you want to make sure that all users have passwords over eight characters in length and that passwords must be changed every 30 days. what should you do? answer configure account lockout policies in group policy configure expiration settings in user accounts configure day/time settings in user accounts configure account policies in group policy
Answers
You should (option) configure account policies in group policy.There are various methods and techniques that an administrator can apply in order to make the domain environment more secure. One of these methods is to configure account policies in group policy.
By doing so, the administrator can set up a password policy that requires users to create passwords that are at least eight characters in length. Moreover, the administrator can also configure a policy that forces users to change their passwords every 30 days.To configure account policies in group policy, follow these steps:
Step 1: Open the group policy management console (GPMC)Step 2: Expand the domain to which you want to apply the policy.Step 3: Right-click on the OU that contains the users and groups whose password policies you want to configure and select “Create a GPO in this domain and link it here”.Step 4: Enter a name for the policy and click OK.Step 5: Right-click on the policy that you just created and select “Edit”.Step 6: In the editor, navigate to “Computer Configuration\Windows Settings\Security Settings\Account Policies”.Step 7: You will see three password policies: “Password Policy,” “Account Lockout Policy,” and “Kerberos Policy.”Step 8: Configure the policies as per your organization's security policy.Step 9: Close the editor.The administrator can also configure the password policy settings in the following areas:
Group Policy Object Default Domain PolicyLocal Security PolicyEditorWindow Server Essentials DashboardOnce configured, the administrator can enforce the policy on the user accounts.
Learn more about password: https://brainly.com/question/27875382
#SPJ11
Related Questions
Cancico Communications has supplied the following data for use in its ABC system Overhead Costs Wages and salaries Other overhead costs $280,000 157,000 Total overhead costs $437,000 Activity Measure Activity Cost Pool Direct labour support Order processing Customer support Other Total Activity 7,955 DLHs Number of direct labour-hours Number of orders Number of customers These costs are not allocated 450 orders 200 customers to products or customers NA Distribution of Resource Consumption across Activity Cost Pools Direct Labour Order SupportProcessing Support 35% 25% Customer Wages and salaries Other overhead costs 20% 15% 30% 25°10 Other 15% 35% Total 100% 100% During the year, Cancico Communications completed an order for special telephone equipment for a new customer, Hurn Tel. This customer did not order any other products during the year. Data concerning that order follow Selling price Units ordered Direct materials Direct labour-hours Direct labour rate $221 per unit 150 units $195 per unit 0.6 DLH per unit $ 29 per DLH
Answers
1. To determine the total overhead cost for the order completed by Hurn Tel, we need to calculate the overhead cost based on the activity measures and the distribution of resource consumption across activity cost pools.
2. By multiplying the activity measures for each cost pool by the corresponding percentage of resource consumption and summing up the costs, we can obtain the total overhead cost for the order.
1. Cancico Communications has provided data on the activity cost pools and their respective activity measures, along with the distribution of resource consumption across these pools.
2. To allocate overhead costs to the order completed by Hurn Tel, we need to determine the overhead costs associated with the activity measures for direct labor support, order processing, and customer support.
3. By multiplying the activity measures (7,955 DLHs, 450 orders, 200 customers) by the corresponding percentages of resource consumption for each activity cost pool, we can calculate the overhead costs attributed to the order.
4. Summing up these costs will give us the total overhead cost for the order completed by Hurn Tel.
Learn more about overhead cost
brainly.com/question/32466347
#SPJ11
What type of cloud infrastructure delivers services based on security requirements, the mission-critical nature of the applications, and other company-established policies that supports organizations that want to maintain higher security standards for some data but have less-sensitive data that does not require intranet-level protection?.
Answers
Private cloud computing offers features like scalability and self-service that are similar to those of public cloud computing.
What is cloud infrastructure ?
