What are examples of computer hardware
Answers
Answer:
Monitor
Motherboard
CPU (Microprocessor)
Main memory (RAM)
Expansion cards
Explanation:
Answer:mouse, keyboard, motherboard, CPU
Explanation:This is the right one ur looking for
Related Questions
How can i print an art triangle made up of asterisks using only one line of code. Using string concatenation (multiplication and addition and maybe parenthesis)?
Answers
#include <iostream>
int main(int argc, char* argv[]) {
//One line
std::cout << "\t\t*\t\t\n\t\t\b* *\t\t\b\n\t\t\b\b* *\t\t\b\b\n\t\t\b\b\b* *\t\t\b\b\b\n\t\t\b\b\b\b* *\t\t\b\b\b\b\n\t\t\b\b\b\b\b* * * * * *\t\t\b\b\b\b\b\n";
return 0;
}
Yes, it is possible with a single line and using escape sequences, but it is tedious and not recommended. Instead, you can use loops to write more readable and easy on the eyes code. We only used the cout method (C++). Good luck!

what is the main circuit board inside the computer called?
Answers
Answer:
Motherboard is the main circuit board inside the computer.
Select the correct answer from each drop-down menu.
Jeff writes a blog on digital photography. His most recent post was about visual artifacts. Identify the visual artifacts in the sentences below.
. A visual artifact of digital projectors is called
An inappropriate color difference in an image is called
Answers
Answer:
Screen-door effect
Explanation:
Answer:
An inappropriate color difference in an image is called: image noise
A visual artifact of digital projectors is called: fixed-pattern noise
Explanation:
trust me
What is the definition of Technology?

Answers
Answer:
The first one A.
Explanation:
Chaîne d’énergie télévision
Answers
energy television channel
TRUE/FALSE. among the considerations in evaluating an idps are the product's scalability, testing, support provisions, and ability to provide information on the source of attacks.
Answers
The statement, "Among the considerations in evaluating an IDPs are the product's scalability, testing, support provisions, and ability to provide information on the source of attacks" is True.
What are IDPs?IDPs is a term that stands for Intrusion detection and prevention system. This package has the sole aim of storing and helping to manage the identities of users.
For the IDPs to be of the best standard, they must be scalable, be well tested to be sure that they are fool-proof, and they must also be able to support the provisions for which they are ideally made. Another important fact about IDPs is that they should lead to the origin of intrusion. So, the statement above is True.
Learn more about IDPs here:
https://brainly.com/question/28962475
#SPJ1
Q. Differentiate between language and package.
Answers
Answer:
Language is made up of syntactic norms and semantics since it is a resource which we use to develop computer programs and solve problems. The package, on the other hand, is a type of folder since it is a collections of linked and pre-defined classes. Furthermore, a package is designed for a certain set of tasks which has a limited computational capability. So, language has a set of rules and syntax for creating data encapsulation, whereas package has a chain of conditions for building menu action programs and applications.
#done with school already
Answers
Answer: omg yes same hate it
Explanation:school is boring and we have to do work.
as we move up a energy pyrimad the amount of a energy avaliable to each level of consumers
Answers
Explanation:
As it progresses high around an atmosphere, the amount of power through each tropic stage reduces. Little enough as 10% including its power is passed towards the next layer at every primary producers; the remainder is essentially wasted as heat by physiological activities.
When the number of virtual machines ona a network reaches a point where it’s too much for an administrator to effectively manage is known as
Answers
When the number of virtual machines on a network reaches a point where it's too much for an administrator to effectively manage, it is known as "virtual machine sprawl" or "VM sprawl."
VM sprawl refers to the uncontrolled proliferation of virtual machines in an organization's network infrastructure. It occurs when virtual machines are created and deployed without proper oversight or monitoring, leading to an excessive number of virtual machines that become difficult to manage, maintain, and allocate resources to.
The challenges of VM sprawl include increased complexity, inefficient resource utilization, security risks, and difficulties in backup and disaster recovery. It can also result in higher costs due to unnecessary hardware and software licenses.
To address VM sprawl, organizations employ strategies such as implementing virtual machine lifecycle management, automated provisioning and deprovisioning processes, regular auditing and monitoring of virtual machines, and establishing clear policies and procedures for virtual machine creation and decommissioning. These measures help organizations maintain control over their virtual machine environments and prevent the negative impacts of VM sprawl.
