Which of the following statements for a JTextField is false?
a. Can be used to display uneditable text.
b. Can be used to display editable text.
c. Enables users to enter data from the keyboard.
d. Displays a list of fields.
Answers
The false statement for a JTextField is "d. Displays a list of fields."
A JTextField is a graphical component in Java Swing that allows users to enter and edit text. It is commonly used for inputting or displaying single-line text.
Statement a. is true - a JTextField can be used to display uneditable text by setting its "editable" property to false.Statement b. is true - a JTextField can be used to display editable text that users can modify.Statement c. is true - a JTextField enables users to enter data from the keyboard.However, statement d. is false - a JTextField does not display a list of fields. It is designed for single-line input or display of text, not for displaying multiple fields or lists.
Therefore, the false statement is "d. Displays a list of fields."
You can learn more about JTextField at
https://brainly.com/question/15737823
#SPJ11
Related Questions
Which of the following represent advantages of GPL-licensed software? Check all of the boxes that apply
It is always free of cost.
It allows the source code to be modified.
It can be redistributed by the user.
It can be included in proprietary software.
It can be modified and re-sold as proprietary software.
Answers
Open source software can be copied, modified, and redistributed under the provisions of the GNU Public Licence, sometimes known as the GNU GPL or just the GPL. Thus, option A,C is correct.
What best define about GPL-licensed software?Both apply whether the program is given out or purchased. Software must come with either a copy of the source code or explicit directions on how to obtain one.
Therefore, Because it cannot be used with proprietary software, the GPL is referred to be a “strong” licence. Any copies of the software that are distributed must be licensed under the GPL, and the GPL requires that all modifications to the original source code be disclosed.
Learn more about GPL here:
https://brainly.com/question/6645210
#SPJ1
Answer:B,C
Explanation:
IM JUST SMART
what is the main reason parallel processing is sometimes used for data mining? because the hardware exists in most organizations and it is available to use because the most of the algorithms used for data mining require it because of the massive data amounts and search efforts involved because any strategic application requires parallel processing
Answers
Main reason parallel processing is sometimes used for data mining is because of the massive data amounts and search efforts involved.
By parallel processing, what do you mean?The use of two or more processors (CPUs) simultaneously to handle various components of a single activity is known as parallel processing. A program's execution time can be slashed by dividing up a task's many components among several processors.
What exactly is data mining?Data mining, commonly referred to as knowledge discovery in data (KDD), is the act of sifting through huge data sets to find patterns and other important information. Data mining types
Analytical data mining that is predictive.Data mining analysis that is descriptive.To know more about data mining visit
brainly.com/question/14080456
#SPJ4
question 10 a data analyst is studying weather data. they write the following code chunk: bias(actual temp, predicted temp). What will this code chunk calculate?
Answers
A data analyst is studying weather data. They write the following code chunk: bias(actual temp, predicted temp). What this code chunk calculate is: The average difference between the actual and predicted values.
What is a Code Chunk?
A code chunk is a piece of R code that can be run. Calculations will be re-run if the document is reproduced. The code chunk technique is advantageous because it reduces the chance of a mismatch between the comments in a publication and the findings being discussed.
You may enter an R code chunk using the Insert button in the RStudio toolbar or the keyboard shortcut Ctrl + Alt + I (Cmd + Option + I on macOS).
Chunk issues can be resolved by departing and reentering the world, as well as disconnecting and reconnecting/reloading the server.
Learn more about code chunks:
https://brainly.com/question/29370173
#SPJ1
Which sphere is responsible for climate change?
Answers
Answer:
troposphere sphere
Explanation:
contains 99% (by weight) of the total atmosphere. C02 is water soluble and continuously washed during rain. some c02 is also getting dissolved in surface water. A big percentage is trapped during photosynthesis.
vertical distribution pertains to the previous ones stated, in which the different tiers correlate directly with the logical arrangement of programs; place logical different components on different machines. 1 point true false
Answers
True. Vertical distribution in software architecture refers to the practice of organizing different logical components or tiers of a system and deploying them on separate machines.
This approach aims to align the physical infrastructure with the logical arrangement of programs, enhancing scalability, modularity, and performance optimization.
