Which circumstance would result in an enterprise deciding to implement a corporate WAN?
when its employees become distributed across many branch locations
when the enterprise decides to secure its corporate LAN
when the network will span multiple buildings
when the number of employees exceeds the capacity of the LAN
Answers
The circumstance that would result in an enterprise deciding to implement a corporate WAN is when its employees become distributed across many branch locations. A corporate WAN (Wide Area Network) is a network that connects multiple LANs (Local Area Networks) together over a large geographical area.
Such as across cities, countries, or even continents. It provides a secure and reliable way for employees in different locations to communicate and share resources with each other. One of the main reasons why an enterprise would decide to implement a corporate WAN is when its employees become distributed across many branch locations. As a business grows, it may expand its operations to new geographic locations, either domestically or internationally. In such a scenario, the enterprise will need a way to connect its various branch locations and enable its employees to collaborate with each other.
Implementing a corporate WAN can help solve this problem by connecting all the branch locations together, regardless of their physical distance. This enables employees to share information and communicate with each other in real-time, regardless of their physical location. A corporate WAN can also provide access to common resources such as databases, servers, and applications, thereby enabling employees to work collaboratively from any location. In summary, the implementation of a corporate WAN is essential for enterprises that have employees distributed across many branch locations. It allows for seamless communication and collaboration between employees and enables access to shared resources, regardless of physical distance.
To know more about Wide Area Network visit :
https://brainly.com/question/18062734
#SPJ11
Related Questions
Select all the correct answers.
Stephen is starting out in the networking field. He aspires to join the higher ranks later in his career. Which two options are important for
Stephen?
O polishing foundational skills
applying for expert level certifications
O completing novice-level certifications
working on one project only
O avoiding new challenges
Answers
Answer:
comlleting novice-level certifications working on one
Can someone please help me I need to turn this in my 3:00pm Eastern time
What mathematical function would you use to find Money Left Over in a spreadsheet if you had a Beginning Balance of $10000.00 and a final total of $5000.00?
Answers
Answer:
1000000000
Explanation:
What does the following if statement do?
if (num1 == Math.abs(num1))
Answers
This statement checks if num1 is equal to the absolute value of num1
For instance,
num1 = 4 and the absolute value of num1 = 4. This would run the code inside the if statement but if num1 = -1 the absolute value of num1 = 1 and the if stamtent would be skipped because -1 does not equal 1
Which of the following is NOT a method for applying the SDLC model?
ITIL
Lean
IPO
Agile
Answers
Answer:
IPO is not a mehod for applying the SDLC .
Submit your definitions for the words below:
gigabyte
intranet
pixel
telecommunication
modem
raster graphic
vector graphic
digital
GUI
Answers
Answer:
1. gigabyte- Technology branded as GIGABYTE or sometimes GIGA-BYTE; formally GIGA-BYTE Technology Co., Ltd. it is a Taiwanese manufacturer and distributor of computer hardware. Gigabyte's principal business is motherboards.
2. intranet-a computer network for sharing information, collaboration tools, operational systems, and other computing services within an organization, usually to the exclusion of access by outsiders.
3. pixel-a minute area of illumination on a display screen, one of many from which an image is composed.
4. telecommunication-the transmission of information by various types of technologies over wire, radio, optical or other electromagnetic systems.
5. modem- a combined device for modulation and demodulation, for example, between the digital data of a computer and the analog signal of a phone line.
6. raster graphic-In computer graphics and digital photography, a raster graphic or bitmap image is a dot matrix data structure that represents a generally rectangular grid of pixels (points of color), viewable via a bitmapped display (monitor), paper, or other display medium.
7. vector graphic-computer graphics images that are defined in terms of points on a Cartesian plane, which are connected by lines and curves to form polygons and other shapes.
8. digital-expressed as series of the digits 0 and 1, typically represented by values of a physical quantity such as voltage or magnetic polarization.GUI-a system of interactive visual components for computer software.
9. GUI- displays objects that convey information, and represent actions that can be taken by the user. The objects change color, size, or visibility when the user interacts with them.punineep and 15 more users found this answer helpful4.0(6 votes)
Explanation:
When I read the robotic arm datasheet, it mentions position accuracy of 50um. But often when my gripper position changes or when the finger moves, I'm not sure if I'm still getting 50um repeatability. How Do I measure the position accuracy of the Robotic arm with respect to its Tool point?
