which algorithm should be used to find a phone number on a contact list?
Answers
The most commonly used algorithm to find a phone number on a contact list is a linear search algorithm.
This algorithm searches through each item in the contact list one by one until it finds the phone number being searched for. While this algorithm may not be the most efficient, it is typically suitable for smaller contact lists. For larger contact lists, more complex algorithms such as binary search or hash tables may be more appropriate.
To find a phone number on a contact list, you should use the Binary Search algorithm.
Step 1: Sort the contact list based on phone numbers or names, if not already sorted.
Step 2: Determine the middle element of the sorted list.
Step 3: If the middle element matches the desired phone number, the search is successful.
Step 4: If the desired phone number is less than the middle element, repeat steps 2-3 with the left half of the list.
Step 5: If the desired phone number is greater than the middle element, repeat steps 2-3 with the right half of the list.
Step 6: Repeat until the desired phone number is found or the search area is empty.
Using the Binary Search algorithm allows you to efficiently find a phone number on a contact list by repeatedly dividing the list in half until the desired phone number is found.
To learn more about binary search algorithm https://brainly.com/question/15190740
#SPJ11
Related Questions
User
Application Software
Operating System
Hardware
Assignment #1
•Explain the meaning of this graphics organizer base on what you have learned from this lesson.
• Is an "app" same in meaning with "application"?

Answers
This graphics organizer base talks about Software and how it is divided into two groups such as the operating systems and application software.
What are Software?Software are said to be often shared into two categories such as:
The operating systems The application software.Note that the Operating systems functions by helping the hardware and produce a kind of interface between the hardware and its user while the Application software is said to be a stage of a programs that help the user to do anything meaningful just as seen in the diagram.
Conclusively, The word "app" has the in meaning with "application". It is known to be the short form of application.
Learn more about Application Software from
https://brainly.com/question/1538272
How do u create a game
Answers
Stephen is slowing down as he approaches a red light. He is looking in his mirror to switch lanes and misjudges how close Keisha's car is, rear-ending her car. When
they get out and assess the damage, Keisha's bumper will need to be replaced. What type(s) of insurance could Stephen use to cover this accident? Explain.
Krisha had some discomfort in her neck at the time of the accident but thought it was minor and would go away. A week or so after the accident, Keisha finally goes
What t) of insurance could Keisha use to cover this accident?
Answers
The type of insurance that Stephen could use to cover this accident is known as liability coverage
What t) of insurance could Keisha use to cover this accident?The insurance that Keisha could use to cover this accident is personal injury protection.
In the case above, The type of insurance that Stephen could use to cover this accident is known as liability coverage as damage was one to his property.
Learn more about Property Damage from
https://brainly.com/question/27587802
#SPJ1
music sites through schools wifi 2020 What is one thing a person should do to stay safe when exercising? 100 pts.!
Answers
Answer:
They should stay away from others (keep workout short or at home)
always do The exercise right-properly
Explanation:
Answer:
they should stay at home and do workouts or they can start a fitness program in a safe area.
