what the meaning of Formatting marks?
Answers
Related Questions
Chief Financial Officer (CFO) has been receiving email messages that have suspicious links embedded from unrecognized senders.
The emails ask the recipient for identity verification. The IT department has not received reports of this happening to anyone else.
Which of the following is the MOST likely explanation for this behavior?
a) The CFO is the target of a whaling attack.
b) The CFO is the target of identity fraud.
c) The CFO is receiving spam that got past the mail filters.
d) The CFO is experiencing an impersonation attack.
Answers
The Chief Financial Officer (CFO) has been receiving email messages that have suspicious links embedded from unrecognized senders. The emails ask the recipient for identity verification. The IT department has not received reports of this happening to anyone else. Which of the following is the MOST likely explanation for this behavior?Answer: The CFO is the target of a whaling attack.What is whaling?Whaling is a social engineering attack on high-profile executives and senior management in organizations, as well as celebrities and other public figures.
The victim is an individual of particular importance or power within a company or organization, who has access to sensitive data. Whaling is also referred to as business email compromise (BEC).Attackers employ many of the same methods as spear-phishing but specifically target senior executives and other high-profile targets. The attack is aimed at acquiring valuable information, such as the CEO's or CFO's login credentials, employee details, and customer data, through targeted phishing. They can then use the information to gain access to the victim's systems and data.In the above scenario, since the CFO is the only person receiving such emails, it is likely that the CFO is the target of a whaling attack. The emails have suspicious links that require the recipient to provide identity verification. Attackers frequently use whaling attacks to obtain sensitive information such as account login credentials, personal information, and confidential corporate data that can be sold on the black market or used in future attacks.
To know more about whaling attack visit :
https://brainly.com/question/29971956
#SPJ11
you want to ensure that data can only be viewed by authorized users. what provides this assurance? group of answer choices integrity authentication confidentiality availability
Answers
To ensure that data can only be viewed by authorized users, confidentiality is the most important assurance. Confidentiality is the practice of limiting access to sensitive information only to those who are authorized to view it.
Confidentiality is achieved through various security measures, such as access controls, encryption, and data masking. Access controls limit access to data by requiring authentication, such as a username and password, or by restricting access to specific users or groups. Encryption is the process of encoding data so that it cannot be read by anyone who does not have the decryption key. Data masking is the process of obscuring sensitive data, such as credit card numbers or social security numbers, so that they cannot be read or accessed by unauthorized users.In addition to confidentiality, authentication is also important to ensure that only authorized users can view data. Authentication is the process of verifying the identity of a user, typically through a username and password or other form of identification. It helps to prevent unauthorized access to data by ensuring that only legitimate users can access it.To ensure that data can only be viewed by authorized users, a combination of confidentiality and authentication is necessary. These measures help to protect sensitive data from unauthorized access and ensure that only those who are authorized to view it can do so. Other components of data security, such as integrity and availability, are also important but do not directly address the issue of restricting access to data.For more such question on authentication
https://brainly.com/question/28344005
#SPJ11
While running your app in debug mode with breakpoints enabled, which command in the Debug menu and toolbar will you use to Execute one statement at a time?a.) Stop Debuggingb.) Step Outc.) Step Intod.) Continue
Answers
Answer:
c. step into
Explanation:
To execute one statement at a time while running an app in debug mode with breakpoints enabled, you would use the "Step Into" command. This command allows you to move through the code one line at a time, executing each statement and stepping into any method calls that are encountered. It is useful for closely examining the execution flow and variables at each step.
this ingredient is often used as decoration for both hot and cold dessert
Answers
Answer: cream
Explanation: Cream This ingredient is often used as a decoration or accompaniment for both cold and hot desserts, but may also be used as one of the recipe ingredients.
Please mark as brainliest
your office has been sharing an inkjet printer connected to a pc with very limited resources. they ask you to upgrade the printer, so you decide to get a laser printer that has a built-in nic (network interface card). what type of printing will you set up
Answers
To utilize the new laser printer with a built-in NIC, you would set up network printing.
What is network printing?Network printing refers to the ability to print to a printer from multiple devices on a network without the need for a direct physical connection to the printer.