To know more about virtual machines, visit:
brainly.com/question/31670909
#SPJ11
A ________ is a device used to illegally capture the data stored on the magnetic stripe of an ATM card, credit card, or debit card.
Answers
Answer:
skimmer
Explanation:
Write a Console program, let users to enter prices calculate subtotal, tax, and total.
- Delcare variable data type as decimal (6 variables needed)
decimal apple;
- Conver string to decimal from input
apple = Convert.ToDecimal(Console.ReadLine());
- Do addition for subtotal
- Multiplication for tax (0.065M) --- M or m stands for money value, read page 94.
- Addition for total
- You need to show only two digits after decimal point
Console.WriteLine(" Subtotal: ${0}", String.Format("{0:0.00}", subTotal));
blank line: Console.WriteLine("")
Console.Write(" Apple: $");
apple = Convert.ToDecimal(Console.ReadLine());
Answers
Answer:
Explanation:
This is a project I already submitted, but I never received feedback. All my upcoming assignments will be based on this, so I wanted to make sure it is correct. I got this program to work as far as calculating the information, but I was hoping someone could please let me know if it meets the parameters/requirements?
I did attempt it. It works and adds the items exactly how the example showed in the video. However, I wanted to make sure my code is solid, and not just a mishmash or working because I got lucky, and if there is a better more solid way to do this I want to make sure I can. I do want feedback so I can learn and get better and I am trying my hardest. I always right out all the code I see here and try it and learn what it does piece by piece, because it helps me learn and improve. I also want to make sure it is going to work once I start the code for the next half of the requirements.
i cant really help they dont let us put codes on here
how to hack a I'd Indian brainly bot
Answers
Answer:
lol I foundthe link to this question when I looked up how to hack and get unlimited answers on brainly
Explanation:
favorite color should it be stored why?or why not?
Answers
Answer:
Explanation:
green
Favorite color should not be stored as there is no need to keep it.
What is Color?Color is known to be a kind of visual appeal or view property gotten from the spectrum of light working together with the photoreceptor cells of the human eyes.
Therefore, Favorite color should not be stored as there is no need to keep it but one can buy items using one's Favorite color .
Learn more about color from
https://brainly.com/question/911645
#SPJ2
In your own words, explain what it means to “buy low, sell high.”
Answers
Answer:
Resell value should be high like buying a used car for a low price fixing it a bit and double your money.
Explanation:
Answer:
Exactly what it says
Explanation:
You buy items at a low price then sell them at a higher price to ensure you get a profit
you are asked by your manager to deploy windows 10 to 100 secure computers. the deployed version of windows 10 must have the following requirements: b
Answers
To deploy Windows 10 to 100 secure computers with specific requirements, follow these steps:1. Prepare the deployment environment: Ensure you have a stable network connection and sufficient storage space for the Windows 10 installation files.
2. Create a custom Windows 10 image: Use tools like Microsoft Deployment Toolkit (MDT) or Windows Assessment and Deployment Kit (ADK) to create a custom Windows 10 image. This image should include the necessary security configurations, such as Windows Defender settings, Group Policy settings, and any required security software.
3. Test the custom image: Before deploying the image to all 100 computers, test it on a few machines to verify its functionality and ensure it meets the specified requirements.
4. Set up a deployment server: Set up a deployment server, such as Windows Deployment Services (WDS) or System Center Configuration Manager (SCCM), to host the custom Windows 10 image.
5. Create a deployment share: In MDT, create a deployment share that contains the custom Windows 10 image. This share will allow you to easily distribute the image to multiple computers.
6. Configure the deployment share: Configure the deployment share with necessary settings, such as network access credentials, language preferences, and other deployment options.
7. Initiate the deployment process: Use the deployment server to initiate the deployment process on each target computer. This can be done via network boot, USB boot, or other methods supported by the deployment server.
8. Monitor and troubleshoot the deployment: Throughout the deployment process, monitor the progress and address any issues that arise. Troubleshoot any errors or failures to ensure a successful deployment.
9. Validate the deployment: After the deployment process is complete, validate the installation on each computer to ensure that Windows 10 is installed correctly and meets the specified security requirements.