Play to end-
Back to beginning
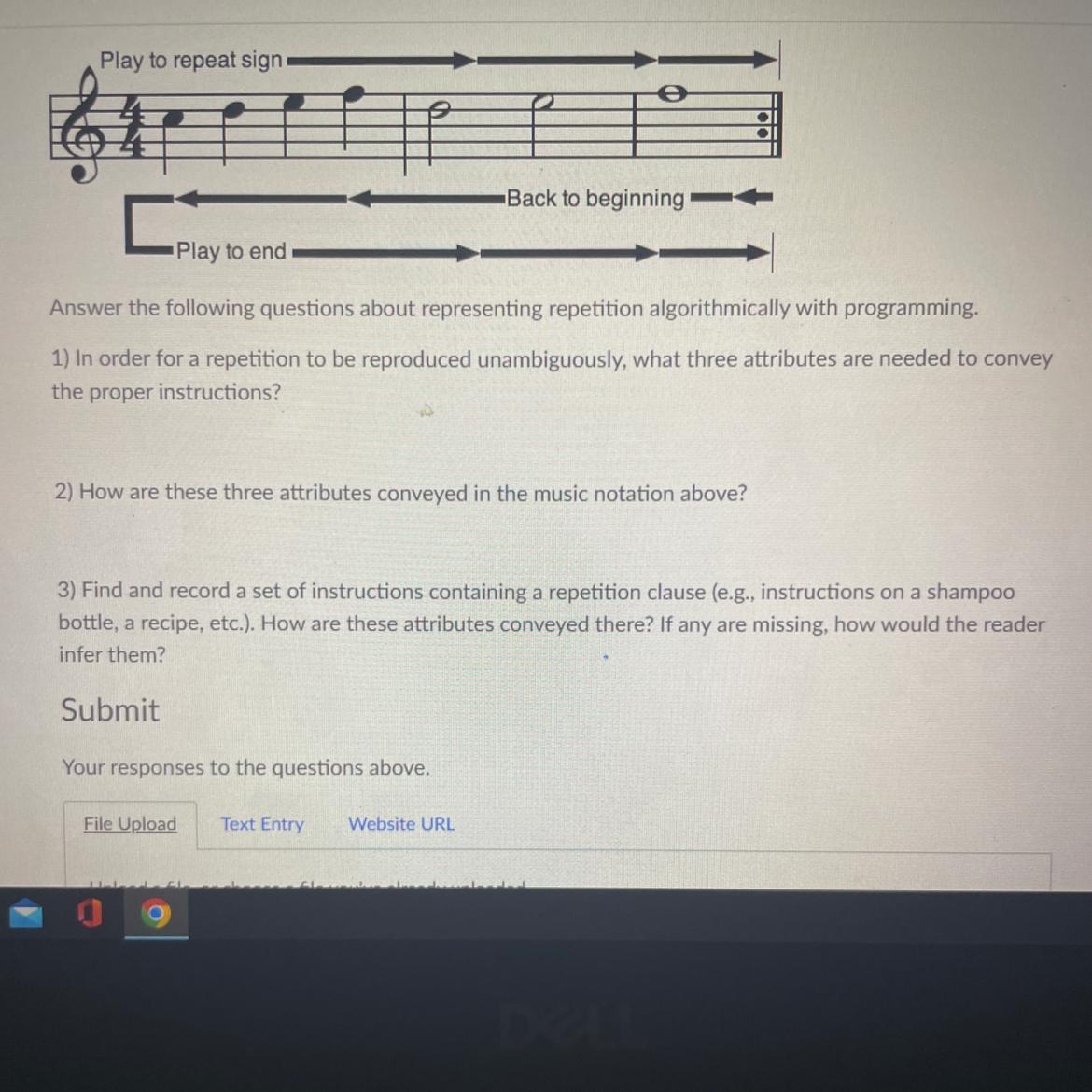
Answer the following questions about representing repetition algorithmically with programming
1) In order for a repetition to be reproduced unambiguously, what three attributes are needed to convey
the proper instructions?
2) How are these three attributes conveyed in the music notation above?
3) Find and record a set of instructions containing a repetition clause (eg, instructions on a shampoo
bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader
infer them?
Answers
There must be a starting point, a point where the code ends, and it restarts back to the beginning.
2) How are these three attributes conveyed in the music notation above?
The starting point is the beginning of the phrase, the point of where it gets sent back is the is represented by the colon symbol at the end, and thus it starts again at the beginning of the phrase.
3) Find and record a set of instructions containing a repetition clause (e.g., instructions on a shampoo bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader infer them?
How to download the McDelivery app from a McDonalds bag
- Download the uber eats app
- Select “McDonald’s”
- Order your favorite foods
In this set of instructions, it has a start where you download or open up the uber eats app, selecting the “McDonalds” option for delivery is part of the start or the middle part, and the point of repetition where the instructions can be a repeated is the ordering the food. It would’ve just been in a constant loop afterwards because the first two instructions have already been pre-completed.
hope this helps :)
Similarities and differences between simple electric circuit and home electricity network.
Answers
Electric circuits and home electricity networks are both systems that involve the flow of electrical energy.
A simple electric circuit is a closed loop through which electric current can flow. It typically consists of a power source, such as a battery, and a load, such as a light bulb or motor. The circuit also contains conductive wires or cables that connect the components together.