Network printing allows multiple devices on the network to access and print to the printer without the need for a direct physical connection to the printer. This setup would be more efficient and convenient than the previous configuration, as it would eliminate the need for the PC to act as a print server and allow all devices on the network to print to the printer directly.
Learn more about network printing on:
https://brainly.com/question/29351223
#SPJ1
A command is
A) a sentence the provides information.
B)an order you give the computer verbally.
C) a word that is open for interpretation.
D) a one-word instruction that has been assigned meaning.
Answers
Answer:
D
Explanation:
Transferring data from a remote computer to a local computer is .....
Answers
The answer is uploading
which return value of the jfilechooser object's showopendialog method indicates that a file was chosen by the user at run time?
Answers
The return value of the JFileChooser object's showOpenDialog method that indicates a file was chosen by the user at runtime is "JFileChooser.APPROVE_OPTION."
The showOpenDialog method presents a file chooser dialog to the user and waits for the user to make a selection.
1. Create a JFileChooser object: `JFileChooser fileChooser = new JFileChooser();`
2. Call the showOpenDialog method on the fileChooser object: `int returnValue = fileChooser.showOpenDialog(parentComponent);`
3. Check if the returnValue is equal to JFileChooser.APPROVE_OPTION, which indicates that a file was chosen: `if (returnValue == JFileChooser.APPROVE_OPTION) { /* File was chosen */ }`
In this scenario, if the returnValue is equal to JFileChooser.APPROVE_OPTION, it means that the user has selected a file during runtime.
To know more about JFileChooser visit: https://brainly.com/question/16345599
#SPJ11
6.6 Code Practice 2- Boat:
Use the code above to write a program that draws an image of a boat on water. Your program should create an image similar to the one below. Your image does not need to be exactly the same as the one above, but can have slight modifications (for example, your image can use a different color or different positioning of
objects).
(In edhesive please)
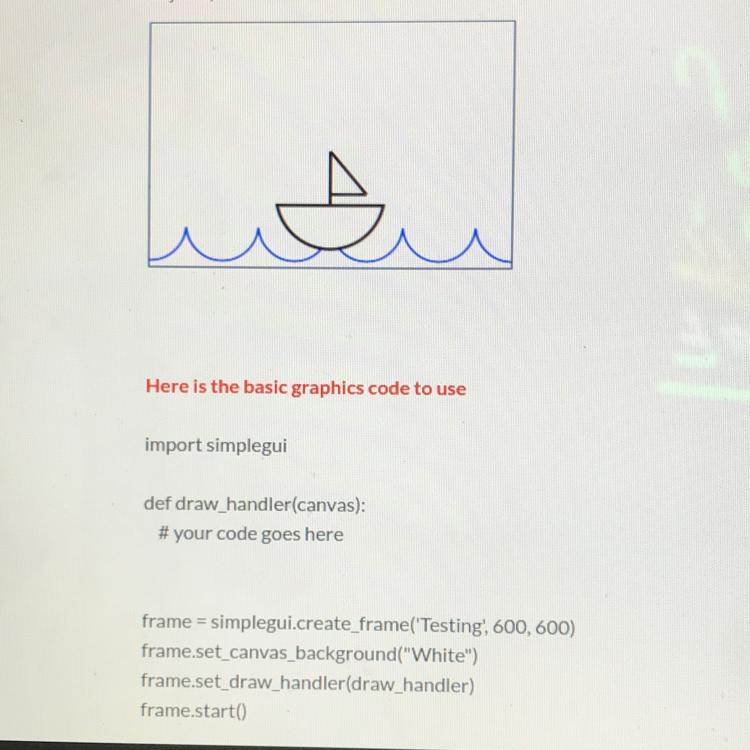
Answers
Answer:
import simplegui
def draw_handler(canvas):
canvas.draw_circle((0,550), 2, 100, "Blue")
canvas.draw_circle((100,550),2,100,"Blue")
canvas.draw_circle((200,550),2,100,"Blue")
canvas.draw_circle((300,550),2,100,"Blue")
canvas.draw_circle((400,550),2,100,"Blue")
canvas.draw_circle((500,550),2,100,"Blue")
canvas.draw_circle((600,550),2,100,"Blue")
canvas.draw_polygon([(0,550), (600,550), (600,500), (0,500)], 5, "White", "White")
canvas.draw_circle((300, 525), 2, 100, "Black")
canvas.draw_polygon([(250, 525), (350,525), (350, 475), (250, 475)], 5, "White", "White")
canvas.draw_line((250,525), (350,525), 5, "Black")
canvas.draw_line((300,525), (300, 500), 5, "Black")
canvas.draw_polygon([(300,500), (325, 500), (300,450)], 5, "Black")
frame = simplegui.create_frame('Testing', 600, 600)
frame.set_canvas_background("White")
frame.set_draw_handler(draw_handler)
frame.start()
Explanation:
Little jank but looks fine
The Internet is a(n) ______
made up of wires, cables, satellites, and rules for exchanging information between computers connected to the network.