The set of hardware and software components needed to enable cloud computing make up cloud computing infrastructure. It consists of computer and network resources.Through the development of cloud networks that effectively store data remotely, a cloud infrastructure engineer contributes to the development of the networks and systems needed for computer cloud systems.Public, private, hybrid, and multiclouds are the four primary categories of cloud computing. The three primary categories of cloud computing services are infrastructure as a service (IaaS), platforms as a service (PaaS), and software as a service (SaaS).Network, servers, storage, and virtualization are the four elements of cloud infrastructure that each contribute to the success of an organization's application deployment and service delivery.To learn about infrastructure refer to :
https://brainly.com/question/29745873
#SPJ1
Please help me on this it’s due now

Answers
Answer:
All of the Above
Explanation:
TDL professionals meet all of these options.
The statement that best describes the benefits of a career in transportation, distribution, and logistics (TDL) may include all of the statements.
What is TDL?TDL stands for transportation, distribution, and logistics. It is characterized as an expanding industry that mutually connects manufacturers and other companies to consumers.
According to the present times, with a huge increase in eCommerce, a strong TDL workforce is required to transport goods from one location to another safely and on time.
The benefits of a career in TDL involve professional work in a highly collaborative environment that values teamwork, professionals meet the needs of consumers across the globe, and there are several opportunities to solve unique problems in the TDL industry.
Therefore, the statement that best describes the benefits of a career in transportation, distribution, and logistics (TDL) may include all of the statements.
To learn more about Transportations, refer to the link:
https://brainly.com/question/27667264
#SPJ7
Write a pseudocode algorithm that uses the For Each loop to display all of the
values in the following array:
Constant Integer SIZE = 10
Declare Integer values[SIZE] = 1, 2, 3, 4, 5, 6, 7, 8, 9, 10
Answers
Here is a pseudocode algorithm that uses the For Each loop to display all of the values in the given array:
```
declare a constant integer named SIZE and set its value to 10
declare an integer array named values with SIZE elements and initialize it with the values 1, 2, 3, 4, 5, 6, 7, 8, 9, and 10
for each integer value in values do
display the value
end for
```
This algorithm first declares a constant integer `SIZE` and an integer array `values` with `SIZE` elements, initialized with the given values. It then uses a For Each loop to iterate through each value in the `values` array and display it. The loop will execute 10 times, once for each element in the `values` array.
ball.setSize(25, 75);
What does 25 represent in the example above?
1. The SPEED of the ball
2. The WIDTH of the ball
3. The HEIGHT of the ball
4. The 'X' coordinate of the ball
Answers
Answer:
2
Explanation:
I am getting two expected errors on this code for the bottom two “public static void” lines. Can someone tell me how I can fix it? Thanks

Answers
Answer:
Declare variable b in both lines
i.e. int b
Explanation:
In the given code, the parameters of both functions were not properly declared.
When listing the parameters, the data type must be clearly stated for all parameters (individually)
In the declaration of both functions, only variable a is declared as integer while b is undeclared.
So, the correction is to declare b as integer
________________are programs that designed to help users to be more productive with their personal tasks
Answers
Have a nice day
Answer:
Application software
Application software consists of programs designed to make users more productive and/or assist them with personal tasks
Explanation:
A photograph is created by what
A) Silver
B) Shutters
C) Light
4) Mirror
Answers
A photograph is created by Light.
What are photographs made of?Any photograph created is one that is made up of Support and binders.
The steps that are needed in the creation of a photograph are:
First one need to expose or bring the film to light.Then develop or work on the imageLastly print the photograph.Hence, for a person to create a photograph, light is needed and as such, A photograph is created by Light.
Learn more about photograph from
https://brainly.com/question/25821700
#SPJ1
please elp i will give you brainelst answer the question and answer please!!!!!!!!!!!!!!!!
I GIVE YOU BRAINELST 5 STARS AND HEART!!!!

Answers
Answer:
I'd so like one of the Presidents.
Explanation:
research some facts. make sure to use your resources. Put some facts on who their vice president was a stuff
Spreadsheet functions are____
that perform specific calculations. Formulas are always preceded by ___

Answers
Spreadsheet functions are pre-written formulas that perform specific calculations. Formulas are always preceded by an equal sign (=).
What is a Spread Sheet?A spreadsheet is a computer program that allows you to compute, organize, analyze, and save data in tabular form. Spreadsheets were created as electronic counterparts to paper accounting spreadsheets. The software runs on data entered into table cells.