By vertically distributing components, each machine can focus on specific responsibilities, leading to efficient resource utilization and improved management of the system's overall functionality. This distribution can be based on the different tiers of an application, such as presentation, business logic, and data storage, or any other logical separation that aligns with the system's architecture.
For example, in a three-tier architecture, the presentation layer responsible for user interaction can be deployed on one set of machines, the business logic layer handling application processing can be deployed on another set of machines, and the data storage layer managing data persistence can be deployed on yet another set of machines. Each tier operates independently, communicating through well-defined interfaces, which promotes loose coupling and enables scalability and flexibility.
Vertical distribution offers several benefits. First, it allows each component to be optimized for its specific role. For instance, presentation layer machines can be configured with appropriate resources to handle user interface rendering and user interactions efficiently. Business logic layer machines can be optimized for processing computations and executing application-specific logic, while data storage layer machines can be optimized for data storage and retrieval performance.
Furthermore, vertical distribution facilitates scalability by allowing each component to scale independently. If the application experiences increased user traffic, additional presentation layer machines can be added to handle the load without affecting the other layers. Similarly, if the data storage requirements grow, more machines can be dedicated to the storage layer.
Moreover, vertical distribution enhances system modularity and maintainability. Each component can be developed, tested, and deployed independently, enabling parallel development efforts and easier maintenance. It also allows for component-specific updates and upgrades without impacting the entire system.
In conclusion, vertical distribution aligns the physical infrastructure with the logical arrangement of programs, placing different logical components on different machines. This approach enables better scalability, modularity, performance optimization, and maintenance of software systems. Thus, the statement that vertical distribution pertains to the previous ones stated is true.
Learn more about distribution here
https://brainly.com/question/29035741
#SPJ11
What technology that was developed in the early 1880s was used for both mining reclaiming land in the california delta?.
Answers
The technology that was developed in the early 1880s ,that was used for both mining reclaiming land in the california delta is hydraulic mining.
A type of mining known as hydraulic mining involves moving silt or displacing rock material with the help of high-pressure water jets. The resulting water-sediment slurry from placer mining for gold or tin is sent through sluice boxes to extract the gold. Kaolin and coal mining both use it.
Ancient Roman practices that employed water to remove soft subsurface minerals gave rise to hydraulic mining. Its contemporary form, which makes use of pressured water jets generated by a nozzle known as a "monitor," was developed in the 1850s in the United States during the California Gold Rush. Despite being effective in extracting gold-rich minerals, the process caused significant environmental harm due to increased flooding and erosion as well as sediment blocking water ways and covering farmland.
To know more about hydraulic mining click here:
https://brainly.com/question/13970465
#SPJ4
ways in which a computer are used in online resavation
Answers
Answer:
Explanation:
Modern GDSs typically also allow users to book hotel rooms, rental cars, airline tickets as well as other activities and tours. ... These are also used to relay computerized information for users in the hotel industry, making reservation and ensuring that the hotel is not overbooked.
programmers sometimes refer to a situation in which nothing goes wrong as the ____ case.
Answers
Answer:
Programmers sometimes refer to a situation in which nothing goes wrong as the sunny day case.
Explanation:
Please give answers between 500 words.
What have been the major issues and benefits in
Electronic Data Interchanges (EDI) and Web-Based/Internet
Tools?
Answers
The major issues and benefits of electronic data interchange (EDI) and web-based/Internet tools, such as compatibility and standardization, privacy, cost, dependence on internet connectivity, etc.,
One of the challenges of EDI is that it is ensuring compatibility between different systems and also establishing standardized formats for data exchange. It requires agreement and coordination among trading partners in order to ensure the seamless communication, while there are many benefits that include EDI and web-based tools that enable faster and more efficient exchange of information, eliminating manual processes, paperwork, and potential errors. Real-time data exchange improves operational efficiency and enables faster decision-making. Apart from this, there are many other benefits to these.
Learn more about EDI here
https://brainly.com/question/29755779
#SPJ4
When you overlay data on top of a map, you are implementing what type of business intelligence "look and feel"?
