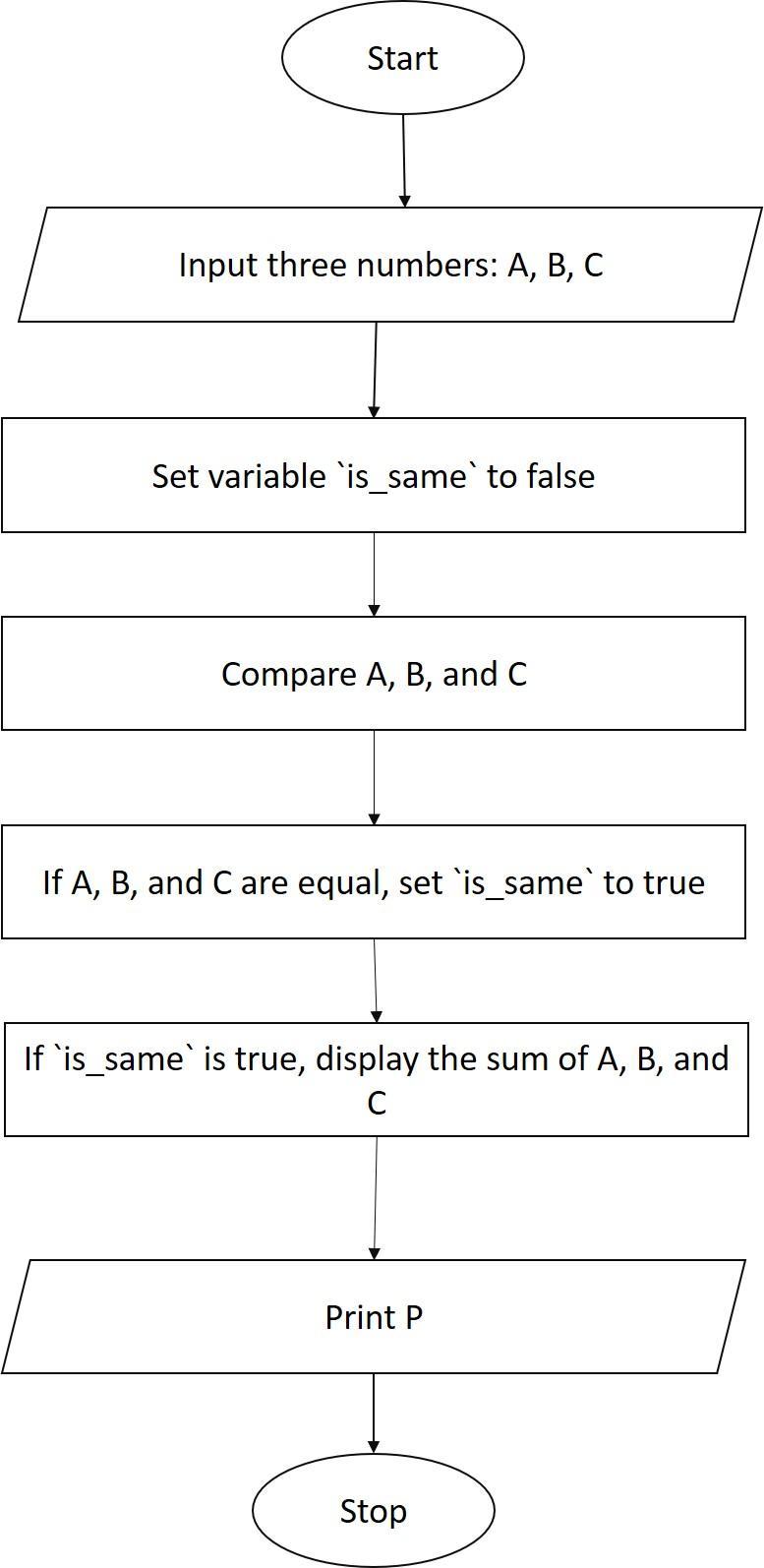
Draw the flowchart to accept three numbers check if they are same then display sum otherwise display product
Answers
The required flow chart is depcied as follows
Start
Input three numbers, A,B, and C
Compare A, B, and C
If A, B, and C are the same, then
Display the sum of A, B, and C
Else
Display the product of A, B, and C
End
What is the explanation for the above?The program starts by inputting three numbers, A, B, and C.
The program then compares A, B, and C.
If A, B, and C are the same, then the program displays the sum of A, B, and C.
Otherwise, the program displays the product of A, B, and C.
The program ends.
Learn more about Flow Chart at:
https://brainly.com/question/6532130
#SPJ1
a binary mixed-integer programming problem in which the binary variables represent whether an activity, such as a production run, is undertaken or not is known as the a. fixed-cost problem. b. covering problem. c. share of choice problem. d. capital budgeting problem.
