What will be displayed as a result of executing the following code? public class test { public static void main(String[] args) { int value1 = 9; System.out.println(valuel); int value2 = 45; System.out.println(value); System.out.println(value); value = 16;
Answers
The code will not compile as there are typos in the variable names. "valuel" and "value" are not declared variables.
```java
public class Test {
public static void main(String[] args) {
int value1 = 9;
System.out.println(value1);
int value2 = 45;
System.out.println(value2);
System.out.println(value2);
value2 = 16;
}
}
```
Based on this corrected code, the output will be:
```
9
45
45
```
This is because the `System.out.println()` method is used to display the values of the variables `value1` and `value2`. The value of `value2` is changed to 16 after the last `println()` statement, but it is not printed after that change, so it does not affect the output.
To learn more about declared variables, click here:
brainly.com/question/14006589
#SPJ11
Related Questions
hris has received an email that was entirely written using capitalization. He needs to paste this text into another document but also ensure that the capitalization is removed.
What should Chris do?
Answers
the following header is seen when inspecting traffic from a web server to a browser client. what might a security consultant recommend be changed to reduce risk for the web server?
Answers
The administrator can disable the banner in IIS.
An administrator is someone who makes sure an organization runs well. Depending on the type of business, group, or entity where they are employed, their precise responsibilities vary. Administrators must be extremely organized and have excellent communication abilities.
The person designated by a court to administer a decedent's estate is also referred to by this title. In these situations, either the deceased person left no will, or the will failed to name an executor. In addition, if the designated executor is unable or unwilling to act, the court may nominate an administrator.
A court could appoint an administrator to oversee a company's operations.
Here you can learn more about administrator in the link brainly.com/question/29994801
#SPJ4
When you purchase a device, system software is already loaded on it. Which of the following system software settings can you customize?
Answers
Answer:
Screen resolution
Explanation:
The brightness of the words and pictures displayed on computer screen is referred to as screen resolution. Items seem crisper at larger resolutions, such as 1600 x 1200 pixels. They also seem smaller, allowing for more objects to be displayed on the screen. The greater the resolution supported by a display, the larger it is.
Match each type of option on the left with a corresponding function on the right.
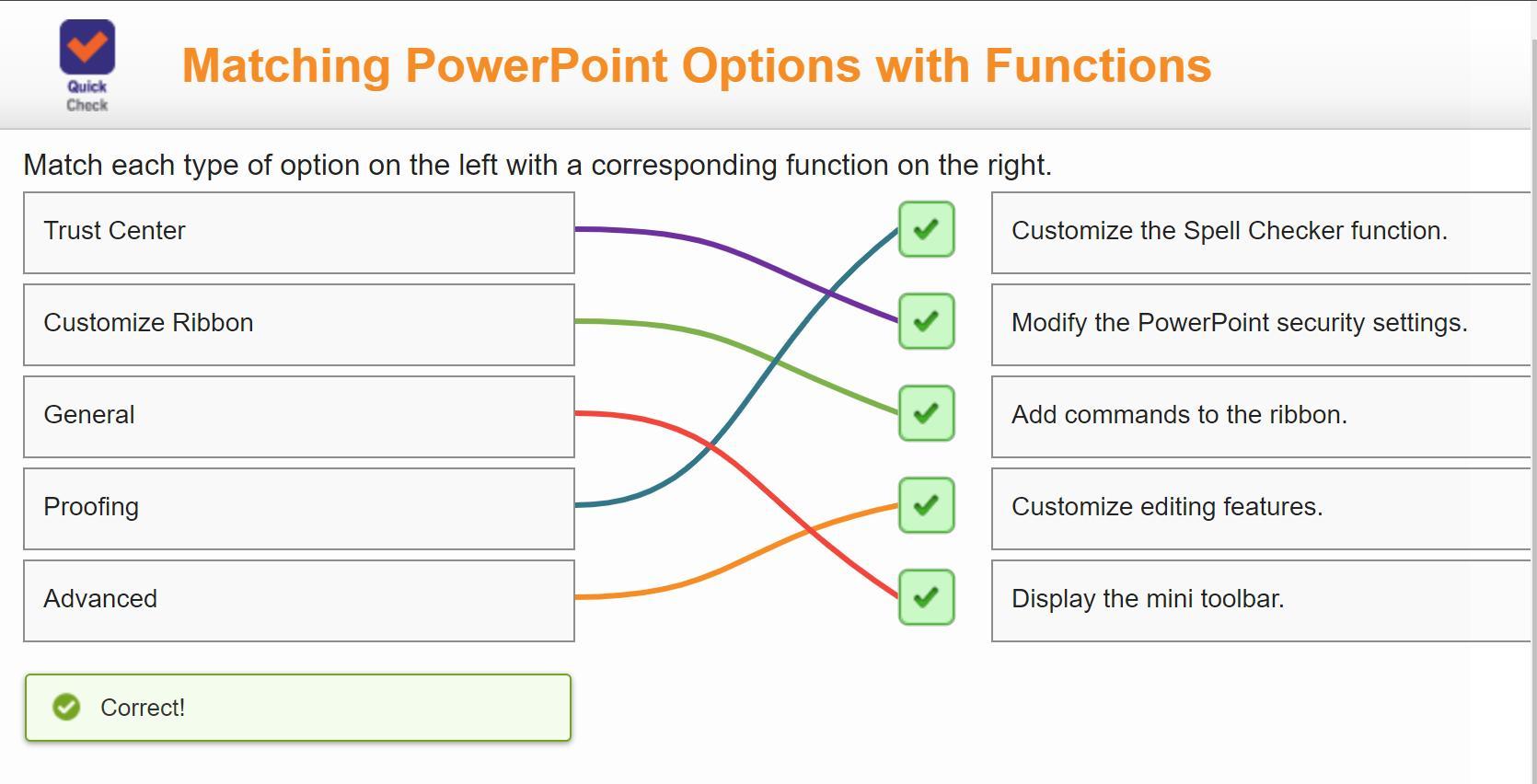
Answers
Answer:
yes. the above is correct
Explanation: q posted
Answer: Anwer is correctly shown!!!!!!!!
Explanation:
HOPE IT HELPS Y'ALL!!!!!!!!!!!!!!!!!!!!!!!!!!!!!

you are the network administrator for westsim. the network consists of a single active directory domain. all the servers run windows server 2016, and all the clients run windows 10. the network had a child domain named east.westsim. the domain was decommissioned but several snapshots were taken prior to the decommissioning. management requests that you identify the members of a group that existed in the east.westsim. you mounted the last snapshot to examine the group on a domain controller named dc1, but you now need to see the data in the snapshot. what command should you run?
Answers
As a network adminstrator, to see the data in the snapshot, you should use the "dsquery" command. Specifically, you should use the following command:
dsquery group -snapshot <snapshot_location> -name <group_name>
What is the explanation for the above response?Replace <snapshot_location> with the location of the mounted snapshot and <group_name> with the name of the group you are trying to identify the members of.
For example, if the mounted snapshot is located at "D:\Snapshots\Snapshot1" and the group you are looking for is named "EastGroup", the command would be:
dsquery group -snapshot D:\Snapshots\Snapshot1 -name EastGroup
This command will search the snapshot for the specified group and return information about its members.
Learn more about network administrator at:
https://brainly.com/question/14093054
#SPJ1
ill give brainliest whoever does this fsteset.
an array has been created which stores names. write an algorithm which saves each name on a new line in a text file called student.txt.
names["jane", "Humayun" , "Cora" , " Astrid" , "Goran"]
Answers
The algorithm which saves each name on a new line in a text file called student.txt is given as follows:
names = ["jane", "Humayun", "Cora", "Astrid", "Goran"]
with open("student.txt", "w") as file:
for name in names:
file.write(name + "\n")
What is the rationale for the above response?Open the file student.txt in write mode.