Group of answer choices
Tabular reports
Geospatial visualization
Audio-visual analytics
None of the above is correct
Answers
When overlaying data on top of a map, you are implementing geospatial visualization as a type of business intelligence "look and feel."
Geospatial visualization is the process of displaying data in a geographic context. It involves integrating data with geographic information systems (GIS) to create maps that represent various data points. When overlaying data on a map, you are essentially combining spatial data with non-spatial data to provide a visual representation of information in a geographic context. This approach allows businesses to analyze and understand patterns, trends, and relationships based on location. By visually representing data on a map, users can gain insights and make more informed decisions. Geospatial visualization is commonly used in fields such as urban planning, logistics, environmental monitoring, and market analysis, among others. It enhances business intelligence by providing a spatial perspective and facilitating the exploration and interpretation of data in relation to geographic locations.
Learn more about Geospatial here :
https://brainly.com/question/10785231
#SPJ11
Can someone help me with Unit 7 of cmu cs academy python. PLSS EMERGENCYY
Answers
Carnegie Mellon University's CMU CS Academy is an online, graphics-based computer science curriculum taught in Python.
Why is Phyton important?Python has become a data science industry standard, allowing data analysts and other professionals to do complicated statistical computations, produce data visualizations, design machine learning algorithms, handle and analyze data, and accomplish other data-related jobs.
Development time is far more essential than computer run time in today's society. Python just cannot be beat in terms of time-to-market. Python is also efficient and dependable, allowing developers to design complex programs with minimal effort.
Learn more about Phyton:
https://brainly.com/question/31768977
#SPJ1
what method does a gsm network use to separate data on a channel?
Answers
What are some scenarios where you might use the IF function in Excel?
Answers
Answer:
The IF function runs a logical test and returns one value for a TRUE result, and another for a FALSE result.
For example, to "pass" scores above 70: =IF(A1>70,"Pass","Fail"). More than one condition can be tested by nesting IF functions.
Comparison operator:
Meaning
Pam purchased video cameras for all of her employees so they can participate in videoconferencing discussion forum a webinar a screen-sharing application the same computer
Answers
Pam has purchased video cameras for her employees so they can participate in various activities such as video conferencing, a discussion forum, webinars, and a screen-sharing application.
Pam's investment is a great way to help her employees stay connected and work from home more efficiently. In this answer, I will explain how each of these activities will help Pam's employees.Video Conferencing: Video conferencing is a technology that enables people to conduct virtual meetings. Pam's employees can now attend meetings without leaving their homes. Video conferencing can increase productivity by saving time and reducing travel expenses.
Discussion forums can help employees stay motivated and engaged in their work.Webinars: Webinars are online seminars where participants can learn about a particular subject or topic. Pam's employees can participate in webinars and gain new skills that can benefit the company.Screen-Sharing Application: A screen-sharing application is software that enables people to share their computer screen with others. Pam's employees can use this software to work together on projects.
Learn more about video cameras: https://brainly.com/question/32164229
#SPJ11
Pam purchased video cameras for all of her employees so they can participate in videoconferencing, discussion forums, webinars, screen-sharing applications, and the same computer. This is a great initiative taken by the owner to make her employees capable of doing their work in an advanced manner.
Below is an explanation of how it is helpful to the employees. The video cameras purchased by Pam will help her employees to participate in various online activities like videoconferencing, discussion forums, webinars, and screen-sharing applications. Nowadays, videoconferencing and webinars are considered one of the most significant ways of communicating. This method helps people to communicate and do their work with others who are geographically distant from them.The purchased video cameras will help employees to be present in videoconferencing and webinars without leaving their place. It will save their time, and they can also participate in a meeting if they are not available physically. Similarly, discussion forums and screen-sharing applications will help employees to do their work efficiently. In screen-sharing applications, people can share their screens with others and can ask for help or can help others with their work.
To sum up, Pam's initiative to purchase video cameras for her employees is a great way to help them perform their work efficiently and effectively. Video cameras will help employees to participate in various online activities without any hurdle. Discussion forums and screen-sharing applications will help employees to collaborate with their colleagues and do their work in a better way.