Answers
A binary mixed-integer programming problem in which the binary variables represent whether an activity, such as a production run, is undertaken or not is known as the fixed-cost problem (option a). In a fixed-cost problem.
the decision variables are binary, indicating whether to perform an activity or not. These decisions often involve incurring a fixed cost if the activity is chosen to be undertaken. Examples of fixed costs include the setup cost for a production line, the cost of opening a facility, or the mixed integer cost of initiating a project. The objective of the fixed-cost problem is to minimize the total cost, which includes both fixed and variable costs, while meeting specific requirements or constraints. Fixed-cost problems are widely used in operations research, supply chain management, and other areas of optimization, and are an important category of binary mixed-integer programming problems.
The formal name of this problem is the (linear) integer-programming problem. When some decision variables—but not all—must be made up of integers, the programme is said to fall under the category of a mixed integer programme. A programme is referred to as a pure integer programme when every variable utilised to make decisions must be an integer. A crucial special circumstance is when a decision variable, X1, at the instant of resolution can only be either 0 or 1. These variables, also known as 0-1 or binary integer variables, can be used to mimic yes-or-no decisions, like building a plant or buying a piece of machinery.
Learn more about mixed-integer here
https://brainly.com/question/31759821
#SPJ11
match each artificial intelligence (ai) technique with its definition. - represent the knowledge of experts as a set of rules that can be programmed so that a computer can assist human decision makers. - software that can identify patterns in very large databases without explicit programming although with significant human training. - loosely based on human neurons, algorithms that can be trained to classify objects into known categories based on data inputs. - algorithms based loosely on evolutionary natural selection and mutation, commonly used to generate high-quality solutions to optimization and search problems. - algorithms that make it possible for a computer to understand and analyze natural human language. - systems that can view and extract information from real-world images. - use of machines that can substitute for human movements as well as computer systems for their control and information processing. - software agents that use built-in or learned knowledge to perform specific tasks or services for an individual. a. robotics b. computer vision systems c. neural networks d. genetic algorithms e. natural language processing f. machine learning g. intelligent agents h. expert systems
Answers
The top AI methods—heuristics, natural language processing, artificial neural networks, machine learning, support vector machines, and markov decision processes—will be covered in this essay.
How does artificial intelligence work?
The replication of human intelligence functions by machines, particularly computer systems, is known as artificial intelligence. Expert systems, natural language processing, speech recognition, and machine vision are some examples of specific AI applications.
What fundamental principle underpins artificial intelligence?
Artificial intelligence is founded on the idea that human intelligence can be described in a way that makes it simple for a computer to duplicate it and carry out activities of any complexity. Artificial intelligence aims to emulate cognitive processes in humans.
To know more about Artificial intelligence visit;
https://brainly.com/question/23824028
#SPJ4
If you Buy my group clothing in R.o.b.l.o.x for a donation i will make you brainliest
My group is One Percenters
Answers
Answer:kk ima do it
Explanation:
Answer:
this and that
Explanation:
this and that
IT WORKSHEET FOR GRADE 7 STUDENT'S PART L WRITE TRUE IF THE STATEMENT IS CORRECT AND FALSE IF IT IS L 1. It is not mandatory to unplug power cable from the main powe cleaning a computer I need help
Answers
False. It is mandatory to unplug the power cable from the main power before cleaning a computer to prevent electrical shock or damage to the components.
What is the explanation for the above response?The statement "It is not mandatory to unplug the power cable from the main power when cleaning a computer" is false. It is important to unplug the power cable from the main power before cleaning a computer because it can prevent electrical shock or damage to the computer's components.
If the power is still connected, there is a risk of electric shock from accidental contact with live components. Also, cleaning the computer while it's powered on may also lead to damage or data loss due to electrostatic discharge or accidental spills.
Learn more about computers at:
https://brainly.com/question/21047147
#SPJ1
You have two Windows Server 2016 computers with the Hyper-V role installed. Both computers have two hard drives, one for the system volume and the other for data. One server, HyperVTest, is going to be used mainly for testing and what-if scenarios, and its data drive is 250 GB. You estimate that you might have 8 or 10 VMs configured on HyperVTest with two or three running at the same time. Each test VM has disk requirements ranging from about 30 GB to 50 GB. The other server, HyperVApp, runs in the data center with production VMs installed. Its data drive is 500 GB. You expect two VMs to run on HyperVApp, each needing about 150 GB to 200 GB of disk space. Both are expected to run fairly disk-intensive applications. Given this environment, describe how you would configure the virtual disks for the VMs on both servers.
Answers
The virtual disk configuration for the VMs on both servers in this environment is shown below.
In the Hyper V Test,
Since there will be two or three virtual machines running at once, each of which needs between 30 and 50 GB of the total 250 GB of disk space available,
What is virtual disks?Setting up 5 virtual disks, each 50 GB in size.