Loop through each name in the array names:
a. Write the current name to the file followed by a newline character.
Close the file.
This will create a new text file called student.txt (or overwrite it if it already exists) and write each name from the names array on a new line in the file. The "\n" character at the end of each name ensures that each name is written to a new line in the file.
Learn more about algorithm at:
https://brainly.com/question/22984934
#SPJ1
Security Technology Incorporated (STI) is a manufacturer of an electronic control system used in the manufacture of certain special-duty auto transmissions used primarily for police and military applications. The part sells for $61 per unit and STI had sales of 24,300 units in the current year, 2021. STI had no inventory on hand at the beginning of 2021 and is projecting sales of 26,900 units in 2022. STI is planning the same production level for 2022 as in 2021, 25,600 units. The variable manufacturing costs for STI are $22, and the variable selling costs are only $0.40 per unit. The fixed manufacturing costs are $128,000 per year, and the fixed selling costs are $560 per year.
Required:
1. Prepare an income statement for each year using full costing.
2. Prepare an income statement for each year using variable costing.
Answers
1. Under full costing, STI's income statement for the current year shows sales revenue of $1,486,300, cost of goods sold of $779,500, and a net income of $259,800. For the projected year, sales revenue is estimated to be $1,641,400, cost of goods sold to be $812,800, and a net income of $328,800.
2. Under variable costing, STI's income statement for the current year shows sales revenue of $1,486,300, variable expenses of $657,900, and a net income of $294,200. For the projected year, sales revenue is estimated to be $1,641,400, variable expenses to be $712,600, and a net income of $342,800.
Under full costing, all manufacturing costs, both variable and fixed, are included in the cost of goods sold. This means that the income statement reflects the complete cost of producing each unit, including the allocation of fixed costs. In the current year, STI had sales of 24,300 units, which generated sales revenue of $1,486,300 (24,300 units x $61 per unit). The cost of goods sold was $779,500, calculated as (24,300 units x $22 variable manufacturing cost) + $128,000 fixed manufacturing costs. Subtracting the cost of goods sold from sales revenue gives a net income of $259,800.
For the projected year, STI estimates sales of 26,900 units, which would generate sales revenue of $1,641,400 (26,900 units x $61 per unit). The cost of goods sold is estimated to be $812,800, calculated as (26,900 units x $22 variable manufacturing cost) + $128,000 fixed manufacturing costs. Subtracting the cost of goods sold from sales revenue gives a projected net income of $328,800.
Under variable costing, only the variable manufacturing costs are included in the cost of goods sold, while fixed manufacturing costs are treated as period costs and are not allocated to the units produced. In the current year, the variable expenses amounted to $657,900, calculated as 24,300 units x $22 variable manufacturing cost. Subtracting the variable expenses from sales revenue gives a net income of $294,200.
For the projected year, the variable expenses are estimated to be $712,600, calculated as 26,900 units x $22 variable manufacturing cost. Subtracting the variable expenses from sales revenue gives a projected net income of $342,800.
Learn more about income statement
brainly.com/question/14890247
#SPJ11
Need help on Assignment 4: Evens and Odds

Answers
n = int(input("How many numbers do you need to check? "))
even = 0
odd = 0
for x in range(n):
num = int(input("Enter number: "))
if num % 2 == 0:
even += 1
print(str(num) + " is an even number.")
else:
odd += 1
print(str(num) + " is an odd number.")
print("You entered " + str(even) + " even number(s).")
print("You entered " + str(odd) + " odd number(s).")
This works for me. Best of luck.
Before a new email application could be released to the public, it was released for a few days to some account holders of a website. The project team then collected feedback from this limited number of users and later made the email application available for public use. What type of testing did the project team use?
The project team used __ testing for the email application.