To learn more about videoconferencing, visit:
https://brainly.com/question/10788140
#SPJ11
what are the constraints of mine shaft head gear
Answers
Answer:
Mine headgear constructions support wheel mechanisms for suspending winding cables that transport workers and ore up and down deep level shafts. These strange anthropomorphic structures have become the iconic symbol for mining.
Mine shaft head gear is a stationary equipment used as lift to transport miners underground and back up on earth surface.
Mine shaft head gear are also used to lift the mined ore to the surface.In essence, these lifting equipment have a wheel mechanisms for suspending winding cables which play a role of transporting for both the workers and mined ore.In conclusion, the major constraint is that the Incompetence or fault to the gear could lead to free fail and cause injury or death to the workers.
Learn more about Mine shaft head gear here
brainly.com/question/24553709
Yolanda is trying to do more networking. How does she BEST demonstrate this effort?
A.
She fills out and submits four job applications every month.
B.
She reads the newspaper every day to look at job openings.
C.
She spends hours doing internet research about jobs each week.
D.
She attends conferences quarterly to introduce herself to people.
Answers
An effective networker should utilize both of their ears and mouth in proportion.
What is meant by networking?Your ability to develop a mutually beneficial relationship will increase as you and your networking partner discover everything there is to know about one another more quickly. An effective networker should utilize both of their ears and mouth in proportion. Find ways to assist others by paying attention to their needs and problems. In 2022, communication, public speaking, active listening, confidence, and positivism will be some of the most crucial networking abilities. Some of the most helpful advice to enhance your networking is to be mindful of your body language, have a safety net, and ask open-ended inquiries. Information and ideas are shared through networking, typically in a casual social situation, between individuals who share a career or a particular interest. Therefore, the correct answer is option D. She attends conferences quarterly to introduce herself to people.
To learn more about networking refer to:
brainly.com/question/21527655
#SPJ1
Hey i need some help with code.org practice. I was doing a code for finding the mean median and range. the code is supposed to be including a conditional , parameter and loop. I'm suppose to make a library out of it and then use the library to test the code? please help!
here is the link to the code.
https://studio.code.org/projects/applab/YGZyNfVPTnCullQsVFijy6blqJPMBOgh5tQ5osNhq5c
P.S. you cant just type on the link i shared you have to click view code and then remix to edit it. thanks
Answers
Answer:
https://studio.code.org/projects/applab/YGZyNfVPTnCullQsVfijy6blqJPMBOgh5tQ5osNhq5c
Explanation:
Richard wants to share his handwritten class notes with Nick via email. In this scenario, which of the following can help Richard convert the notes into digital images so that he can share them via email? a. Bar coding device b. Digital printing software c. Document scanner d. Radio frequency identification tag
Answers
Answer: Document Scanner
Explanation: Cos then he can easily add the paper notes to his computer and email the client.
Which of the following operator(s) are overloaded by default method, if the programer does not provide one? operator= operator== operator-- All of the above None of these Class
Answers
None of these operators are overloaded by default methods. In C++, the assignment operator (operator=) and the equality operator (operator==) must be explicitly overloaded if the programmer wants to define custom behavior for these operators in a class. Similarly, the decrement operator (operator--) also needs to be explicitly overloaded if desired. If the programmer does not provide custom implementations for these operators, the default behavior will be applied, which is typically a member-wise assignment for operator=, a member-wise comparison for operator==, and a decrement of the value for operator--.
WILL GIVE BRAINLIEST!!! Danielle is warehouse supervisor for a large shipping company. Most shipments need to leave the warehouse by 3am because the drivers need to get on the road to their destinations. Danielle does not usually arrive until 4am because she has a hard time waking up. What quality does Danielle need to work on in order to complete her job successfully?
integrity
punctuality
friendliness
curiosity
PLEASE FAST!!!!!!!!
Answers
Answer:
Punctuality
Explanation:
She needs to get there earlier so that she can see the drivers out on time.
Which of the following sentences use personification 
A. The stars in the sky are bright
B. The tree had leaves of green, yellow, and brown,
C. The truck pulled the heavy trailer out of the mud.
D. The snowflakes danced through the air.
Answers
Answer:
D
Explanation:
snowflakes cant dance.Its a human things.