2 VMs each have a 50 GB virtual drive assigned to them.
The above setup was chosen because running three VMs with various virtual disks assigned to them will not pose an issue when two or three VMs are running concurrently and sharing the same virtual disk. This is because the applications are disk-intensive.
To learn more about virtual disks refer to:
https://brainly.com/question/28851994
#SPJ1
Given this environment, the virtual disk configuration for the VMs on both servers is shown below. Because two or three VMs will be running at the same time, and each VM has disk requirements ranging from 30 to 50 GB of total disk space of 250 GB.
What is Hyper V Test?While there are several methods for testing new virtual machine updates, Hyper-V allows desktop administrators to add multiple virtual machines to a single desktop and run tests. The Hyper-V virtualization technology is included in many versions of Windows 10. Hyper-V allows virtualized computer systems to run on top of a physical host. These virtualized systems can be used and managed in the same way that physical computer systems can, despite the fact that they exist in a virtualized and isolated environment. To monitor the utilization of a processor, memory, interface, physical disk, and other hardware, use Performance Monitor (perfmon) on a Hyper-V host and the appropriate counters. On Windows systems, the perfmon utility is widely used for performance troubleshooting.Therefore,
Configuration:
Creating 5 Virtual disks of 50 GB each.
1 virtual disk of 50 GB is assigned to 2 VM.
The above configuration is because since two or three VM will be running at the same time and using the same virtual disk will cause a problem since the applications are disk intensive, running three VMs with different virtual disks assigned to them, will not cause a problem.
For Hyper V App,
Two VM will run at the same time, and the disk requirement is 150 - 200 GB of 500 GB total disk space.
Configuration:
Creating 2 virtual disks of 200 GB each with dynamic Extension and assigning each one to a single VM will do the trick.
Since only two VMs are run here, the disk space can be separated.
To learn more about Hyper V Test, refer to:
https://brainly.com/question/14005847
#SPJ1
which is always true about java classes? a. a class can implement only one interface b. a class can extend from multiple classes c. an interface can implement multiple classes d. a class can implement multiple interfaces e. none of the above
Answers
The correct statement about Java classes is that a class can implement multiple interfaces. This means that a class can provide implementation for multiple sets of behaviors or functionalities defined by different interfaces.
However, a class can only extend from a single class in Java, which means it can inherit and reuse the properties and methods of only one parent class. This is because Java does not support multiple inheritance of classes to avoid the complexities and ambiguities that may arise from it. On the other hand, an interface in Java can only extend from one or more interfaces but cannot implement any class. It defines a contract of methods that a class implementing it must implement. Therefore, the correct option is d. a class can implement multiple interfaces. The other options are incorrect.
Learn more about Java here-
https://brainly.com/question/31561197
#SPJ11
still consider using anomaly detection for intrusion detection. let's analyze a case. suppose alice's computer has 4 files (not realistic but for easy calculation...), and here are some data:
Answers
It is still recommended to use anomaly detection for intrusion detection. Anomaly detection is a method used in intrusion detection systems to identify unusual behavior that could be indicative of a security breach. It involves monitoring network traffic and system activity for any patterns or behaviors that deviate from the norm.
By identifying these anomalies, security analysts can investigate and respond to potential threats before any damage is done. In the case of Alice's computer, let's say she has four files. Using anomaly detection, her system activity would be monitored for any unusual behavior such as attempts to access or modify files that are not normally accessed, or connections to unknown or suspicious IP addresses.
If such behavior is detected, an alert is triggered, and security analysts can investigate the source of the anomaly to determine if it is a legitimate threat or a false positive. Anomaly detection is particularly useful in detecting zero-day attacks, which are previously unknown exploits that have not yet been identified by signature-based detection methods. Overall, anomaly detection is an important tool in an organization's security arsenal, and should be used in conjunction with other security measures such as firewalls, antivirus software, and intrusion prevention systems. Anomaly detection is a proactive approach to security that involves monitoring system activity for any deviations from the norm. It is used to identify potential security threats that may not be detected by traditional signature-based methods. By using anomaly detection, organizations can detect and respond to security breaches before they cause any significant damage. In the case of Alice's computer, anomaly detection would be used to monitor her system activity for any unusual behavior that could be indicative of a security breach Yes, anomaly detection can be used for intrusion detection in this case. Anomaly detection is a technique used to identify unusual patterns or behaviors that deviate from the norm. In the context of intrusion detection, it can help identify potential threats or intrusions on Alice's computer by analyzing the activities related to her 4 files. Establish a baseline: First, we need to create a baseline of normal activities or behaviors for Alice's computer. This could include file access patterns, file modifications, and network activities.