Answers
To measure the position accuracy of a robotic arm with respect to its tool point, you will need to perform a calibration procedure.
The calibration procedure involves measuring the actual position of the tool point and comparing it to the commanded position. Here are the general steps to follow for calibrating a robotic arm's position accuracy:
Mount a precision measurement device, such as a laser tracker or coordinate measuring machine (CMM), near the robotic arm's workspace.Define a series of positions that cover the robotic arm's workspace, including various orientations and distances from the measurement device.Command the robotic arm to move to each of the defined positions.At each position, use the measurement device to measure the actual position of the tool point.Compare the actual position to the commanded position to calculate the error.Repeat the process for all defined positions.Calculate the statistical metrics of the error (such as mean, standard deviation, and maximum error) to evaluate the position accuracy of the robotic arm.During the calibration process, it's important to ensure that the robotic arm is properly calibrated and adjusted, and that any external factors that could affect the measurement accuracy (such as temperature or vibration) are accounted for.Once you have performed the calibration procedure, you can use the statistical metrics of the error to determine the position accuracy of the robotic arm with respect to its tool point.
To learn more about calibration click here
brainly.com/question/13092565
#SPJ4
An apple cake recipe calls for 454 grams of apples and 50 grams of raisins. How many kilograms of fruit are needed to make 12 cakes?
Answers
Answer:
9.08
Explanation:
Because 454 divided by 50 is 9.08
A text feature that adds bold, italics, or underlining to words to emphasize them is known as what?
Answers
Cursor/Insertion Point: The cursor (also called the insertion point) is a blinking vertical bar on the screen that indicates where typed text or objects will be placed in a document.
What is the name of the text format that raises text or numbers above and to the right?
A subscript or superscript is a character (such as a number or letter) that is placed slightly below or above the normal line of text. Usually smaller than the rest of the text. Subscripts appear below the baseline and superscripts appear above the baseline.
What are the formatting options used to place the text above the normal lines of text?
You can use keyboard shortcuts to make the text appear slightly above (superscript) or below (subscript) the normal text. Select the desired text or number. , press Shift and the plus sign (+) at the same time.
To know more about Cursor/Insertion Point visit;
https://brainly.com/question/29279087
#SPJ4
So my computer has be clicking random things and opening things. It’s been happening for a few days and I want to know if it’s a hacker or something wronging with the computer (I don’t have a mouse) so it’s not auto clicking
Answers
Viruses and malware are common and can have drastically negative results on your computer and life.
You can often tell that your computer is infected because it acts weird or slow.
Active antivirus software is a good way to prevent these problems.
What does this mean?

Answers
Answer:
The network that the platform is running on is down. Wait about 30min, and then try again. You can also restart your device.
Explanation:
This used to happen to me all the time during school, but when I restarted my computer it always fixed it!
Given the table of C Code Statements, variable names and variable values, determine
the variable values after each code statement is executed.
*Image is below*
Thank you!!

Answers
The variable values after each code statement is executed goe the num1 is -2 and num2 is 1.25.
How variables are declared in C deliver an example?You will use the key-word extern to claim a variable at any place. Though you could claim a variable a couple of instances on your C program, it may be described most effective as soon as in a file, a function, or a block of code.
The = image is referred to as the undertaking operator. It is likewise viable to claim a variable and assign it a fee withinside the equal line, so in place of int i after which i = 9 you could write int i = 9 multi functional go. If you've got got multiple variable of the equal kind you could additionally claim them collectively e.g.
Read morea bout the Code :
https://brainly.com/question/4514135
#SPJ1
please help me i will award brainliest
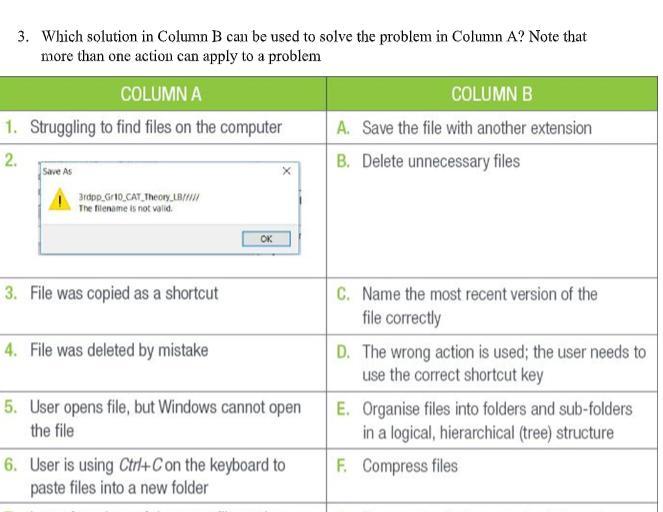

Answers
Answer: It would be option C.