A home electricity network, on the other hand, is a more complex system that distributes electrical energy to various parts of a house or building. It typically includes a power source, such as a utility grid or generator, and various loads, such as lights, appliances, and electronics. The network also consists of a distribution system, which may include transformers, circuit breakers, and wiring, that connects the power source to the loads.
One key difference between a simple electric circuit and a home electricity network is their level of complexity. While a simple electric circuit consists of just a few components, a home electricity network can involve many different components and subsystems that work together to ensure safe and reliable power distribution.
Another difference is their application. A simple electric circuit is typically used for a specific purpose, such as lighting a single light bulb or powering a small motor. A home electricity network, on the other hand, is designed to power an entire house or building and provide electricity for a wide range of purposes.
Learn more about electrical energy here:
https://brainly.com/question/31481822
#SPJ11
DES is a commonly used symmetric encryption algorithm, developed in the mid-1990s by the American government in conjunction with IBM, and is the recommended encryption algorithm for highly sensitive data. True False
Answers
Answer:
False
Explanation:
The DES encryption standard is believed to be weakened by the American government by containing shortened key lengths and 'S-boxes' of unknown origin.
The first step of data analysis after generating questions,
is:
a. Preparation - ensuring data integrity
b. Analyze Data
c. Evaluation results
d. Visualizing results
Answers
The first step of data analysis after generating questions is Visualizing results. Thus, option d is correct.
Data analysis is a process of examining, sanctifying, transubstantiating, and modeling data with the thing of discovering useful information, informing conclusions, and supporting decision- timber. Data analysis has multiple angles and approaches, encompassing different ways under a variety of names, and is used in different business, wisdom, and social wisdom disciplines. In moment's business world, data analysis plays a part in making opinions more scientific and helping businesses operate more effectively.
Data mining is a particular data analysis fashion that focuses on statistical modeling and knowledge discovery for prophetic rather than purely descriptive purposes, while business intelligence covers data analysis that relies heavily on aggregation, fastening substantially on business information.
Learn more about data analysis here:
https://brainly.com/question/30094947
#SPJ4
FILL IN THE BLANK When we join orders and customers, we join on customer_id. which is a(n)_______ in orders and the primary key in customers
Answers
"When we join orders and customers, we join on customer_id. Which is a foreign key in orders and the primary key in customers."
What is a foreign key?A foreign key is a column or set of columns in one table that identifies the data in another table. It establishes a relationship between two tables. It's an identification column from one table that appears in another table, and it refers to the primary key of the original table.
A primary key is a column or set of columns in a table that identifies each row uniquely. The primary key is used to establish relationships between tables, allowing us to combine data from several tables into a single table. The table can have only one primary key column, and it cannot contain NULL values.
Learn more about foreign key https://brainly.com/question/13437799
#SPJ11
How many layers are there in the osi reference model?.
Answers
In Computer Networking, there are seven (7) layers in the OSI reference model.
The layers of the OSI model.In Computer networking, there are seven (7) layers in the open systems interconnection (OSI) model and these include the following in sequential order;
Physical LayerData link LayerNetwork LayerTransport LayerSession LayerPresentation LayerApplication LayerIn conclusion, we can infer and logically deduce that there are seven (7) layers in the OSI reference model.
Read more on OSI here: https://brainly.com/question/26177113
#SPJ1
All of the following are cloud computing services except: A) infrastructure as a service. B) platform as a service. C) software as a service. D) on-demand computing. E) virtualization as a service.
Answers
The cloud computing services that exist and are offered to the market can be grouped into three categories, including Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), and Software-as-a-Service (SaaS). Among the given alternatives, the cloud computing service that does not exist is D) on-demand computing.
Cloud computing: Cloud computing is a modern technology that delivers services to users, companies, and other clients over the internet by enabling access to a shared pool of computing resources that includes servers, storage, applications, and services.
The three cloud computing service types are Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), and Software-as-a-Service (SaaS).
Infrastructure-as-a-Service: Infrastructure-as-a-Service (IaaS) - delivers virtualized computing resources such as servers, storage, networks, and operating systems as a service over the internet.