Spreadsheets are a vital tool in business and accountancy. They can be of varying complexity and used for a variety of purposes, but their fundamental function is to organize and categorize data into a logical structure. Once you've placed this information into the spreadsheet, you may utilize it to help manage and expand your business.
Learn mroe about SpreadSheet:
https://brainly.com/question/10509036
#SPJ1
can I run crisis remastered on max settings?
Answers
Yes....................................
alice sends a message to bob that is intercepted by trudy. which scenario describes an availability violation?
Answers
An availability violation scenario in the given context would be if Trudy intercepts Alice's message and prevents Bob from receiving it, causing a disruption in the communication between Alice and Bob.
Availability is one of the fundamental principles of information security that ensures timely and uninterrupted access to data and resources by authorized users. In the given scenario, if Trudy intercepts the message sent by Alice to Bob, it results in an availability violation because Bob is unable to receive and access the message as intended.
Availability violations can occur through various means, such as network disruptions, denial-of-service attacks, unauthorized access, or interception by malicious actors. In this case, Trudy's interception disrupts the availability of the communication channel between Alice and Bob. The message intended for Bob is no longer accessible, leading to a violation of the availability principle. To maintain availability, it is essential to protect the communication channels, ensure secure transmission, and implement measures to prevent unauthorized interception and disruptions.
Learn more about communication channels here:
https://brainly.com/question/25630633
#SPJ11
List two building techniques or materials that should be considered if you are building in Tornado Alley.
Answers
[SPECIAL]>>>WRITE THIS TEXT IN BINARY CODE
![[SPECIAL]>>>WRITE THIS TEXT IN BINARY CODE](https://i5t5.c14.e2-1.dev/h-images-qa/contents/attachments/CwjsCGDj3PdPdQNBFEkBp60RBAtHk7sw.png)
Answers
Answer:
in binary
01000110 01010010 01000101 01000101 00100000 01010000 01001111 01001001 01001110 01010100 01010011
THX:
01010100 01001000 01000001 01001110 01001011 00100000 01011001 01001111 01010101
Answer:
01000110 01010010 01000101 01000101 00100000 01010000 01001111 01001001 01001110 01010100 01010011
Identifies the number of useful bits delivered from the sender to the receiver. Received signal level
Answers
The term you are referring to is called the "Received Signal Level" (RSL).
RSL is a measure of the power level of a signal received by the receiver from the sender. It represents the strength or intensity of the signal at the receiver's end.The RSL is typically expressed in decibels (dB) and is used to assess the quality and reliability of the communication link. It helps in determining the number of useful bits delivered from the sender to the receiver. A higher RSL indicates a stronger signal and better transmission quality, while a lower RSL may result in a weaker signal and potential loss of data.To summarize, the Received Signal Level is a metric that measures the power level of a signal received by the receiver. It is important in assessing the quality of the communication link and influences the number of useful bits delivered. In conclusion, a higher RSL is desirable for reliable communication and data transmission.
To know more about data transmission. Visit:
https://brainly.com/question/31919919
#SPJ11
Sophia notices that the public bus she takes to get to her volunteer work is
often late. She decides to interview someone at the city planner's office to
find out why this route seems to be understaffed. How did Sophia identify a
topic of interest for an interview?
OA. She concentrated on what was affecting her.
B. She accepted the interview topic her teacher assigned.
C. She concentrated on current events.
D. She focused on a hobby.
SUBMIT
Answers
A. She concentrated on what was affecting her, seems the most correct, as the problem is affecting her.
BUT, C could also be correct too..
How do i fix this? ((My computer is on))

Answers
Answer:
the picture is not clear. there could be many reasons of why this is happening. has your computer had any physical damage recently?
Answer:your computer had a Damage by u get it 101 Battery
and if u want to fix it go to laptop shop and tells him to fix this laptop
Explanation:
Which file attribute identifies the file as having been modified since the last backup? a. Archive b. Hidden c. Encrypted d. Read-only
Answers
The file attribute that identifies the file as having been modified since the last backup is Archive. Hence, option (a) is correct.