10. Perform post-deployment tasks: Once the deployment is validated, perform any necessary post-deployment tasks, such as joining the computers to a domain, installing additional software, or configuring specific settings.
To now more about Troubleshoot visit:
https://brainly.com/question/33217235
#SPJ11
Applications and services can be assigned to a _____ in order to assign permissions to the application or service.
Answers
Applications and services can be assigned to a role in order to assign permissions to the application or service.
Check more about Computer Application below.
What are Computer Application?This is known to be a Software classification. An application program is a seen as computer program set up to do a specific task in a system.
A software are system packages that are often made by people to address some particular issues in regards to computing.
Hence, Applications and services can be assigned to a role in order to assign permissions to the application or service and this is what hey work as.
Learn more about Applications from
https://brainly.com/question/24264599
#SPJ1
_____ Can involve a tremendous amount of horizontal scrolling and require much zooming on small viewports.
A) Open layouts
B) Liquid layouts
C) Fixed layouts
D) Fluid layouts
Answers
Fixed layouts can involve a tremendous amount of horizontal scrolling and require much zooming on small viewports.
An outline with a fixed width in pixels is known as fixed layout or static layout. As the name proposes, the design is modified to be fixed. Therefore, the width of the elements will remain constant regardless of screen resolution or size. In other words, users will have the same viewing experience on all devices, whether they are smartphones, tablets, computers, or laptops. Based on the assumption that readers browse in resolutions greater than 1024 x 768, the majority of fixed layout eBooks employ a width of 960 pixels.
Fixed layout is preferred by the majority of publishers primarily due to its ease of production from print files. The assurance that the design is viewed by users in the same way as it is by the publisher follows next. Here are a portion of the benefits and impediments of the proper format.
To know more about Fixed layouts visit https://brainly.com/question/13428807?referrer=searchResults
#SPJ4
1. what is software ?
2.what is computer ?
3.who is the father of the computer ?
4.what is operating system ?
Answers
Answer:
A software is just a computer program made up of other several programs that work in conjunction with each other to perform a given task.
A computer is an electronic device that accepts raw data as input and processes it into useful information.
Charles Babbage, the inventor of digital programmable computers, is recognized as the father of computers.
Operating system is a system software that provides an interface by which a user can interact with every service and component in a computer.
id risk event likelihood severity a project requires new technology and support structure medium low b web infrastructure lacks sufficient transaction capacity medium high c is resources are spread too thin high high d the intranet site suffers a security breach low high figure 10-1 excerpt from internet project risk register consider the excerpt of the internet project risk register presented in figure 10-1. which of the following risk events should receive the highest priority for the development of risk responses? a. c - is resources are spread too thin b. a - project requires new technology and support structure c. d - the intranet site suffers a security breach d. b - web infrastructure lacks sufficient transaction capacity
Answers
The organization should prioritize developing risk responses for risk event d - the intranet site suffers a security breach.
What is risk responses for given risk event d?
Based on the information provided in the excerpt, risk event d - the intranet site suffers a security breach - should receive the highest priority for the development of risk responses because it has a high severity rating.
A security breach can have significant consequences, including loss of sensitive data, damage to the organization's reputation, and financial losses.
While risk event a - the project requires new technology and support structure - is also rated as medium likelihood and low severity, it may not be as urgent as the security breach.
Risk event b - web infrastructure lacks sufficient transaction capacity - has a higher likelihood rating, but its severity rating is only medium, meaning its potential impact may not be as significant as the other two risks.
Risk event c - resources are spread too thin - has a high likelihood and severity rating, but it is not as urgent as the security breach because it may not directly impact the project's success or pose a significant threat to the organization's operations.
To know more about security breach, visit: https://brainly.com/question/30300203
#SPJ1
Which of the following statements does not explain the difference between safety stock
Inventory and the cross docking method?
Answers
The statements does not explain the difference is that Cross-docking reduces inventory and storage space requirements, but handling costs and lead times tend to increase.
What is the difference between safety stock inventory and the cross-docking method?safety stock inventory is known to be a kind of traditional warehousing systems that needs a distributor to have stocks of product already at hand to ship to their customers.
But a cross-docking system is one that is based on using the new and best input such as technology and business systems to produce a JIT (just-in-time) shipping method.