Explanation: The file name is invalid, so therefore it would make sense to rename the most recent version correctly.
n
Which of the following is not a goal of a persuasive speaking?
a. to motivate to action
b.
to change attitudes, beliefs, or values
to strengthen or weaken attitudes, beliefs, or values
d. to define, demonstrate, or instruct
C.
Answers
Answer: D. to define, demonstrate, or instruct.
Explanation:
Persuasive speaking is the form of speaking that we usually engage in. It is used to convince people. As individuals, we usually engage in persuasive speaking. We argue about different things and try to convince the other person to agree with us.
Th goals of persuasive speaking is to motivate to action, to change attitudes, beliefs, or values and to strengthen or weaken attitudes, beliefs, or values.
It should be noted that the goal of persuasive speaking isn't to to define, demonstrate, or instruct. Therefore, the correct option is D.
Answer:
Simple Answer: D
Complete the sentence with the correct response.
____ filtering is the minimum function a firewall can perform and still be considered a firewall.
Answers
Packet filtering firewall is the minimum function a firewall can perform and still be considered a firewall.
What is the firewall about?Packet filtering is a basic function of a firewall that is used to control the flow of incoming and outgoing network traffic based on specified rules. The firewall inspects each incoming and outgoing network packet and either allows or blocks it based on its origin, destination, and type of data it carries.
Therefore, this kind of firewall uses rules to determine which packets to allow or block based on the packet's source and destination addresses, port numbers, and other information such as protocol type. This allows administrators to control the flow of traffic into and out of the network, and to prevent unauthorized access and potential security threats.
Learn more about firewall from
https://brainly.com/question/3221529
#SPJ1
nims was based upon the concepts originally developed for which ?
Answers
NIMS (National Incident Management System) was based upon the concepts originally developed for the Incident Command System (ICS The National Incident Management System (NIMS)
a framework used in the United States for managing and coordinating emergency response efforts. It was developed to provide a standardized approach to incident management across different jurisdictions and agencies. The concepts and principles underlying NIMS were originally developed for the Incident Command System (ICS). The Incident Command System was initially created in the 1970s in response to the need for a structured and coordinated approach to managing emergency incidents. It was designed to improve the effectiveness of incident response by establishing a clear chain of command, defining specific roles and responsibilities, and facilitating efficient communication and coordination among responding agencies.Over time, the ICS framework gained recognition and was widely adopted across the United States.
learn more about Incident here :
https://brainly.com/question/14019899
#SPJ11
why ada lovelace is known as first computer programmer ?
Answers
Answer:
Ada Lovelace, is known as the fist computer programmer because she was the one who proposed / invented computer programming.
Basically the first person to realize that the analytical engine could "perform arbitrary tasks and wrote programs for those arbitrary task, beyond computational operations."
Hope this helps :)
as the content of a marketing website for a product moves from words to photos, videos, and animation, the media richness of the site ______
Answers
As the content of a marketing website for a product moves from words to photos, videos, and animation, the media richness of the site increases.
What is media richness about?Media richness is the degree to which a communication medium can pass on numerous signals, such as tone of voice, body dialect, and visual symbolism.
As a promoting site for a item joins more visual media such as photographs, recordings, and liveliness, the sum and differing qualities of signals passed on through the location increments, driving to a better level of media lavishness.
This will improve the website's capacity to capture and keep up the audience's consideration, pass on data, and inspire feelings, possibly expanding the adequacy of the promoting campaign.