Explain the difference between supervised learning, unsupervised learning, and reinforcement learning.
Answers
Supervised learning relies on labeled data with predefined outputs, unsupervised learning learns from unlabeled data to discover patterns or structures, and reinforcement learning learns through interaction with an environment to maximize rewards. Each approach addresses different types of problems and requires different training methodologies and algorithms.
Supervised learning is a kind of AI where a calculation gains from named information. The dataset used for training in this method has both target outputs (labels) and input data (features), respectively. By generalizing the patterns and relationships found in the labeled examples, the algorithm learns to map the input data to the correct output. Predicting or categorizing new, unseen data accurately is the aim of supervised learning.
Unsupervised learning: Unaided learning is a sort of AI where the calculation gains from unlabeled information. In contrast to supervised learning, the training process does not provide any predefined target outputs or labels. All things considered, the calculation recognizes examples, designs, or connections inside the information all alone. Algorithms for unsupervised learning can either find underlying patterns or distributions in the data or cluster similar data points together. Exploratory analysis, data preprocessing, and uncovering hidden insights from data are all common applications of this kind of learning.
Reinforcement Learning: Support learning is a sort of AI where a specialist learns through cooperation with a climate. Based on the actions it takes in the environment, the agent receives feedback through rewards or penalties. Finding the optimal sequence of actions that maximizes the cumulative rewards over time is the objective of reinforcement learning. The agent learns to take actions that result in positive outcomes and to avoid actions that result in negative outcomes through trial and error. When an agent needs to learn how to make decisions and take action in complex, dynamic environments, reinforcement learning is frequently used.
To learn more about AI learning:
https://brainly.com/question/6974221
Which of the following is NOT a Receiver-Centered message:
A.
In order to provide you with the best service, please compile the following application.
B.
As soon as you are able to complete the claim form, we will send you a full refund.
C.
So that you may update your profile with the most current information, it is being returned to you.
D.
Our policy requires that all customers sign the disclaimer before their accounts are charged with purchases.
Answers
The option "C. So that you may update your profile with the most current information, it is being returned to you" is NOT a Receiver-Centered message.
Receiver-Centered messages are focused on the recipient or receiver of the message, emphasizing their needs, preferences, and actions. These messages are designed to be more customer-oriented and customer-centric.
Options A, B, and D in the given choices demonstrate receiver-centered messages as they directly address the recipient and their requirements or preferences.
Option C, however, does not follow a receiver-centered approach. Instead, it focuses on the action of returning the profile for the purpose of updating information. It does not directly address the recipient's needs or preferences but rather states a procedure or action being taken. Therefore, option C is not a receiver-centered message.
In summary, option C ("So that you may update your profile with the most current information, it is being returned to you") is not a receiver-centered message as it does not emphasize the recipient's needs or preferences.
Learn more about profile here:
https://brainly.com/question/31818081
#SPJ11
i cracked a school computer screen on purpose and one on accident what will happen now?
Answers
Answer:
You will probably have to pay a fee of replacement, or pay for the whole computer.
Explanation:
if you often work with plain-text documents, it is helpful to know about he linux _____ comannd for spell checking
Answers
If you often work with plain-text documents, it is helpful to know about the Linux 'aspell' command for spell checking.
Here's a step-by-step explanation:
1. Open a terminal window in Linux.
2. To check the spelling of a plain-text document, type the following command: `aspell check [filename]`, replacing [filename] with the name of your document.
3. Press Enter to start the spell checking process.
4. Aspell will highlight any misspelled words and provide suggestions for corrections.
5. Choose the appropriate correction or ignore the suggestion.
6. Once the spell checking is complete, aspell will save the corrected document.
Remember to replace 'aspell' with the specific spell-checking command you want to use, such as 'hunspell' or 'ispell', if you prefer those tools.
To learn more about plain text documents visit-
https://brainly.com/question/2140801
#SPJ11
The total number of possible keys for Data Encryption Standard (DES) is _________, which a modern computer system can break in a reasonable amount of time.
Answers
Answer:
The correct answer is "56".