To know more about detection visit:
https://brainly.com/question/28284322
#SPJ11
Kai recently graduated from college with a dual degree—a Bachelor’s in Game Design and Development and a Bachelor’s in Music. The goal is to find a job that will use both degrees, and there is an interview at a video game design studio tomorrow. Kai would love to be in charge of planning, authoring, and implementing the soundscape for games, including sound effects, music, and dialogue. What role at the video game studio would be a good fit?
character rigger
audio designer
artificial intelligence programmer
cinematic artist
Answers
Audio designers plan , sound effects, music and pretty much anything that has to do with sound in a video game
why is it important to put specific conditionals first?
Answers
Answer:
i dunno
Explanation:
Answer:
Explanation:
First conditional is used to talk about actions/events in the future which are likely to happen or have a real possibility of happening. If it rains tomorrow, I'll stay at home.
Which type of network activities are handled by the presentation layer of the osi model?
Answers
The presentation layer of the OSI model is responsible for managing the formatting and encryption of data exchanged between applications. It handles network activities such as data translation, compression, encryption, and decryption.
Here are some specific network activities handled by the presentation layer:
1. Data formatting: The presentation layer ensures that data is presented in a format that is understandable by the receiving application. For example, it may convert data from ASCII to Unicode or vice versa.
2. Data compression: The presentation layer compresses data to reduce the amount of data that needs to be transmitted over the network. This can help improve network performance and reduce bandwidth usage.
3. Encryption and decryption: The presentation layer can encrypt data before sending it over the network and decrypt it at the receiving end. This ensures data confidentiality and security during transmission.
4. Data syntax validation: The presentation layer checks the syntax and structure of data to ensure it is correct and compatible with the receiving application.
In summary, the presentation layer of the OSI model handles activities such as data formatting, compression, encryption, decryption, and syntax validation to ensure smooth communication between applications.
To know more about network activities visit:
https://brainly.com/question/27629086
#SPJ11
do you think you have the qualities of an enterpreneur in you? If yes, give examples when you have shown these qualities.
Answers
The quality that all successful entrepreneurs must possess is determination and the ability to take action. They have to think and make decisions quickly and they discipline themselves to act and implement their decisions.
What is entrepreneurs?An entrepreneur is defined as a person who has the ability and desire to establish, manage and succeed in a start-up company with his own risks, in order to generate profit.
It is classified into the following types:
Small Business- Scaling of Initial Business Large Corporate Business Social Business5 Qualities of a Better Entrepreneur
Willingness to fail. Fear of failure is a common affliction.Critical Thinking. As the first trait, critical thinking enables entrepreneurs to move away from the herd mentality Clarity of Vision. Use yourself. Strong communication.Entrepreneurship accelerates economic growthEntrepreneurs are important for a market economy because they can act as the wheels of a country's economic growth. By creating new products and services, they increase new jobs, which ultimately leads to an acceleration of economic development.
To learn more about entrepreneurs, refer;
https://brainly.com/question/13897585
#SPJ9
If you think about designing a really complicated webpage with HTML, what are some challenges that you could face?
Answers
Answer:
Some challenges you could face when designing a really complicated web page with HTML are that the functions are different and if you don't know the code or there isn't any code for what you want to do you would need to find another way to get the result you want.
Explanation:
it's what i put down (i got it right so i hope this can help)
Answer:
I'm just here so the other person can get brainliest <3
Explanation:
Can somebody help me and make a code for this in PYTHON, please? I would be very thankful!
It is estimated that China on July 1, 2019. had 1,420,062,022 inhabitants, and India 1,368,737,513. The population in China increases by 0.35% every year, and in India by 1.08%. After how many years will India surpass China in terms of population, assuming that the annual population growth in neither of these two countries will change?
I think it should be used command FOR...
Answers
Code:
population_china = 1420062022
population_india = 1368737513
years = 0
while population_china >= population_india:
population_china *= 1.0035
population_india *= 1.0108
years += 1
print(years)
Output:
6
Explanation:
Using a while loop would probably be of greater use than a for loop since we are increasing the population growth of both countries until India's population surpasses China's population (so a condition needs to be set).
Looking at the code, we first set the original population of both countries in their own variables (population_china, population_india). We also set the 'years' variable at 0, which will increase with respect to the yearly population growths of both countries. In the while loop, the condition population_china >= population_india will allow for the variable 'years' to increase until population_india surpasses population_china. Once India's population is larger than China's population, we are left with the number of years it takes for India's population to surpass China's population, which is 6 years.
Hope this helps :)
Could someone please tell me what is the error in my code?
I'm trying to write a code for finding the cube of a number using C programming.

Answers
I think you have to remove the semicolon at the end of line 15. From what I see, this is not a logic error, rather than a syntax error.
Looking at the error on the bottom, it's expecting a '(' before the '{'.