Learn more about Media richness from
https://brainly.com/question/29820040
#SPJ1
Computer programmers must be fluent in every programming language. (5 points)
O True
O False
Answers
Answer:
False, its true that they need to know some programming languages but they do not need to be fluent in all of them.
what are the characteristics of review site
Answers
- Web 2.0 techniques: Review sites may use Web 2.0 techniques to gather reviews from site users or may employ professional writers to author reviews on the topic of concern for the site
- Self-selection bias: Most review sites make little or no attempt to restrict postings, or to verify the information in the reviews. Critics point out that positive reviews are sometimes written by the businesses or individuals being reviewed, while negative reviews may be written by competitors, disgruntled employees, or anyone with a grudge against the business being reviewed. Some merchants also offer incentives for customers to review their products favorably, which skews reviews in their favor
- Reviewer characteristics: Understanding online reviewer characteristics has become important, as such an understanding can help to identify the characteristics of trustworthy reviews. Some of the characteristics that have been studied include valence, rationality, and source
- Content characteristics: The content characteristics of online consumer reviews can make them more useful to readers. Some of the content characteristics that have been studied include the tone of the review, the level of detail, and the relevance of the review to the reader's needs
- Successful owner responses: Successful owner responses to reviews can help to improve the reputation of a business. Some of the characteristics of successful owner responses include being prompt, personalized, and professional
Respond to the following questions. You can work them on papers then scan and upload it or use Math Equation Editor in Insert to type your responses directly in here. I only grade the first attempt. There will be no grades for the second or third attempts. If your response is similar or matched with any others, you and the other will both get zeros. You must include your name on each page. If I don't see your name, I might consider it is not your work and you will get a zero as well. 1. Give the function f(x)=x^2−1 a. Sketch the graph of the function. Use the graph to state the domain and the range of the function. b. Find δ such that if 0<∣x−2∣<δ, then ∣f(x)−3∣<0.2. b. Find delta such that 0
Answers
The student is required to respond to questions related to the function f(x) = x² - 1, including sketching the graph, stating the domain and range, and finding a value of delta (δ) for a specific condition.
Please solve the quadratic equation 2x² - 5x + 3 = 0.In this task, the student is asked to respond to a set of questions related to the function f(x) = x² - 1.
The first question asks the student to sketch the graph of the function and determine its domain and range based on the graph.
The second question involves finding a value of delta (δ) such that if 0 < |x - 2| < δ, then |f(x) - 3| < 0.2.
The student is required to provide their responses either by scanning and uploading their work or by using the Math Equation Editor to type their answers directly.
It is emphasized that the first attempt will be graded, and any similarities with other submissions will result in both parties receiving zeros.
Additionally, the student's name should be included on each page to ensure authenticity.
Learn more about respond to questions
brainly.com/question/31817842
#SPJ11
Why are charts and graphs included in documents rather than just raw data?
Answers
Answer:
It's more organized and easier to look at
Explanation:
If it was just the raw data, it would take more time to analize, rather than it already being in a chart or graph
This act creates a set of requirements that allow for insurance portability, significant provisions regarding "administrative simplification" and standards for "privacy and security."
a. Consumer Directed Health Plans
b. Health Insurance Portability Accountability Act
c. Healthcare Integrity and Protection Data Bank
d. Employee Retirement Income Security Act
Answers
The correct answer is: b. Health Insurance Portability Accountability Act (HIPAA).
HIPAA ensures that employees and their families who lose their job-based health insurance are able to continue their coverage through the Consolidated Omnibus Budget Reconciliation Act (COBRA). The act also introduced administrative simplification provisions to promote efficiency and cost savings in the healthcare system.
HIPAA creates a set of requirements that allow for insurance portability, includes significant provisions regarding "administrative simplification" and establishes standards for "privacy and security." The other options, such as Consumer Directed Health Plans, Healthcare Integrity and Protection Data Bank,
To know more about HIPAA visit:-
https://brainly.com/question/14308448
#SPJ11
The act that creates a set of requirements allowing for insurance portability, significant provisions regarding "administrative simplification," and standards for "privacy and security" is the Health Insurance Portability Accountability Act (HIPAA). HIPAA was signed into law in 1996 and aims to protect individuals' health information while also making it easier for them to switch health insurance plans and providers.
One significant provision of HIPAA is the establishment of national standards for electronic healthcare transactions and code sets, which aim to simplify the administrative process and reduce healthcare costs. Additionally, HIPAA created the Privacy and Security Rules, which require healthcare providers and insurance companies to protect patients' personal health information from unauthorized access and disclosure.