Explanation:
DES has become a widely accepted process of information encryption but instead private key cryptography that utilizes one less key that is used in the encryption algorithm. This same encryption performance is strongly linked to that same size, as well as 56-bit key size is becoming too insignificant compared to that same storage advent of technology computer systems.So the answer above is completely right.
How do you fix a class, interface, or enum expected in this code
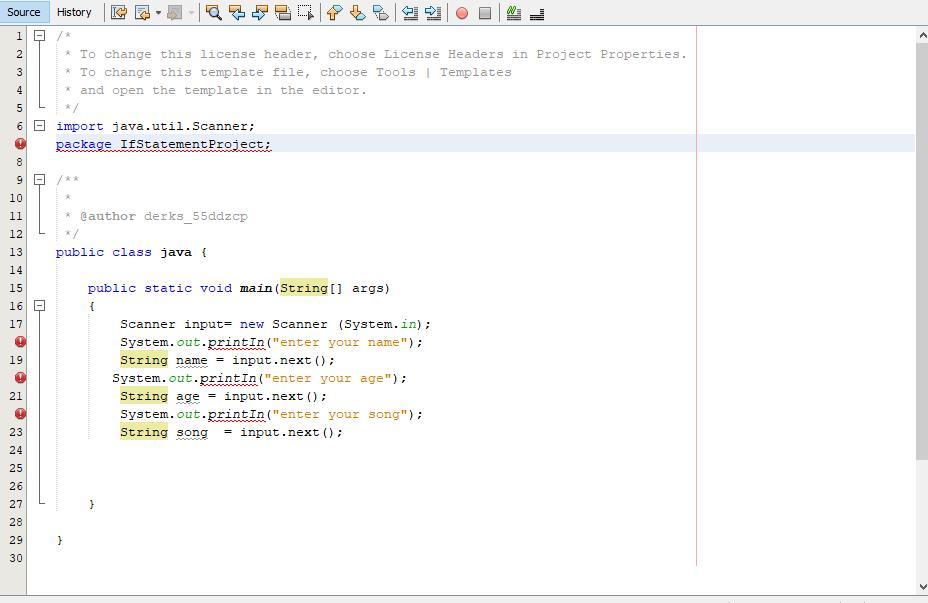
Answers
Answer:
The class interface or enum expected error is a compile-time error in Java which arises due to curly braces. ...Code. ...Here, the error can be corrected by simply removing the extra bracket, or by keeping an eye on the indentation.class Main { ...Case 2 (function outside class)
Explanation:
The first computer available for commercial sale in the United States was made by Mauchly and Eckert in what year?
1974
1947
1940
1951
Answers
Answer:
1951
Explanation:
please help it's my last question
Mention different between client / server architecture and peer to peer architecture of the network.
Answers
Explanation:
In Client-Server Network, Clients and server are differentiated, Specific server and clients are present. In Peer-to-Peer Network, Clients and server are not differentiated. ... In Client-Server Network, Centralized server is used to store the data. While in Peer-to-Peer Network, Each peer has its own data
Answer:
thanks for the point of contact
when non-numeric data is being added to a table, the data must be enclosed in ____________________ quotation marks.
Answers
When non-numeric data is added to a table, the data must be enclosed in single or double quotation marks, depending on the programming language or database management system you are using. Enclosing non-numeric data in quotation marks ensures that the system correctly identifies and processes the data as a string, rather than a numeric value or a variable.
Quotation marks help differentiate between various data types in programming languages and databases. Numeric data, such as integers and floating-point numbers, can be input without any special characters. However, non-numeric data like text or characters requires the use of quotation marks to prevent errors and maintain proper data handling.
In most programming languages and database systems, single and double quotation marks are interchangeable, but it's essential to use them consistently throughout your code or query. Some systems, like SQL, may require single quotation marks specifically for enclosing non-numeric data.
It's crucial to follow the proper syntax when working with data types, as incorrect usage of quotation marks can lead to errors or incorrect data processing. Enclosing non-numeric data in quotation marks allows for proper identification and manipulation of the data, ensuring accurate and efficient operations in your programs and databases.
You can learn more about non-numeric data at: brainly.com/question/4860917
#SPJ11