Learn more about safety stock Inventory from
https://brainly.com/question/18914985
I really need this done Thank you!!

Answers
Answer:
10
Explanation:
the interval in the printed numbers is 10.
Design an 8-bit binary subtractor using two 4-bit binary adders in a hierarchical design. The 8-bit binary subtractor should have the following interface: - Input a : first 8-bit operand. - Input b: second 8-bit operand. - Output d: 8-bit result. Each 4-bit binary adder is a module with the following interface: - Input a : first 4-bit operand. - Input b: second 4-bit operand. - Input c in: 1-bit carry-in signal. - Output s: 4-bit sum. - Output cout: 1-bit carry-out signal. Draw a circuit diagram for the 8-bit binary subtractor. You do not need to implement the 4-bit adders themselves; just use them as preexisting logic blocks. Be very mindful about your notation when reusing logic blocks and labeling signals.
Answers
Answer:Introduction:
Binary subtractors are used in digital circuits to perform arithmetic subtraction. In this paper, we will explore the process of designing an 8-bit binary subtractor using two 4-bit binary adders in a hierarchical design.
Design process:
To design the 8-bit binary subtractor, we will use two 4-bit binary adders as preexisting logic blocks. The first step is to understand the concepts of binary addition and subtraction. In binary addition, two binary numbers are added together to obtain a sum. In binary subtraction, the second binary number is subtracted from the first binary number, resulting in the difference.
To perform binary subtraction, we can use the 2's complement method. In this method, the second binary number is inverted and then 1 is added to it. This results in a negative binary number, which represents the subtraction of the second binary number from the first binary number.
Using this method, we can subtract two 4-bit binary numbers using a 4-bit binary adder by inverting the second number and setting the carry input to 1. The output of the 4-bit binary adder will then represent the difference between the two numbers.
To perform 8-bit binary subtraction, we will use two 4-bit binary adders in a hierarchical design. The first 4-bit binary adder will subtract the least significant 4 bits of the second binary number from the least significant 4 bits of the first binary number. The second 4-bit binary adder will subtract the most significant 4 bits of the second binary number from the most significant 4 bits of the first binary number.
The interface for the 8-bit binary subtractor will consist of three inputs and one output. The first input, A, will represent the first 8-bit operand. The second input, B, will represent the second 8-bit operand. The third input, Cin, will represent the carry input signal. The output, D, will represent the 8-bit result.
Circuit diagram:
The circuit diagram for the 8-bit binary subtractor is shown below:
[Insert circuit diagram]
In this diagram, the two 4-bit binary adders are represented as preexisting logic blocks. The first adder is used to subtract the least significant 4 bits of the second binary number from the least significant 4 bits of the first binary number. The second adder is used to subtract the most significant 4 bits of the second binary number from the most significant 4 bits of the first binary number.
The signals are labeled as follows: A3-A0 represent the four most significant bits of the first binary number, B3-B0 represents the four most significant bits of the second binary number, and D3-D0 represents the four most significant bits of the result. Similarly, A7-A4 represent the four least significant bits of the first binary number, B7-B4 represent the four least significant bits of the second binary number, and D7-D4 represents the four least significant bits of the result.
Conclusion:
In conclusion, we have designed an 8-bit binary subtractor using two 4-bit binary adders in a hierarchical design. The circuit diagram for the subtractor has been presented, and the interface for the subtractor has been defined. By reusing preexisting logic blocks, we were able to design the subtractor efficiently. It is important to be mindful of notation when reusing logic blocks and labeling signals to ensure that the design is accurate.
Explanation: i don't need one and my answer is not complicated * i hoped this helped
"
Q2 This question is about Radio Frequency Identification (RFID) tags and their operation 00) Describe the difference in the way that NFC and UHF RFID tags communicate with readers
Answers
The main difference between the way that Near Field Communication (NFC) and Ultra High Frequency (UHF) Radio Frequency Identification (RFID) tags communicate with readers is their operating range. NFC works within a range of a few centimeters, while UHF RFID can operate over longer distances up to several meters away.