HIPAA also established the Healthcare Integrity and Protection Data Bank, which is a national database that tracks healthcare providers who have been convicted of fraud or abuse. Finally, while HIPAA is often associated with healthcare providers and insurers, it also has provisions that relate to employee benefits under the Employee Retirement Income Security Act (ERISA).
Overall, HIPAA is a complex law with far-reaching implications for the healthcare industry, patients, and employers.
To know more about Health Insurance Portability visit:
https://brainly.com/question/30677213
#SPJ11
Give five (5) tips on how to identify credible sources on the internet. (5pts)
Answers
1. Look for sources with authors or organizations that are experts in the field.
2. Check the source’s domain name.
3. Look for sources with a good reputation.
4. Check the source’s date of publication.
5. Look for sources with citations and references.
What is "social
comparison"?
A. When you compare your social life to others' social
life
B. When you compare your life to others' social media
posts and feel like your life is worse
C. When you compare your online posts to others'
online posts and feel like yours are worse
D. When you compare your life to others' online posts
and feel like your life is better
Answers
Answer:
A. When you compare your social life to others.
Answer:
A. When you compare your social life to others' sociallife...........
The ____ view displays the worksheet the way it will look when it prints.
A) Normal
B) Page layout
C) Break
D) Page settings
Answers
An information system is a large and highly-specialized server that hosts the database for large businesses, generally those with over 10,000 employees.
False
Answers
The given statement "An information system is a large and highly-specialized server that hosts the database for large businesses, generally those with over 10,000 employees" is False because it helps to automate time-consuming processes and provides insight into the business's operations.
What is an information system?
An information system is a set of processes, equipment, and people that collect, store, and distribute data. It aids in decision-making by providing valuable information. It's an essential component of any organization.
Examples include transaction processing systems, management information systems, decision support systems, and executive information systems.
Therefore the correct option is False
Learn more about An information system:https://brainly.com/question/14688347
#SPJ11
Question 8 of 10
What does DOS stand for?
A. Disk override system
B. Disk only system
C. Disk opening system
D. Disk operating system
Answer: D
Answers
Answer:
Dis operating system
Explanation:
refers to the original operating system developed by Microsoft for IBM
Answer:
disk
Explanation:
FREE BRAINLIEST!!!
When recording a macro, the cursor will look like a _____ to indicate it is recording. A.microphone
B. Arrow
C. CD
D. cassette tape
Answers
Answer:
B
Explanation:
Answer:
When recording a macro, the cursor will look like a cassette tape to indicate it is recording. This answer has been confirmed as correct and helpful.
Explanation:
the correct answer is D
answer john recently upgraded from windows 8.1 to windows 10, after the upgrade is complete, on the right-hand side of his desktop there is a new area that contains a way to toggle several windows features on and off, access the settings app, and view notifications. what is this area called in windows 10?
Answers
Answer:
nswer john recently upgraded from windows 8.1 to windows 10, after the upgrade is complete, on the right-hand side of his desktop there is a new area that contains a way to toggle several windows features on and off, access the settings app, and view notifications. what is this area called in windows 10?
The area in windows 10 is called the Action center
new action center which is in windows 10 you'll find app notifications and quick actions. Program alerts as well as quick actions can be contained within Window 10's new action center. Browse for the action center icon just on the taskbar.
The original action center has already been rebranded Security and Maintenance, however, it is still intact. Users still visit the site to modify their security settings. It is also s a central place wherein users can access alerts and perform actions that can ensure Windows works efficiently. This is when critical safety, as well as servicing notifications, will appear if Windows uncovers certain software or equipment problems that require user response.
learn more about Action center here: https://brainly.com/question/17827631
#SPJ4
consider a doubly-linked list with n nodes, where n is large. what is the running time required to access the second node in the list?
Answers
There is no definitive answer to this question, since it depends on the implementation of the doubly-linked list. However, in general, accessing the second node in a doubly-linked list with n nodes would take O(n) time.
What is the running time required to access the second node in the list?Since a doubly-linked list is a data structure that consists of a set of nodes that are connected together by links, the time required to access the second node in the list depends on the number of nodes in the list.
In general, the time complexity of accessing the second node in a doubly-linked list is O(n), where n is the number of nodes in the list.
Learn more about Time complexity: https://brainly.com/question/3398458
#SPJ4