A. Physical network
B. Virtual network
C. Multimedia interface
D. Domain name
Answers
Answer:
The Internet is a(n) B. Virtual network made up of wires, cables, satellites, and rules for exchanging information between computers connected to the network.
Explanation:
How touse the provided registry files to determine the ipv4 address of the system
Answers
The IPv4 address of the system. Please note that modifying the Windows Registry requires caution, as making incorrect changes can adversely affect the system's functionality.
To use the provided registry files to determine the IPv4 address of the system, you can follow these steps:
1. **Accessing the Registry**: Press the Windows key + R on your keyboard to open the "Run" dialog box. Type "regedit" (without quotes) and press Enter. This will open the Windows Registry Editor.
2. **Navigate to the Registry Key**: In the Registry Editor, navigate to the following key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces
3. **Finding the IPv4 Address**: Under the "Interfaces" key, you will find several subkeys, each representing a network adapter on your system. Expand each subkey and look for the one with values related to IPv4 settings, such as "IPAddress" or "DhcpIPAddress". The corresponding values will display the IPv4 address associated with that network adapter.
4. **Record the IPv4 Address**: Once you have found the appropriate subkey with the IPv4 address values, note down the IP address listed in the "IPAddress" or "DhcpIPAddress" value. This value represents the IPv4 address of the system.
By following these steps, you can use the provided registry files to locate the IPv4 address of the system. Please note that modifying the Windows Registry requires caution, as making incorrect changes can adversely affect the system's functionality.
Learn more about Windows Registry here
https://brainly.com/question/17200113
#SPJ11
11.6 Code Practice edhesive
Answers
Answer:
This is not exactly a copy paste but required code IS added to help
<html>
<body>
<a href=" [Insert the basic www wikipedia website link or else it won't work] ">
<img src=" [I don't believe it matters what image you link] "></a>
</body>
</html>
Mainly for the Edhesive users:
I received a 100% on Edhesive 11.6 Code Practice
The program for html code for the 11.6 code practice edhesive can be written in the described manner.
What is html element?HTML elements are a component of html documents. There are three kines of html elements viz, normal elements, raw text elements, void elements.
The html code for the 11.6 code practice edhesive can be written as,
<html>
<body>
<a href="https:/website-when-image-clicked.com">
<img src="https://some-random-image"></a>
</body>
</html>
Hence, the program for html code for the 11.6 code practice edhesive can be written in the described manner.
Learn more about the code practice edhesive here;
https://brainly.com/question/17770454
what is the minimum number of years over which computers may be depreciated under macrs?
Answers
Under MACRS (Modified Accelerated Cost Recovery System), the minimum number of years over which computers may be depreciated is five years.
MACRS is a tax depreciation system used in the United States for recovering the costs of tangible assets, including computers, used in a business or income-producing activity. It assigns specific recovery periods or classes to different types of assets. Computers fall under the "5-year property" class, which means they are depreciated over a period of five years. This means that businesses can claim annual depreciation deductions for computers over the course of five years, spreading out the cost of the asset over its useful life.
Learn more about MACRS here:
https://brainly.com/question/29220994
#SPJ11
Where can agent logging be turned on in the Admin Console in order to troubleshoot how the Cleanup Agent is functioning?