Answers
Answer:
closed
Explanation:
closed beta testing
Answer:
beta
Explanation:
What are the steps to complete an internet search?
Answers
Answer:
step one: open your search engine
step two: type what you wanna search for in the text box
step three: press enter
and that's it
Artificial intelligence could be useful or harmful for humans true or false
Answers
Answer:
Artificial intelligence (AI) can be both useful and harmful for humans, depending on how it is developed and used. AI has the potential to solve complex problems, improve efficiency, and enhance human capabilities in various fields such as healthcare, education, and transportation. However, AI can also pose risks and challenges, such as job displacement, biased decision-making, and security threats. Therefore, the statement
"Artificial intelligence could be useful or harmful for humans" is true.A study was undertaken to compare moist and dry storage conditions for their effect on the moisture content(90) of white pine timber. The report on the findings from the study included the following statement: "The study showed a significant difference (observed difference =1.1% : p-value 0.023 ) in the moisture content of the pine timber under different storage conditions. Level of Significance (a) for the test was 5%.
2
Based on this informstion, which of one the following statements is necessarily FAL.SE? The probabaisy that there is no difterence between moist and dry stor fpe conditons is 0.023 Thi observed difference between the mean moisture contents 1.1869 b uniskely to be due to chunce aione Trthis stody was repeated 100 hmess oven then we wehald espect to fincorrectly) conciude there was differense in thet storage methods for approvimatety 5 of the 100 studies ithat l. 5% of the time we would say there wara difference in the storago methods when in fact, there was nonek. A statistically significant difference of 1.18 in the moisture content of the white pine is not necessarily a difference of practical importance A. 95% confidence interval for the mean ( μ of a random variable, based on the t-distribution, is found to be (4.3, 4.9). With minimal further calculations, the p-value for a test of
H
0
:μ=5
H
1
:μ=5
can be ciaimed to be <0.001 can't say without knowing the sample size A significance test was performed to test the null hypothesis H
0
:μ−2 versus the alternative hypothesis H
1
:μ
∗
2. The test statistic is z=1.40. The p-value for this test is approximately 0.16 0.08 0.003 0.92 0.70
Answers
The false statement among the given options is:A statistically significant difference of 1.18 in the moisture content of the white pine is not necessarily a difference of practical importance.
The statement implies that even though the observed difference in moisture content is statistically significant, it may not have practical importance or relevance. However, in reality, statistical significance indicates that there is a meaningful difference between the two storage conditions. The p-value of 0.023 suggests that the observed difference is unlikely to occur by chance alone. Therefore, the statistically significant difference is likely to be practically significant as well.
To know more about moisture click the link below:
brainly.com/question/13724830
#SPJ11
6.36. Four kilograms of steam in a piston/cylinder device at 400kPa and 175 ∘
C undergoes a mechanically reversible, isothermal compression to a final pressure such that the steam is just saturated. Determine Q and W for the process.
Answers
To determine Q (heat transfer) and W (work) for the given process, we can use the first law of thermodynamics:
Q = ΔU + W
where ΔU is the change in internal energy of the system.
For an isothermal process, the change in internal energy (ΔU) is zero since the temperature remains constant. Therefore, the equation simplifies to:
Q = W
Now let's calculate the work done:
Work done (W) = P_initial * V_initial * ln(V_final / V_initial)
Given:
P_initial = 400 kPa
V_initial = (mass of steam) / (density of steam at initial conditions)
V_final = (mass of steam) / (density of saturated steam at final pressure)
To calculate the specific volume (V), we can use the steam tables or properties of water and steam at different conditions.
Once we have the specific volumes at initial and final conditions, we can calculate W using the equation mentioned above.
To calculate Q, we can use Q = W since it is an isothermal process.
To know more about temperature visit-
https://brainly.com/question/14532989
#SPJ11
which ieee 802.11 phy technology specifies an 80 mhz wide channel for transmitting and receiving data?