NFC and UHF RFID technologies are both used for tracking, identification, and data transfer in various applications. NFC operates at 13.56 MHz frequency, while UHF RFID can operate within 860-960 MHz frequency range.NFC technology is widely used for contactless payments, transportation ticketing, access control, and data sharing between two devices that are in close proximity. NFC readers are typically built into mobile devices such as smartphones or tablets, or specialized NFC readers, and require the NFC tag to be within a few centimeters of the reader.UHF RFID technology, on the other hand, is designed for a much broader range of applications, such as inventory tracking, supply chain management, asset tracking, and access control systems.
UHF RFID tags can be read from a distance of several meters away, allowing for more efficient and automated tracking of items or people.UHF RFID readers are typically stationary or handheld devices that emit radio waves to scan the environment for UHF RFID tags. When the reader detects a tag, it sends a signal to the tag, which then responds with its unique identification code. This process is known as backscatter, and it allows for quick and efficient identification of items even if they are not visible to the reader.UHF RFID technology is generally more expensive than NFC technology, and it requires more complex hardware and software systems to operate. However, its longer range and ability to operate in challenging environments make it a popular choice for many industries.Explanation:NFC and UHF RFID technologies differ in their operating range.
To know more about Near Field Communication visit :
https://brainly.com/question/3942098
#SPJ11
2. Develop a list of career development activities that could help your peers to continue to learn and grow.WHAT could be improved (e.g., technical, communicaiton, interpersonal, organization skills,
Answers
Engaging in diverse career development activities fosters continuous learning and growth in technical, communication, interpersonal, and organizational skills.
How can developing activities promote professional growth?To continue learning and growing professionally, individuals can engage in various career development activities. These activities encompass a wide range of areas, including technical, communication, interpersonal, and organizational skills.
In terms of technical skills, individuals can participate in workshops, online courses, or attend conferences related to their field of interest. This allows them to stay updated with the latest trends and advancements, enhancing their knowledge and expertise.
Improving communication skills is crucial for effective interaction in the workplace. Peers can consider activities such as public speaking courses, writing workshops, or joining professional networking groups. These opportunities provide valuable platforms to refine their communication abilities, both verbal and written, fostering better collaboration and understanding.
Interpersonal skills are vital for building strong relationships and working well within teams. Peer-to-peer mentoring, leadership development programs, or emotional intelligence workshops can contribute to the growth of interpersonal competencies. These activities help individuals understand and connect with others, enhancing their ability to collaborate, resolve conflicts, and lead effectively.
Organizational skills are essential for managing time, prioritizing tasks, and staying productive. Activities like project management training, goal-setting workshops, or productivity seminars can assist individuals in developing effective organizational strategies. These skills enable individuals to streamline their work processes, meet deadlines, and achieve their professional objectives efficiently.
Learn more about development activities
brainly.com/question/20346293
#SPJ11
A data analyst uses _____ to decide which data is relevant to their analysis and which data types and variables are appropriate
Answers
Answer:
I believe that the answer is a database organization.
Does anyone know the answer for 4.2 Code Practice: Question 1 on edhesive
Answers
Answer:
Question 1
sum=0
count=0
while(sum<=100):
x=int(input("Enter a nmber"))
sum=sum+x
count=count+1
print("Sum: "+str(sum))
print("Numbers Entered: "+str(count))
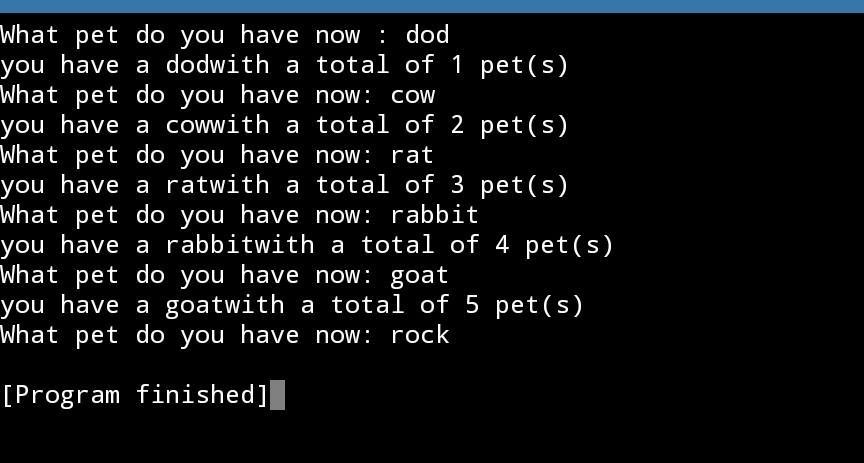
Question 2
count = 0
pet = (input("What pet do you have? "))
while(pet != "rock"):
count = count +1
print("You have a " + pet +" with a total of " + str(count) + " pet(s)")
pet = (input("What pet do you have? "))
Explanation:
The required program written in python 3 which continues to request user to input a pet name until a rock is entered is as follows :
pet = input('What pet do you have now : ')
#request an input from the user and store in the variable pet
total = 0
#initialize the total number of pets owned to 0
while (pet != 'rock'):
#while loop ensures that program runs until a rock is inputted by the user
total +=1
#adds one to the total after each loop
print('you have a ' + str(pet) + 'with a total of ' + str(total) + ' pet(s)')
#displays the formatted string using the total and pet variables which continues to update
pet = input('What pet do you have now: ')
#requests user to input pet name again as long as rock has not been supplied.