Answers
To troubleshoot how the Cleanup Agent is functioning and turn on agent logging in the Admin Console, follow these steps:
1. Open the Admin Console: First, you need to access the Admin Console of your system or application. This is typically a web-based interface where administrators can manage settings, users, and monitor system performance.
2. Locate the Agent Settings: Within the Admin Console, navigate to the section where you can manage agents, which are responsible for various tasks within the system, including the Cleanup Agent.
3. Find the Cleanup Agent: Search for the Cleanup Agent within the list of agents. The Cleanup Agent is responsible for removing unnecessary or temporary data from the system to maintain optimal performance.
4. Enable Logging: In the settings or configuration options for the Cleanup Agent, look for an option to enable logging. This will allow the system to record detailed information about the Cleanup Agent's activities, which can be useful for troubleshooting.
5. Save Changes: After enabling logging for the Cleanup Agent, make sure to save your changes in the Admin Console. This ensures that your updated settings take effect.
6. Review Log Files: Once logging is enabled, you can access and review the log files generated by the Cleanup Agent. These files will provide valuable insight into the agent's activities and help you troubleshoot any issues that may arise.
Learn more about troubleshoot here:
https://brainly.com/question/29736842
#SPJ11
In cell K26, create a formula that counts the number times "Thunder" occurs in the columns containing "Names"
I would wanna know the Formula for this In Excel
Answers
Answer:
I1 to K2: Use a formula to link the cells. Create a formula in column L that calculates the averages for each matching category in K2:
hope it's help you plz mark as brain listFollowing are the excel formula to count the number of times "Thunder" occurs in the names column:
Excel formula to count the number of times the value occurs:Formula:
=COUNTIF(C:C,C8)
Explanation of the Formula:
The COUNTIF function in Excel is a built-in function that counts cells according to several criteria. "=COUNTIF" is how it's spelled. The "COUNTIF" is a statistical function that can be used to count the number of cells that meet a requirement, like the number of times a certain city occurs in a client list.Inside the "COUNTIF" method we pass a two-parameter, in which the first parameter selects the column and the next parameter finds the value that will occur the number of times.Find out more about the excel function here:
brainly.com/question/20497277


What is the largest risk of a business selling its products or services on account?
Answers
Answer:
financial risk
Explanation:
they don't know if the product will work
Do the lengths of 10,4 and 5 form a triangle explain why please I’m confused
Answers
Answer:
no
Explanation:
Imagine having sticks of these lengths. Attach the 4 and 5 to both ends of the 10. No way you can have them touch each other, not even when the triangle is flat.
The 4 and 5 add up to 9, that is less than 10.
The Triangle Inequality Theorem states that the sum of any 2 sides of a triangle must be greater than the measure of the third side.
Which of the following statements are true regarding Moore’s Law? Select 3 options. A. Moore’s Law can be applied to processing advances in general and not just the miniaturization of transistors and chips. B. Moore’s Law was accurate until about 1998, when computing advances slowed drastically. C. The accuracy of Moore’s Law is being affected by the difficulty of making increasingly smaller components at the same rate. D. Moore’s Law is expected to continue at the same rate, even with the introduction of quantum computers. E. Gordon Moore, a co-founder of Intel, described Moore’s Law in 1965.
Answers
Answer: Which of the following statements are true regarding Moore’s Law? Select 3 options.
Explanation:
• The accuracy of Moore’s Law is being affected by the difficulty of making increasingly smaller components at the same rate.
• Gordon Moore, a co-founder of Intel, described Moore’s Law in 1965.
• Moore’s Law can be applied to processing advances in general and not just the miniaturization of transistors and chips.
Statement that can be considered as true statement about Moore’s Law is C:The accuracy of Moore’s Law is being affected by the difficulty of making increasingly smaller components at the same rate.
Moore's law can be regarded as an observation that was made by Gordon Moore, which explains that there is always a double increase in number of transistors in a dense integrated circuit in every two years.However, this law has it's shortcomings because of the difficulty of producing smaller components at the same rate.Therefore, option C is correct.