When a file is changed, its archive attribute is turned on. This indicates to backup software that the file has been modified and should be backed up again.The archive attribute is a file attribute that can be set on files and directories. The purpose of this attribute is to provide a way for backup software to determine which files need to be backed up. When a file is changed, its archive attribute is turned on. This indicates to backup software that the file has been modified and should be backed up again.
To know more about file attribute click here,
https://brainly.com/question/32218275
#SPJ11
Question 2 (Show your steps, not only the final results.) According to the PMF table in Question 1, a bag is considered underqualified if it weights less than 47(<47). Randomly select three packages. What is the probability that at least one is underqualified ( 2 points)?
Answers
To calculate the probability of at least one underqualified package out of three randomly selected packages, we need to consider the complement rule. This rule states that the probability of an event occurring is equal to 1 minus the probability of the event not occurring. We will calculate the probability of none of the packages being underqualified and then subtract it from 1 to obtain the desired probability.
To calculate the probability of none of the packages being underqualified, we need to find the probability that each package weighs 47 or more. According to the PMF table in Question 1, the probability of a package weighing 47 or more is 0.67. Since the selection of each package is independent, we can multiply these probabilities together to obtain the probability of none of the packages being underqualified:
P(None underqualified) = 0.67 * 0.67 * 0.67 = 0.300763.
Next, we calculate the probability of at least one package being underqualified by subtracting the probability of none of the packages being underqualified from 1:
P(At least one underqualified) = 1 - P(None underqualified) = 1 - 0.300763 = 0.699237.
Therefore, the probability that at least one package out of three randomly selected packages is underqualified is approximately 0.699 or 69.9%.
Learn more about probability here: https://brainly.com/question/31355126
#SPJ11
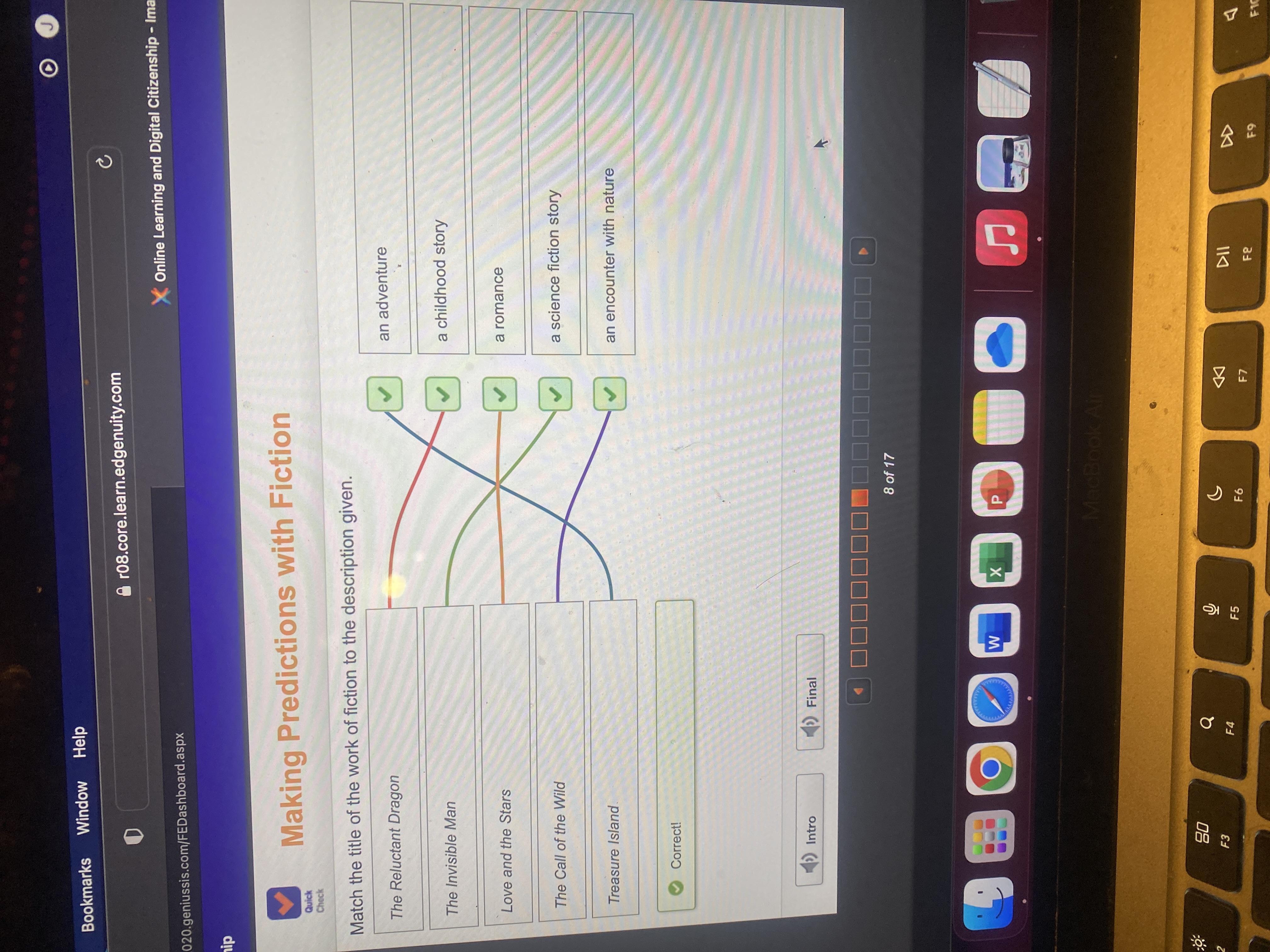
Match the title of the work of fiction to the description given.

Answers
Answer:
Explanation:
Let's get the ones that there is no dispute.
Love and the Stars Romance
The Invisible Man Science Fiction
Treasure Island An Adventure
Call of the Wild An encounter with Nature
Reluctant Dragon Childhood story.
Here's the problem.