Answers
The IEEE 802.11n PHY technology specifies an 80 MHz wide channel for transmitting and receiving data. This technology supports data rates of up to 600 Mbps.
The IEEE 802.11ac standard, which is a PHY technology, specifies an 80 MHz wide channel for transmitting and receiving data. PHY, or physical layer, technology is a wireless networking term that refers to the physical hardware and components that transmit and receive radio waves in the network's lower-level network stack.
Read more about the ieee 802.11 phy technology
https://brainly.com/question/30701436
#SPJ11
hmac algorithm is hash function-dependent, and it is therefore hard to replace a hash function with another without making substantial changes to the algorithm.
true or false
Answers
True. The HMAC algorithm, which stands for Hash-based Message Authentication Code, is indeed hash function-dependent.
This means that the specific hash function used by the algorithm is a critical component of how it operates and generates its output.
As a result, replacing the hash function with another one would require significant modifications to the algorithm's design and implementation.The reason for this is that different hash functions have unique properties and characteristics that can affect the security and effectiveness of the HMAC algorithm. For example, some hash functions may be more resistant to certain types of attacks or have different output sizes, which could impact the way that the HMAC algorithm generates and verifies message authentication codes.Therefore, when designing and implementing the HMAC algorithm, it is important to carefully select an appropriate hash function that meets the desired security and performance requirements. Any changes to the hash function used by the algorithm should be thoroughly evaluated and tested to ensure that they do not compromise the overall security and effectiveness of the system.Know more about the HMAC algorithm
https://brainly.com/question/31717985
#SPJ11
explain the emergence of cloud computing as a distinct field of expertise resulting from the business drivers and technology innovations
Answers
Renting computer services is key to cloud computing. This concept initially appeared in the 1950s. Five innovations were critical in shaping cloud computing into what it is today. Distributed systems and its peripherals, virtualization, web 2.0, service orientation, and utility computing are examples.
How does developing cloud computing technologies assist expanding businesses?Cloud computing encompasses data storage, networking, servers, and databases as tools and applications. Instead of keeping essential information on a proprietary hardware device or a local storage unit, cloud-based storage allows organizations to access it from anywhere. The notion of virtualization emerged with the internet, as firms began to rent out "virtual" private networks. In the 1990s, the usage of virtual computers became widespread, resulting in the creation of current cloud computing infrastructure. A hybrid cloud architecture combines public and private clouds dedicated to a certain firm whose data is their primary business driver, such as insurance, banking, and so on. As a result, Multi and Hybrid Cloud Deployment will be among the top cloud computing trends in 2023 and subsequent years.
Learn more about servers from here;
https://brainly.com/question/7007432
#SPJ4
Select all the correct answers.
Hans is works for a software company that is developing a banking service that employs online transaction processing. What are two advantages
of using this technology?
•It is simple to implement due to redundancy.
•It allows customers to access the service from any location.
•It experiences minimal losses during downtime.
•It provides a secure environment for transactions.
•It processes a transaction even if part of the transaction fails.
Answers
Banking services are monetary transaction that includes the deposit and withdrawal of money. The online transaction process allows one to access services in any place and secure transaction environment.
What is an online transaction?Online transactions are the transfer of money on the cloud platform using internet services. The financial transactions are done on the web banking platform that includes money transfers, bill payments, shopping, etc.
Online transactions do not require physical presence and can be done at any place irrespective of the location the money gets transferred to the person. Also, it provides a secure environment to transact any amount.
Therefore, a secure environment and access to services at any place are the two advantages of online transactions.
Learn more about online transactions here:
https://brainly.com/question/24192124
#SPJ1
Answer:
a
Explanation:
what the first guy said
it2700 system analysis and design describe the company's overall network topology. what communications in this network need to be done with online processing?
Answers
To describe the overall network topology of the company for IT2700 system analysis and design, it is necessary to understand the communication requirements for online processing. The network topology refers to the physical or logical layout of a network, including the devices and connections used to transmit data.
In this case, the company's overall network topology could include various components such as routers, switches, servers, and workstations connected through a local area network (LAN) or wide area network (WAN). The network may also have different layers, including the physical, data link, network, transport, and application layers.
To ensure effective online processing, the communications in this network should be reliable, secure, and efficient. This means that the network should support real-time data transmission, ensuring that data is delivered in a timely manner.
Some of the key communications that need to be done in this network for online processing include data transfer between servers and workstations, communication between different departments, and communication with external partners such as customers and suppliers. The network should also be capable of supporting various types of data such as voice, video, and text.
In conclusion, a thorough system analysis of the company's network topology is necessary to identify the communications required for online processing. This analysis will ensure that the network is efficient, secure, and reliable, supporting the organization's goals and objectives.
To learn more about network topology: https://brainly.com/question/29756038
#SPJ11
What is the average number of nodes accessed in search for a particular element in an unordered list? In an ordered list? In an unordered array? In an ordered array?
Answers
Answer and Explanation:
1. In the case of the unordered list, the search algorithm is applied as the binary search would not be worked here also the time complexity for searching for n number of elements is O(n)
So the average number of nodes for the unordered list is n ÷ 2
2. For the ordered list, the same is to be considered i.e. n ÷ 2
Also it deals with the recepts of items and every item contains a relative position that represents an attribute of an item
3. For the unordered array, the same is to be considered i.e. n ÷ 2 but in this no sequence is followed
4. For the ordered array, the average number of nodes is \((log_2n) - 1\) and in this, the binary search is to be considered
The program prompts the user for five to ten numbers all on one line, separated by spaces, calculates the average of those numbers, and displays the numbers and their average to the user.
The program uses methods to:
1) get the numbers entered by the user all on one line separated by spaces;
2) calculate the average of the numbers entered by the user; and
3) print the results.
The first method should take no arguments and return a String of numbers separated by spaces.
The second method should take a String as its only argument and return a double (the average).
The third method should take a String and a double as arguments but have no return value.
IF user input is: 20 40 60 80 100
Answers
Answer:
import java.util.Scanner;
public class AverageDemo
{
public static String getNumbers()
{
String numbers;
Scanner scn = new Scanner(System.in);
System.out.println("Enter five to ten numbers all on one line, separated by spaces: ");
numbers = scn.nextLine();
return numbers;
}
public static double calcAverage(String numbers)
{
String[] values = numbers.split(" ");
double total = 0;
for (int i = 0; i < values.length; i++)
{
total += Integer.parseInt(values[i]);
}
if (values.length == 0)
return 0.0;
else
return (total / values.length);
}
// Method definition of printResults: print the results
public static void printResults(String numbers, double average)
{
System.out.printf("\nThe average of the numbers %s is %.2f\n", numbers, average);
}
// main method
public static void main(String[] args)
{
// Call the methods
String numbers = getNumbers();
double average = calcAverage(numbers);
printResults(numbers, average);
}
}
Output:

1.1.1 Give two examples of situations or applications where electrical circuits are used. (2)
Answers
An electric circuit contains a device that gives energy to the charged particles constituting the current, such as a battery or a generator; machines that use current, such as lamps, electric motors, or computers; and the connecting wires or communication lines.
Two of the basic laws that mathematically represent the implementation of electric circuits are Ohm’s law and Kirchhoff’s rules.
What is electric circuit?
Electric circuits are organized in several ways. A direct-current circuit carries a current that courses only in one direction. An alternating-current circuit holds a current that pulsates back and forth many times each second, as in most household circuits. A series circuit includes a path along which the whole current flows through each piece
To learn more about Electric circuits , refer
https://brainly.com/question/2969220
#SPJ9
What is a valid method of spelling and capitalizing your userid on the logon screen?: tsoid01 tsoid01 tsoid01
Answers
Answer:
Explanation:
A valid method of spelling and capitalizing your userid on the logon screen would be to type it exactly as it was provided to you, without any additional spaces or capitalization changes.
In this case, the userid "tsoid01" should be entered as "tsoid01" without any changes to the capitalization or spacing. It is important to enter the userid accurately to ensure that you are able to log in successfully.
What information does a digital certificate contain? check all that apply. 1 point
Answers
The information does a digital certificate contain are;
Digital signaturePublic Key DataWhat is a digital certificate?Digital certificate is known to be a kind of technology that used to link a user's identity to that of a public key.
Note that it is used in the Identifying of the information of the certificate owner as it is said to have the public key information.
Hence, The information does a digital certificate contain are;
Digital signaturePublic Key DataLearn more about digital certificate from
https://brainly.com/question/18916601
#SPJ1
what level of dod clearance do you currently hold ? security clearance level security clearance level
Answers
Level of dod clearance is confidential. There are three levels of security clearance: confidential, secret, and top secret.
A security clearance is a determination by the government that an individual is eligible for access to classified information. The process of obtaining a security clearance involves a background check to verify the individual's loyalty, character, and trustworthiness. The level of clearance required will depend on the sensitivity of the information that the individual will have access to. There are several levels of security clearance, including confidential, secret, and top secret. In order to be eligible for a security clearance, individuals must be U.S. citizens and pass a thorough background investigation. The process can take several months and may require the individual to disclose personal information and undergo a polygraph examination.
Learn more about security clearance here, https://brainly.com/question/18021620
#SPJ4
Native advertising refers to: a.minimalist promotion relying on few graphics. b.promotion that looks like content. c.promotion conducted by indigenous peoples. d.content that looks like promotion.
Answers
b. promotion that looks like content.
What is the definition of native advertising?Native advertising refers to a form of advertising that is designed to blend in with the surrounding content, making it appear as though it is part of the editorial or organic content.
It is often created in a way that closely resembles the format, style, and tone of the platform on which it is displayed.
The purpose of native advertising is to provide a seamless user experience by delivering promotional messages in a way that doesn't disrupt or interrupt the user's consumption of content.
The goal is to make the advertising content feel more natural and less intrusive, increasing the likelihood of user engagement and interaction.
Learn more about promotion that
brainly.com/question/15331436
#SPJ11
the personnel department at a health-care organization has recently mandated preemployment personality testing for all applicants. how should a nurse-manager best interpret the results of this testing when making hiring decisions?
Answers
Understand the purpose of the personality testing: Personality tests are used to assess an applicant's traits, behaviors, and characteristics to determine if they align with the requirements of the job and the organization's culture. Review the job requirements: Evaluate the specific skills, traits, and qualities needed for the nursing position. This includes considering factors like communication skills, empathy, teamwork, problem-solving abilities, and stress management.
Compare the test results with job requirements: Analyze the personality test results to see if they align with the job requirements. Look for traits and behaviors that indicate the candidate's suitability for the role, such as being empathetic, adaptable, and able to work well in a team. the overall candidate profile: Remember that personality test results should not be the sole determining factor. Consider other aspects of the candidate's ap plication, such as their qualifications, experience, and interviews. It is important to have a holistic view of the candidate's potential fit for the organization.
Seek guidance if needed: If you are unsure how to interpret the personality test results or need additional input, consult with the personnel department or seek advice from experts in psychometric testing. In summary, when interpreting the results of preemployment personality testing, a nurse-manager should consider the job requirements, compare the test results with those requirements, and take into account the overall candidate profile.
To know more about applicant's traits Visit:
https://brainly.com/question/31923434
#SPJ11
Helppppppppppp please

Answers
Answer:
1.75
Explanation:
It is marked at 3/4 (.75) of the line so it would be 1.75
What is the confirmation or validation of an event or object?a.Fact.b.Data.c.Information technology.d.All of the above.
Answers
Fact is the Confirmation or validation refers to the process of verifying that an event or object is true or accurate.