Learn more at,:
https://brainly.com/question/15018447?referrer=searchResults
which type of attack is wep extremely vulnerable to?
Answers
WEP is extremely vulnerable to a variety of attack types, including cracking, brute-force, IV (Initialization Vector) attack, and replay attack.
What is Initialization Vector?An Initialization Vector (IV) is a random number used in cryptography that helps to ensure the uniqueness and randomness of data used in an encryption process. The IV is typically used as part of an encryption algorithm, where it is combined with a secret key to encrypt a message. The IV is unique for each encryption session, and must be unpredictable and non-repeating. A good IV should not be reused across multiple encryption sessions, and it should be kept secret from anyone who does not have access to the decryption key. Without a good IV, a cryptographic system can be vulnerable to attacks such as replay attacks, where an attacker can gain access to the system by repeating an encrypted message.
To learn more about Initialization Vector
https://brainly.com/question/27737295
#SPJ4
(576)8. In to ( )16 ( )8
Answers
Answer:
around ()72381 approx
Explanation:
approximately not accurate
It is the "executable" phrase of Word
Wide Web with dynamic applications,?
Answers
Answer:
It is the “executable” phrase of Word Wide Web with dynamic applications, interactive services, and “machine-to-machine” interaction. In Web 3.0, computers can interpret information like humans and intelligently generate and distribute useful content tailored to the needs of users.
A mechanic uses a screw driver to install a ¼-20 UNC bolt into a mechanical brace. What is the mechanical advantage of the system? What is the resistance force if the effort force is 5 lb.
Answers
Answer:
15.7 ; 78.5
Explanation:
Mechanical advantage of a screw = Circumference / pitch
Circumference = pi × d
Where :
pi = 3.142, D = diameter
Therefore ;
Circumference = 3.142 × (1/4) = 0.785 in
Pitch = 1/TPI
TPI (thread per inch) = 20
Pitch = 1/ 20 = 0.05
Mechanical advantage = 0.785 / 0.05 = 15.7
Resistance force if effort force is 5lb
Mechanical advantage = Fr / Fe
Fe = effort force, Fr = resistance force
15.7 = Fr / 5
Fr = 15.7 × 5 = 78.5 lbs
Which of the following is a text file that a website stores on a client's hard drive to track and
record information about the user?
Cookie
Certificate
Mobile code
Digital signature
Answers
The option that is a text file that a website stores on a client's hard drive to track and record information about the user is option A: Cookie.
In computer language, what exactly is a cookie?A cookie is a piece of information from a website that is saved in a web browser for subsequent retrieval by the website. Cookies are used to let a server know whether visitors have visited a specific website again.
Therefore, Computer cookies are small files that web servers send to browsers and frequently contain unique identifiers. Each time your browser requests a new page, the server will receive these cookies. It enables a website to keep track of your online preferences and behavior.
Learn more about Cookie from
https://brainly.com/question/14252552
#SPJ1
PLEASE HURRY!!!! Look at the image below!

Answers
Answer:
print()
The print() function prints the programs message to the screen, or other standard output devices, I hope that this helps (◠‿◠)
Answer: i think it is input
Explanation:
because the word input means to put in something or operate
Explain the main differences between a short-term and long-term scheduler.
Answers
The main difference between short-term and long-term scheduler lies in their functions and the duration of the tasks they perform.
A short-term scheduler, also known as a CPU scheduler, is responsible for selecting which process in the ready queue should be executed next and allocating CPU time to it. Its primary function is to balance the system's resources and ensure optimal utilization of the processor. The short-term scheduler typically executes several times per second and works with a very small amount of information.
On the other hand, a long-term scheduler, also known as an admission scheduler, is responsible for deciding which processes should be admitted into the system's memory from the pool of processes waiting to be executed. Its primary function is to balance the system's resources over the long-term, keeping in mind the overall performance of the system. The long-term scheduler typically works with a much larger pool of processes and runs only once every few minutes or even hours.