Most ten year olds are children. They likely would like both Call of the Wild and the Reluctant Dragon as well as Treasure Island.
The Reluctant Dragon could be called science fiction.
Answer:
your welcomeee
Explanation:
is
an entire sequential game a subgame of itself?
Answers
No, an entire sequential game is not considered a subgame of itself.
In game theory, a subgame is a subset of a larger game that can be analyzed as an independent game in its own right. To qualify as a subgame, it must meet two conditions: (1) it includes a sequence of moves and outcomes that are consistent with the larger game, and (2) it must be reached by a specific history of play.
In the case of an entire sequential game, it encompasses the entire game tree, including all possible moves and outcomes. Since the concept of a subgame involves analyzing a smaller subset of the game, it is not meaningful to consider the entire game as a subgame of itself. A subgame analysis typically involves identifying a smaller portion of the game tree where players make decisions, and analyzing the strategic choices and outcomes within that subset.
Therefore, while a sequential game may contain subgames within it, the entire sequential game as a whole cannot be considered a subgame of itself.
Learn more about sequential here:
https://brainly.com/question/29846187
#SPJ11
laser printers use ___, which is a powder composed of tiny particles of ink.
Answers
Laser printers are a type of digital printing technology that use toner to create high-quality prints. Toner is a powder composed of tiny particles of ink that is used instead of liquid ink, which is used in inkjet printers.
The toner is stored in a cartridge and is transferred to the paper through a combination of heat and pressure.
The process of laser printing starts with a digital file that is sent to the printer. The printer converts the file into a series of dots and lines that represent the image or text to be printed. The drum or photoconductor is then charged with an electrostatic charge, which attracts the toner particles to its surface in the shape of the image or text to be printed.
The paper is then rolled over the drum and the toner particles are transferred to the paper through a combination of heat and pressure. Once the transfer is complete, the paper is sent through a fuser, which uses heat to melt the toner particles and fuse them onto the paper.
The result is a high-quality, sharp, and durable print that is ideal for text, graphics, and images. Laser printers are popular in offices and businesses because of their speed, efficiency, and ability to produce large volumes of high-quality prints quickly and reliably.