Platform-as-a-Service: Platform-as-a-Service (PaaS) - provides a computing platform and a solution stack as a service, enabling users to develop, operate, and manage applications without having to construct and maintain the infrastructure typically associated with app development.
Software-as-a-Service: Software-as-a-Service (SaaS) - offers applications or software on a subscription basis, making it possible for users to use cloud-based applications via the internet.
On-Demand Computing: On-Demand Computing is an IT model where resources and services are provisioned based on the user's requirements in real time, enabling businesses to achieve agility and scalability in the management of their infrastructure. It is a model that differs from traditional IT models, where resources are pre-provisioned and allocated to meet the expected demand.
You can learn more about cloud computing at: brainly.com/question/11973901
#SPJ11
Martha and Ethan are evaluating the following image. What aspect of composition does this image not fulfill?
A. the use of rule of odds in the image
B.
the use of simplification in the image
C. the use of sense of movement in the image
D. the aesthetic appeal of the image
Answers
Answer: B. : the use of simplification in the image
your welcome .

Many social media platforms are designed to facilitate connection. Why then is it a problem to post about topics like politics or religion?
These topics tend to draw heated discussions.
Social media is only meant for personal information.
There is no way to block people who disagree with you.
Social media easily facilitates exploring topics in depth.
Answers
These topics tend to draw heated discussions is the reason then is it a problem to post about topics like politics or religion in social media. Hence, option A is correct.
A recent survey revealed that keeping in touch with friends and family is the main reason people use social media. This is one of the top uses of social media, according to up to 48.2% of internet users.
Because there are so many ideas, thoughts, and opinions traveling through the social media platform, it is persuasive and frequently attempts to alter or influence beliefs when it comes to political views.
Thus, option A is correct.
For more information about social media, click here:
https://brainly.com/question/31261085
#SPJ1
________ computing allows service providers to make computing resources and infrastructure management available to customers as needed and then charges a ________ rate
Answers
Cloud computing allows service providers to make computing resources and infrastructure management available to customers as needed and then charges a usage-based rate.
This type of computing service has become popular because it allows businesses to scale up or down their computing resources as needed without having to maintain and manage their own physical infrastructure. It has also opened up access to computing resources to smaller businesses that may not have had the budget to invest in their own hardware.
Cloud computing allows users to access shared resources such as storage, processing power, and applications over the internet. The service provider manages and maintains the underlying infrastructure, allowing customers to focus on their core business activities. Cloud computing providers typically charge a usage-based rate, which means customers only pay for the resources they use. This allows businesses to reduce their upfront capital expenses, since they only need to pay for what they use.
To know more about computing visit:
https://brainly.com/question/32297638
#SPJ11
Which term best describes the output of the integer division operator?
Difference
Fraction
Quotient
Remainder
Sum
Answers
Answer: Quotient
Explanation:
Which of the following statements about computer networks is true? Within a computer network, the server is the application that runs on a personal computer or workstation. All of the above statements about computer networks are true. Networks have eliminated the need for data sharing. Within a computer network, the client manages the network's resources. Computer networks include clients and servers.
Answers
The statement "Computer networks include clients and servers" is true.
- Within a computer network, the server is not the application that runs on a personal computer or workstation. The server refers to a dedicated computer or system that provides services, resources, or data to other computers or devices within the network.
- Networks have not eliminated the need for data sharing. In fact, computer networks facilitate data sharing by enabling multiple devices to connect and exchange information.
- Within a computer network, the client does not manage the network's resources. The client refers to a device or computer that requests and consumes services or resources provided by servers within the network.
Therefore, the only true statement among the options given is "Computer networks include clients and servers."