The short-term scheduler operates on the already admitted processes, whereas the long-term scheduler determines which processes are eligible to be admitted into the system. Short-term schedulers make decisions based on the current state of the system, while long-term schedulers consider the historical and projected state of the system. In conclusion, both short-term and long-term schedulers are critical components of the operating system, and their distinct functions complement each other to ensure efficient system performance.
know more about primary function here:
https://brainly.com/question/22340031
#SPJ11
Use this option to view your presentation as your audience will see it. a.File menu b.Play button c.Slide Show button d.Tools menu
Answers
Answer:
C. Slide Show Button
Explanation:
Slide show button is used to view the presentation. It is used when presenting the matetial in the form of slides to the audience. You can add various text, images in your slides and also add animation to your slides. In order to view how these slides and animations applied on slides will look and how they will be seen by the audience during presentation, you can use this slideshow option. Slideshow button can be used from quick access toolbar or you can use F5 key to start the slideshow of your presentation or you can select Slide Show view command at the bottom of the PowerPoint window. This is used to start a presentation from the first slide or even from current slide. This is useful in customizing the slides, visualizing and analyzing the slides making changes or adding slides in the presentation.
Answer:
Your answer is C. Slide Show Button.. Hope this helps!
Explanation:
An information system is a large and highly-specialized server that hosts the database for large businesses, generally those with over 10,000 employees.
False
Answers
The given statement "An information system is a large and highly-specialized server that hosts the database for large businesses, generally those with over 10,000 employees" is False because it helps to automate time-consuming processes and provides insight into the business's operations.
What is an information system?
An information system is a set of processes, equipment, and people that collect, store, and distribute data. It aids in decision-making by providing valuable information. It's an essential component of any organization.
Examples include transaction processing systems, management information systems, decision support systems, and executive information systems.
Therefore the correct option is False
Learn more about An information system:https://brainly.com/question/14688347
#SPJ11
Who is responsible for providing the equipment employees need to stay safe on the job (like a hardhat or safety
goggles)?
• the Occupational Safety and Health Administration (OSHA)
O the employer
the labor union
O the employee
MacBook Pro
Answers
Answer:
the employer
Explanation:
Answer:
the employer
Explanation:
What terminals of the 9-pin diagnostic connector are connected to a digital multimeter (DMM) to check the resistance of the terminating resistors used for the CAN bus
Answers
To check the resistance of the terminating resistors used for the CAN bus, you would connect the digital multimeter (DMM) to terminals 6 and 14 of the 9-pin diagnostic connector. These terminals are the CAN_H and CAN_L pins, respectively.
To perform the resistance check, first ensure that the CAN bus is not powered and that all devices are disconnected from the bus. Then, set the DMM to measure resistance and touch the probes to the appropriate pins on the diagnostic connector. The typical resistance value for the terminating resistors on a CAN bus is 120 ohms. If the DMM measurement is significantly different from this value, then there may be an issue with the terminating resistors that could cause communication problems on the CAN bus.
To learn more about resistance; https://brainly.com/question/24119414
#SPJ11
An Internet Service Provider (ISP) is a company that builds the routers and wired connections that allow individuals to access the Internet.
An ISP is considering adding additional redundant connections to its network. Which of the following best describes why the company would choose to do so?
A. It costs less to design a network that is redundant
B. The protocols of the Internet only work on networks that are redundant
C. Redundant networks are more reliable
D. Adding additional connections reduces the fault-tolerance of the network
Answers
Answer:
The answer is C
Explanation:
A redundant network is more reliable as having redundancy provides a backup for when a part of a network goes down.
The best describes why the company would choose to do so is redundant networks are more reliable. The correct option is c.
What is an Internet Service Provider (ISP)?An Internet Service Provider is a business that provides services for using and accessing the Internet (ISP). ISP offers internet services to its clients so they can connect to the internet and the rest of the world.
A public Wi-Fi provider, however, is simply a router that distributes Internet service provider (ISP) services to other users. A network, it should be mentioned, is a link between other networks, computers, etc. However, a network cannot offer services for using and connecting to the internet.
The client's ISP sends a signal over the internet, which is modulated and demodulated using a modem.
Therefore, the correct option is c. Redundant networks are more reliable.
To learn more about Internet Service Provider (ISP), refer to the link:
https://brainly.com/question/18000293
#SPJ2