Learn more about Laser printers here:
https://brainly.com/question/30750534
#SPJ11
help please! I need help with this question, it’s very hard.

Answers
Answer:
1. PRINTER
2.Proj
3.USB
4.CAM
HELPPP ME PLEASEEE!!

Answers
Caroline is collaborating with several writers who are creating multiple documents. There is a single list of content that must be eventually covered by all the documents, and Caroline needs a way to “flag” which writer is covering which content; all writers will be looking at the exact same online version of the list. Describe how Caroline could quickly use colors in Word to show which content goes with which writer; be specific about which Word tool she should use and how that tool operates.
Answers
A Word document can be shared with multiple users by selecting the File menu at the top ribbon and then select Share from the drop down menu
Several writers can work together on Microsoft Word by using the co-authoring, sharing, and co-editing features in MS Word
In order to co-author the content list, Caroline, should
1. Create the content list document
2. Click on Share icon on the top right corner of the document
3. Ensure to save the document in OneDrive
4. Input the email addresses of the other writers who are working on the list
5. Enter a message to the writers to add the title of the content they are working on in the list
When the other writers open the link to the document sent to them in the email they receive, and they open the document in a web browser, by selecting Edit Document > Edit in Browser
The presence of a writer and their real time changes to the content list document, showing the content they are working on are shown by colored flags that has the author (writer) name next to the content they are working on
Learn more about collaboration in Word here:
https://brainly.com/question/1877453
what is the sdlc? describe, compare, and contrast the predictive (traditional waterfall) model and the adaptive (agile) model. [2pts]
Answers
The SDLC stands for Software Development Life Cycle. It is a framework that is used to develop software from concept to completion. The Predictive Model is a traditional Waterfall Model which is a sequential design process while the Adaptive Model (Agile) is a much more iterative process.
The predictive model involves creating a plan of action and following that plan closely. This model requires each phase of the process to be completed before moving on to the next, and the results of each phase need to be tested before the software is released.
The adaptive model involves developing the software in small chunks and then testing those chunks before the full release. This model allows for flexibility in the development process and encourages collaboration between developers, stakeholders, and users.
You can learn more about Software Development Life Cycle at: brainly.com/question/26366977
#SPJ11
When you are done reviewing in Print Preview, you have the option to save your document as a new file type. Which file type can be created using Print?
.edu
.exe
.pdf
.ppt
Answers
Answer:
the answer is pdf
Explanation:
It is because the reweing of the print
Which term is generally used to describe the ways that users can view and analyze data to help them make decisions and complete their tasks
Answers
Reporting is the system that allows users to analyze and understand data through detailed analysis.
What is reporting?Reporting is a classification system for relevant information that serves to make it accessible to users from different internal departments, according to their needs.
Characteristics of reportingThe preparation of reports is the result of a series of chained processes, which will vary depending on the objective to be achieved with the reporting.The results of the analyzes have to be able to be shared, whose conclusions reached from the analytical process are those that allow directing the taking of actions or decisions in one direction or another.Therefore, we can conclude that reporting allows users to perform searches, visualize data, prepare reports, and perform data analysis to help them make decisions.
Learn more about reporting here: https://brainly.com/question/1224013
Optimizing a network to handle more traffic by adding new specialized software is an example of ______ scaling. Adding additional nodes to a network is an example of _________ scaling.
Answers
Answer:vertical and horizontal
Explanation:
Answer:
Horizontal and then Vertical
Explanation:
Alex can't play his newest video game on his desktop computer because his video card is too slow. Alex needs to install a video card that has a faster ______, in order to play his graphics intensive games. Select the two correct answers, then click Done.
Answers
In order to play his graphics intensive games, Alex needs to install a video card that has a faster: microprocessor and graphics processing unit (GPU).
What is a video card?A video card can be defined as a printed circuit board or graphics card that is designed and developed to generate a feed of output and video signals which are sent to the display device of a computer such as a monitor.
In this scenario, Alex needs to install a video card that has a faster: microprocessor and graphics processing unit (GPU), so as to enable him to play his graphics intensive games.
Read more on video card here: https://brainly.com/question/14380167