Visit here to learn more about Computer networks brainly.com/question/13992507
#SPJ11
a) Based on the information for your project, suggest three different conceptual models for your system. You should consider each of the aspects of a conceptual model discussed in this Chapter 11: interface metaphor, interaction type, interface type, activities it will support, functions, relationships between functions, and information requirements. Of these conceptual models, decide which one seems most appropriate and articulate the reasons why. steps. (b) Produce the following prototypes for your chosen conceptual model: (i) (ii) Using the scenarios generated for your topic, produce a storyboard for the chosen task for one of your conceptual models. Show it to two or three potential users and get some informal feedback. Now develop a card-based prototype from the use case for the chosen task, also incorporating feedback from part (i). Show this new prototype to a different set of potential users and get some more informal feedback. (c) Consider your product's concrete design. Sketch out the relevant designs. Consider the layout; use the colors, navigation, audio, animation, etc. While doing this use the three main questions introduced in Chapter 6 as guidance: Where am I? What is here? Where can I go? Write one or two sentences explaining your choices, and consider whether the choice is a usability consideration or a user experience consideration. (d) Sketch out an experience map for your product. Create the necessary scenarios and personas to explore the user's experience. In particular, identify any new interaction issues that you had not considered before, and suggest what you could do to address them. (e) How does your product differ from applications that typically might exists? Do software development kits have a role? If so, what is that role? If not, why do you think not?
Answers
The paragraph outlines various tasks involved in developing a system, including conceptual models, prototypes, interface design, experience mapping, uniqueness of the product, and the role of software development kits (SDKs), but specific details are required to provide a comprehensive explanation.
What is the overall explanation of the given paragraph about system development, interface design, and user experience considerations?The given paragraph outlines a series of tasks related to developing a system, including suggesting conceptual models, creating prototypes, designing the interface, developing an experience map, and discussing the product's uniqueness and the role of software development kits (SDKs).
The tasks mentioned in the paragraph belong to the domain of system development, user interface design, and user experience considerations. Each task involves different steps and methodologies to ensure the development of an effective and user-friendly system.
These steps may include conceptualizing different models, creating prototypes, gathering user feedback, designing the interface layout, considering usability and user experience factors, and addressing potential interaction issues.
To provide a detailed explanation, it would be necessary to have specific information about the project, such as the nature of the system, the target users, their goals and tasks, and the project's requirements and constraints. Without such information, it is not possible to provide a meaningful and contextually relevant explanation.
Learn more about system
brainly.com/question/19843453
#SPJ11
do
it on excel please
Problem 4-2 Calculating Future Values a. Compute the future value of \( \$ 1,250 \) compounded annually for 10 years at 5 percent. (Do not round intermediate calculations and round your answer to 2 de
Answers
The future value of $1,250 compounded annually for 10 years at a 5% interest rate needs to be calculated.
To calculate the future value, we can use the formula for compound interest:
Future Value = Present Value * (1 + Interest Rate)^Number of period
In this case, the present value is $1,250, the interest rate is 5%, and the number of periods is 10 years. Plugging these values into the formula, we can calculate the future value.
To perform this calculation in Excel, you can use the following formula:
=FV(interest rate, number of periods, 0, present value)
In this case, the interest rate would be 5%, the number of periods would be 10, and the present value would be -$1,250 (negative because it represents an outgoing payment). The final result will be the future value of the investment after 10 years.
Using Excel's FV function makes it easy to perform this calculation and obtain the future value accurately.
learn more about interest rate here
https://brainly.com/question/28236069
#SPJ11
which of the following best describes a code of ethics?
Answers
The code of ethics refers to the guide of principles that are required to help professionals so that they can conduct their business with integrity.
Organizations adopt code of ethics so that their members can be able to know the difference between what is considered right and what is wrong.Through code of ethics, employees can be judged in an organization when they do something that doesn't align with the ethical standards of the organization.
In conclusion, code of ethics is important as it shapes an organization in the right direction.
Read related link on:
https://brainly.com/question/21819443
The Ethics Code relates towards the guidance of principles that specialists need to help them perform their business with integrity.
It also included business ethics, a code of professional behavior as well as rules of ethics for employees.Organizations adopt an ethics code so that their representatives can understand the difference between what is wrong and what is right.Employees may be judged in an organization through an ethics code when they do anything that does not match the company's ethical standards.The code of ethics is important because it shapes an organization.Therefore, the final answer is "code of ethics".
Learn more:
brainly.com/question/13818432
Discuss the Autonomous Robots and Additive Manufacturing contribution to Smart Systems. Why are these two technologies are important for the Smart Systems? Explain the technologies with an example.