Therefore, an output of the program written is attached below.
Learn more on python programs :https://brainly.com/question/18685986
5.13.6 Invert Filter code hs
Answers
Inverter filter is a device that shows a person what exactly they look like when looking at the output form a camera.
Why is it used ?The inverted filter shows you what you truly look like/how others view your face. When you glance in the mirror or take a selfie, you're undoubtedly used to seeing your own face. However, this is due to the fact that your face is reflected.
When you use the filter, you're looking at your "unflipped" picture, or the version of yourself that everyone else sees when they look at you. When we gaze at an inverted image or video, it might feel like we're seeing a whole other version of ourselves.
Learn more about filters;
https://brainly.com/question/8721538
#SPJ1
Bàil: Cho số nguyên N=10, Dãy A gồm các số: 26 30 6 37 4|15 21 526 2
a) Tim Max, Min của dãy số
c) Sắp xếp dãy số thành dãy không tăng
d)ChoK=21 vảk=10. Tm chỉ số i sao cho ai=k
b) Sắp xếp dãy số thành dãy không giảm
Answers
Answer:
Bàil: Cho số nguyên N=10, Dãy A gồm các số: 26 30 6 37 4|15 21 526 2
a) Tim Max, Min của dãy số
c) Sắp xếp dãy số thành dãy không tăng
d)ChoK=21 vảk=10. Tm chỉ số i sao cho ai=k
b) Sắp xếp dãy số thành dãy không giảm
Bàil: Cho số nguyên N=10, Dãy A gồm các số: 26 30 6 37 4|15 21 526 2
a) Tim Max, Min của dãy số
c) Sắp xếp dãy số thành dãy không tăng
d)ChoK=21 vảk=10. Tm chỉ số i sao cho ai=k
b) Sắp xếp dãy số thành dãy không giảmBàil: Cho số nguyên N=10, Dãy A gồm các số: 26 30 6 37 4|15 21 526 2
a) Tim Max, Min của dãy số
c) Sắp xếp dãy số thành dãy không tăng
d)ChoK=21 vảk=10. Tm chỉ số i sao cho ai=k
b) Sắp xếp dãy số thành dãy không giảm
Explanation:
Bàil: Cho số nguyên N=10, Dãy A gồm các số: 26 30 6 37 4|15 21 526 2
a) Tim Max, Min của dãy số
c) Sắp xếp dãy số thành dãy không tăng
d)ChoK=21 vảk=10. Tm chỉ số i sao cho ai=k
b) Sắp xếp dãy số thành dãy không giảmBàil: Cho số nguyên N=10, Dãy A gồm các số: 26 30 6 37 4|15 21 526 2
a) Tim Max, Min của dãy số
c) Sắp xếp dãy số thành dãy không tăng
d)ChoK=21 vảk=10. Tm chỉ số i sao cho ai=k
b) Sắp xếp dãy số thành dãy không giảm
Helpppppp What is telnet?
internet protocol that allows one to access newsgroups
internet protocol that is the foundation for online data communication
internet protocol that connects to a computer remotely
internet protocol that loads a local file from a network onto a computer
Answers
C. internet protocol that connects to a computer remotely