Fact is a statement or piece of information that can be verified and is considered to be true. It is a confirmed or validated event or object. Facts can be supported by evidence and documentation, and they are an important part of understanding and explaining the world around us. They are different from opinions or beliefs, which are subjective and may not be supported by evidence. In scientific research, facts are the foundation of theories and hypotheses, and are subject to testing and verification to establish their validity.
Confirmation or validation refers to the process of verifying that an event or object is true or accurate. This is often done through the use of evidence or other forms of documentation. In this context, a "fact" would be the confirmation or validation of an event or object, as it is a piece of information that can be verified and is considered to be true. While data and information technology may be used to confirm or validate facts, they do not represent the confirmation or validation itself.
Learn more about Validation here:
https://brainly.com/question/14356883.
#SPJ4
what is ms word?? and function of Ctrl+E
Answers
Answer:
Ms word is a graphical word processing program that users use to type with.
Ctrl+E: It changes the alignment of the line or selected text so that it is centered on the page.
You have two Windows Server 2016 computers with the Hyper-V role installed. Both computers have two hard drives, one for the system volume and the other for data. One server, HyperVTest, is going to be used mainly for testing and what-if scenarios, and its data drive is 250 GB. You estimate that you might have 8 or 10 VMs configured on HyperVTest with two or three running at the same time. Each test VM has disk requirements ranging from about 30 GB to 50 GB. The other server, HyperVApp, runs in the data center with production VMs installed. Its data drive is 500 GB. You expect two VMs to run on HyperVApp, each needing about 150 GB to 200 GB of disk space. Both are expected to run fairly disk-intensive applications. Given this environment, describe how you would configure the virtual disks for the VMs on both servers.
Answers
The virtual disk configuration for the VMs on both servers in this environment is shown below.
In the Hyper V Test,
Since there will be two or three virtual machines running at once, each of which needs between 30 and 50 GB of the total 250 GB of disk space available,
What is virtual disks?Setting up 5 virtual disks, each 50 GB in size.
2 VMs each have a 50 GB virtual drive assigned to them.
The above setup was chosen because running three VMs with various virtual disks assigned to them will not pose an issue when two or three VMs are running concurrently and sharing the same virtual disk. This is because the applications are disk-intensive.
To learn more about virtual disks refer to:
https://brainly.com/question/28851994
#SPJ1
Given this environment, the virtual disk configuration for the VMs on both servers is shown below. Because two or three VMs will be running at the same time, and each VM has disk requirements ranging from 30 to 50 GB of total disk space of 250 GB.
What is Hyper V Test?While there are several methods for testing new virtual machine updates, Hyper-V allows desktop administrators to add multiple virtual machines to a single desktop and run tests. The Hyper-V virtualization technology is included in many versions of Windows 10. Hyper-V allows virtualized computer systems to run on top of a physical host. These virtualized systems can be used and managed in the same way that physical computer systems can, despite the fact that they exist in a virtualized and isolated environment. To monitor the utilization of a processor, memory, interface, physical disk, and other hardware, use Performance Monitor (perfmon) on a Hyper-V host and the appropriate counters. On Windows systems, the perfmon utility is widely used for performance troubleshooting.Therefore,
Configuration:
Creating 5 Virtual disks of 50 GB each.
1 virtual disk of 50 GB is assigned to 2 VM.
The above configuration is because since two or three VM will be running at the same time and using the same virtual disk will cause a problem since the applications are disk intensive, running three VMs with different virtual disks assigned to them, will not cause a problem.
For Hyper V App,
Two VM will run at the same time, and the disk requirement is 150 - 200 GB of 500 GB total disk space.
Configuration:
Creating 2 virtual disks of 200 GB each with dynamic Extension and assigning each one to a single VM will do the trick.
Since only two VMs are run here, the disk space can be separated.
To learn more about Hyper V Test, refer to:
https://brainly.com/question/14005847
#SPJ1