Answers
Additive manufacturing, also known as 3D printing, revolutionizes traditional manufacturing methods by constructing objects layer by layer. It enables rapid prototyping, customization, and on-demand production. For instance, in a smart healthcare system, additive manufacturing can be employed to produce personalized medical implants, such as customized prosthetics or dental implants, based on patient-specific requirements, resulting in improved patient outcomes and reduced lead times. Both technologies contribute to the advancement of Smart Systems by optimizing processes, enhancing productivity, and enabling customization in various industries.
Most personal computers allow users to expand their systems by providing these on thesystem board.
a. Expansion slots
b. Ports
c. Sound cards
d. Network adapters.
Answers
The correct answer is: a. Expansion slots. Most personal computers allow users to expand their systems by providing Expansion slots on thesystem board.
Most personal computers allow users to expand their systems by providing expansion slots on the system board. Expansion slots are connectors on the motherboard that allow users to add new hardware components such as graphics cards, sound cards, network adapters, and other expansion cards.
By adding expansion cards to these slots, users can customize and upgrade their computer systems to meet their specific needs and improve performance. Examples of expansion slots include PCI, PCIe, and AGP.
Therefore, option a is the correct answer.
Learn more about Expansion slots here brainly.com/question/14312220
#SPJ4
what is a cell address in xsl sheet
Answers
Answer:
cell address is the exact location of a particular cell of ms-excle
Explanation:
A1 refers to first row and first column.
A2 refers to second row first column.
i.e.
in 'A1' : 'A' indicate column { A= first column, B= second
column, C= third column. and soon.....}
'1' indicate row { 1 = first row, 2 = second row, 3= third row..... soon .......}
Which of the following best describes what a thesis for a historical essay should be?
A.
a well-researched fact
B.
a summary of an event
C.
an interpretive claim
D.
an uncontestable statement
Answers
A historical essay's thesis is most appropriately characterized as an interpretive claim. Argumentative historical thesis statements provide the author's viewpoint on a subject.
What is a thesis statement?The thesis statement contains information about the subject being covered, the arguments put forth in the work, and the intended audience. Your thesis statement should be in the final sentence of your introduction, which is typically referred to as your first paragraph.
What is a historical writing thesis statement?The statement that summarizes the historical argument is known as the thesis. The claim or thesis is cited by the Common Core State Standards as a crucial component of writing in history classes.
To know more about interpretive visit:-
https://brainly.com/question/25064859
#SPJ1
Suppose you are assigned the task of the improvement of software development processes of an organization to meet certain organization goals. Your task is to discuss the steps or course of action that you would take in order to improve the organizational software development processes (one or two processes) for achieving certain defined organizational goals.
You also need to clearly state as to why and what goals you want to achieve by improving the organizational software processes. Moreover, you are encouraged to use visual / graphical representations / models (complete process map) to help visualize the entire improvement cycle or process. Furthermore, you should try to be as detailed as possible regarding the potential improvement steps.
Answers
The improvement steps should be tailored to the specific organizational goals and challenges. Regular monitoring and evaluation of the improved processes should be carried out to ensure that the desired goals are being achieved and to identify further areas for refinement. Continuous improvement is essential to maintain the effectiveness and efficiency of the software development processes in line with organizational goals.
To improve the organizational software development processes, the first step is to clearly define the goals that the organization wants to achieve. These goals could include improving the speed of software delivery, enhancing the quality of software products, increasing customer satisfaction, or optimizing resource utilization. Once the goals are identified, a thorough analysis of the current processes should be conducted to identify areas of improvement.
One potential improvement step is to adopt an agile development methodology. This involves breaking down the software development process into smaller, manageable iterations called sprints. Agile methodologies, such as Scrum or Kanban, promote collaboration, flexibility, and faster delivery of software. By implementing agile practices, the organization can achieve goals like increased speed of software development, improved collaboration between development teams and stakeholders, and enhanced responsiveness to changing customer requirements.
Another potential improvement step is to implement continuous integration and continuous delivery (CI/CD) practices. CI/CD focuses on automating the build, testing, and deployment processes, enabling frequent and reliable software releases. By automating these processes, the organization can achieve goals like reducing time-consuming manual tasks, improving the quality of software through automated testing, and enabling faster and more efficient deployment of software updates.
Throughout the improvement process, visual or graphical representations, such as process maps, can help in documenting and visualizing the software development processes. These representations provide a clear overview of the steps involved, the dependencies between different activities, and potential areas for optimization.
Overall, the improvement steps should be tailored to the specific organizational goals and challenges. Regular monitoring and evaluation of the improved processes should be carried out to ensure that the desired goals are being achieved and to identify further areas for refinement. Continuous improvement is essential to maintain the effectiveness and efficiency of the software development processes in line with organizational goals.
To learn more about software click here: brainly.com/question/32393976
#SPJ11
a student uses a flash drive to store assignments/homework. the student plugs in the flash drive, reboots the computer, and it displays a message indicating the operating system is not found. what are two possible ways of fixing the problem relatively quickly?
Answers
The two possible ways of fixing the problem relatively quickly are a USB flash drive can store important files and data backups, carry favorite settings and use its software and hardware.
What is the operating system?An operating system (OS) is the program that controls all other application programs in a computer after being installed into the system first by a boot program. Through a specified application program interface, the application programs seek services from the operating system (API). Examples of operating systems that let users utilize applications like Microsoft Office, Notepad, and games on a computer or mobile device include Windows, Linux, and Android. To execute simple programs like browsers, the computer must have at least one operating system installed. The software needed to run application applications and utilities is known as the operating system.It serves as a conduit for more effective communication between computer hardware and application software.UNIX, MS-DOS, Windows 98/XP/Vista, Windows NT/2000, OS/2, and Mac OS are a few examples of operating systems.To learn more about operating system, refer to:
https://brainly.com/question/22811693
#SPJ4
Write the method drawSquare below.
/** Precondition: 0 ≤ x < 10, 0 < y ≤ 10, and len > 0.
* Draws a square on a 10-by-10 xy-coordinate grid
* and prints the square’s side length and area.
* The upper left corner of the square will be located
* at the coordinate (x, y) and the side length of the * square will be len (or as large as will fit in the grid).
*/
public void drawSquare(int x, int y, int len)
Answers
The method drawSquare is an illustration of functions; functions are named program statements that are executed when called
The method drawSquareThe method drawSquare written in Java, where comments are used to explain each action is as follows:
//This defines the function
public static void drawSquare(int x, int y, int len) {
//This checks if x + len exceeds 10
if(x+len>10){
len = 10-x;}
//This checks if y + len exceeds 10
if(y+len>10){
len = 10-y;}
//The next four lines draw the square
drawLine(x, y, x+len, y);
drawLine(x+len,y,x+len,y-len);
drawLine(x+len, y-len, x, y-len);
drawLine(x, y-len, x, y);
}
Read more about java programs at:
https://brainly.com/question/19271625
What is problem scoping
Answers
Answer:
the process that people use to figure out what problem they’re solving
Explanation:
How electrical current manifests itself?
Thermal
Mechanic
Magnetic
Radiation (electromagnetic)
All listed
Answers
Answer:
Mechianic
Explanation:
What field content is used by ICMPv6 to determine that a packet has expired?
a) Source IP address
b) Destination IP address
c) Hop Limit field
d) Traffic Class field
Answers
c) Hop Limit field.
ICMPv6 (Internet Control Message Protocol version 6) uses the Hop Limit field to determine if a packet has expired. The Hop Limit field, also known as the Time-to-Live (TTL) field in IPv4.
As a packet travels through a network, each router it encounters decrements the value in the Hop Limit field by one. If the Hop Limit field reaches zero, it indicates that the packet has exceeded the maximum allowed number of hops and is considered expired. At this point, the router discards the packet and an ICMPv6 Time Exceeded message may be generated and sent back to the source.
The Hop Limit field serves as a mechanism to prevent packets from endlessly circulating in a network and allows for efficient routing and error handling. By using the Hop Limit field, ICMPv6 can detect when a packet has reached its maximum allowed hop count and take appropriate actions to ensure efficient and reliable packet delivery.
Learn more about Hop Limit here:
https://brainly.com/question/15296530
#SPJ11
How do you change the order of the slides in your presentation in the slide pane? Copy and paste Delete Drag and drop Remove
Answers
Answer: you just drag the slide to the position you want it to be
Explanation: