write a class called calculator.java containing two static methods. the first, torpn(), takes an array-list of tokens and returns a second list. it will implement the following algorithm:
Answers
The Calculator class in Java contains a torpn() method that takes an ArrayList of tokens and returns a second list. This method implements the Shunting-yard algorithm to convert an infix expression to postfix notation. The class also includes helper functions to determine whether a token is a number or operator, and to compare the precedence of two operators.
here is an example implementation of the Calculator class in Java, with a torpn() method that takes an ArrayList of tokens and returns a second list:
import java.util.ArrayList;
import java.util.Stack;
public class Calculator {
public static ArrayList<String> torpn(ArrayList<String> tokens) {
ArrayList<String> output = new ArrayList<String>();
Stack<String> stack = new Stack<String>();
for (String token : tokens) {
if (isNumeric(token)) {
output.add(token);
} else if (isOperator(token)) {
while (!stack.empty() && isOperator(stack.peek()) && (precedence(token) <= precedence(stack.peek()))) {
output.add(stack.pop());
}
stack.push(token);
} else if (token.equals("(")) {
stack.push(token);
} else if (token.equals(")")) {
while (!stack.empty() && !stack.peek().equals("(")) {
output.add(stack.pop());
}
stack.pop();
}
}
while (!stack.empty()) {
output.add(stack.pop());
}
return output;
}
public static boolean isNumeric(String token) {
try {
Double.parseDouble(token);
return true;
} catch (NumberFormatException e) {
return false;
}
}
public static boolean isOperator(String token) {
return token.equals("+") || token.equals("-") || token.equals("*") || token.equals("/");
}
public static int precedence(String operator) {
if (operator.equals("+") || operator.equals("-")) {
return 1;
} else if (operator.equals("*") || operator.equals("/")) {
return 2;
} else {
return 0;
}
}
}
The torpn() method implements the Shunting-yard algorithm to convert an infix expression to postfix (Reverse Polish Notation) notation. It takes an ArrayList of tokens (strings representing numbers, operators, and parentheses) and returns a second list of tokens in postfix notation. The isNumeric(), isOperator(), and precedence() methods are helper functions used by the torpn() method to determine whether a token is a number or operator, and to compare the precedence of two operators, respectively.
Note that this implementation assumes that the input expression is well-formed (e.g. has matching parentheses), and does not handle unary operators or functions.
Learn how to identify static method:https://brainly.com/question/30080467
#SPJ11
Related Questions
Describe the indicators and hazards of a metal deck roof fire in an unprotected steel joist warehouse as well as the techniques to deal with the problem.
Answers
Answer:
Explanation:
Joist mansory building is a type of building with the exterior wall of mansory, which is capable of withstanding combustion or fire for nothing less than an hour.
Therefore, the best method to deal with fire is to build with materials that are fire resistant.
Based on the information given, it's vital to make the construction with materials that are fire resistant.
Within the fire service, building construction can simply be defined as the study of how buildings can be put together. It's also how materials and connections are used.
From the information given, it's stated that the metal deck roof is in an unprotected steel joist warehouse. Therefore, in order to prevent hazard, it's important to make the construction with materials that are fire-resistant.
Read related link on:
https://brainly.com/question/17050293
Choose the correct comparison statement about delivery and read receipts.
A: Delivery receipts can be enabled for all messages, while read receipts can be turned off by the recipient.
B: Delivery receipts will notify the recipient, while read receipts will notify the sender.
C: Read receipts will prompt the sender with a pop-up message, while delivery receipts send a message to the Inbox.
D: Read receipts notify that the message was delivered, while delivery receipts notify that the message was opened.
Answers
Answer:
A: Delivery receipts can be enabled for all messages, while read receipts can be turned off by the recipient.
What strategies could you use if you came across a surplus for a computer parts store?
Answers
1. Discounts and promotions: One strategy for dealing with a surplus of computer parts is to offer deep discounts or promotional offers to customers. This can help incentivize customers to purchase more items, ultimately driving up revenue and reducing the surplus.
2. Bulk sales: Another strategy is to offer bulk sales discounts to resellers or businesses that could use multiple parts at once. This can help get rid of a surplus quickly and create valuable relationships with resellers.
3. Return policies: Consider revising the return policies. Certain policies such as removing the return policy for a select period or offering additional discount for no returns can offer a better deal to people.
4. Use marketplaces for computer parts: Another idea to liquidate the excess inventory is by selling them online on marketplaces or e-commerce platforms. By taking advantage of these platforms, the store can reach a wider audience and ensure the products reach the customers who really need them.
5. Partner with other businesses: Another strategy is to partner with other businesses that may be interested in buying the excess inventory in bulk. This can be particularly effective if the store has a relationship with a local repair shop or other tech-related business.
6. Donate to organizations: Finally, you can consider donating some of the inventory to non-profit organizations or charities that may be able to use the parts. Not only can this be a positive public relations move, but it can also potentially provide tax benefits.
How has music changed with the use of technology?
Musicians can now share their music on the World Wide Web.
Music can easily be created and edited with different applications.
Developers can include music in the background of their websites.
all of the above
please help
Answers
Answer: All of the above
Explanation:
Music like most other things, has been changed by its interaction with technology. Music for instance can now be shared on the internet to people far away from each other with services like Apple music and Tidal benefitting from this.
Different applications have also been created that can help make music from being able to create instrumentals to changing the voices of singers.
Developers are now even able to include their music in their website background as way to market their product, proof of another way music has changed due to technology.
Answer:
all of the above
Explanation:
Ejemplo la violencia no se combate con violencia
Answers
Answer:
ur right violence should not be fought by violence
but sometimes there are problems in the world
that just happens to lead with violence
Which occurs when private details of a class are hidden from other classes or parts of the program that uses instances of the class??
Answers
Answer:
Encapsulation is the concept of hiding the private details of a class from other classes or parts of the program that uses instances of the class. Encapsulation helps to protect the data within an object from being modified by code outside the object, and it also allows for the implementation of the object to change without affecting the code that uses the object. Encapsulation is often achieved in programming languages through the use of access modifiers, such as "private" or "protected," which determine which parts of the code can access the data within an object.
Explanation:
What tag is used to contain information about a web page, such as the title and related pages?
Answers
Answer:
<head>
Explanation:
correct on edge 2021
The tag that has been used for the headings and titles and the information contained in a web page is <head>.
What is a tag?A tag is given as the label that has been attached to someone or something in order to add identification to the particular thing. The tag in the HTML or any other language has been used for the conversion of the HTML document into web pages. The tags are braced in the < >.
The headings and the subheadings or titles stand for the analysis of the topic and the concern of the particular topic or subject. There was the presence of the tag such as head, meta, footer, and header.
The title and the heading to a particular subject have been the representation of the topic that has been covered in the meta description part. Thereby, the title and important information are given in the <head> tag.
Learn more about the tag, here:
https://brainly.com/question/8441225
#SPJ5
All variables are----------------------------------------------- help please
Answers
Answer:
variables are any characteristics that can take on different values, such as height, age, species I think
Answer
A variable basically works as a "placeholder" for anything that might change a majority of the time.
Examples
In science one may call a factor in a experiment that is subject to change a variable.
In math the term is used for a symbol that we do not know yet, such as x or y. Typically in math a variable is a letter.
In computer programming, variables are used to store information to be referenced and used by a computer program. They do give a way of naming data with a descriptive name as well so programs can be understood more clearly. When you go to assign values to the "variable" you are basically assigning individual variables such as the ones above in a way.
2. Say whether these sentences are True or False. a. Input is the set of instructions given to a computer to change data into information. the form of words numbers, pictures, sounds .it is true or false
Answers
Answer:
I think it is false bcz the set of instruction given to computer is program.
Explain why every email account needs a subject
Answers
Answer:
Every email account needs a subject for the following reasons:
Organization: A subject line provides a brief overview of the content of the email, helping the recipient to quickly identify and organize their emails.
Attention: An email with a clear and relevant subject line is more likely to get the recipient's attention, as they can quickly see if the email is worth their time.
Filter: Email services often have filters that sort emails based on their subject line, allowing the recipient to categorize and prioritize emails.
Searchability: A clear subject line makes it easier for the recipient to search for the email later on, particularly in the case of a large inbox.
Therefore, including a subject in an email is important for effective communication and efficient email management.
Explanation:
HOW TO USE THIS IN A STORY CAN ANYONE HELP PICK % WORD FROM THE PAGE AN MAKE A STORY WHY DO I LIKE SUMMER ?????////
get 60 piont if you if you help meeeeeeeeeeee
ASAPPPPPPPPPPPPPPPPPPPPPP
The sunshine
Light mornings
Long light nights
BBQs in the garden
The smell of sun cream
Pretty wildflowers
Cloudless blue skies
Going to the beach
Feeling the warm sun on your face
Summer clothes
Sunglasses
Picnics in the park
Long walks
Sitting out on a warm evening
Eating fresh tasty salads
Drinking sangria
Orange glowy sunsets
Fresh air
Exploring new places
Ice cream (or Dairy Free alternative)
Summer playlists
Road trips
Eating fresh strawberries
Ice cold drinks on a hot day
The smell of freshly cut grass
Not having to wear a jacket when out
Autumn is just around the corner
Holidays at home or abroad
Salty sea breezes
Summer always seems to make people happier
Answers
Answer:
Picnic in the Park
Explanation:
Parks are my favorite spots to chill or go for a stroll. Parks make walking in a neighborhood more fun and offer space for common sports, promoting physical activity. They have hiking trails and other amenities to get people moving. Every place, in my opinion, needs some green space where people can get away from the crowds. I live near a park, so if the weather is good, I usually go there once or twice a week. Therefor, my favorite summer activity is going to the park.
pr professionals use webcasts to stream press conferences and other public events over the internet to reach audiences who cannot attend the event in person.
Answers
PR professionals use webcasts to stream press conferences and other public events over the internet to reach audiences who cannot attend the event in person is true.
What is webcasts?
Webcasts is defined as a media presentation delivered via the Internet that makes use of streaming media technologies to give access to a single content source to numerous listeners and watchers at once.
A kind of strategic communication that strengthens connections between corporations and their audiences. To build, preserve, and safeguard the company's reputation, increase its status, and offer a positive picture.
Thus, PR professionals use webcasts to stream press conferences and other public events over the internet to reach audiences who cannot attend the event in person is true.
To learn more about webcasts, refer to the link below:
https://brainly.com/question/9165574
#SPJ1
Match the types of performance testing to their meanings.
spike testing
stress testing
tests system performance by increasing parameters drastically
soak testing
tests system behavior under a continuous load
tests system behavior when its capacity increases beyond the threshold
tests the performance of databases and servers
load testing
Answers
Answer:
spike,stress,soak,tests system performance by increasing parameters drastically,tests system behavior under a continuous load,tests system behavior when its capacity increases beyond the threshold,tests the performance of databases and servers
i put commas999
Explanation:
A positive integer is called a perfect number if it is equal to the sum of all of its positive divisors, excluding itself. For example, 6 is the first perfect number because 6 = 3 + 2 + 1. The next is 28 = 14 + 7 + 4 + 2 + 1. There are four perfect numbers less than 10,000. Write a program to find all these four numbers.
Answers
i = 1
while i < 10001:
total = 0
x = 1
while x < i:
if i % x == 0:
total += x
x+=1
if total == i:
print(str(i)+" is a perfect number")
i += 1
When you run this code, you'll see that 6, 28, 496, and 8128 are all perfect numbers.
rotate object while holding the shift key. what does it do?
Answers
Answer:
It rotates it 45 degrees in a direction
what are the answers for theses question?




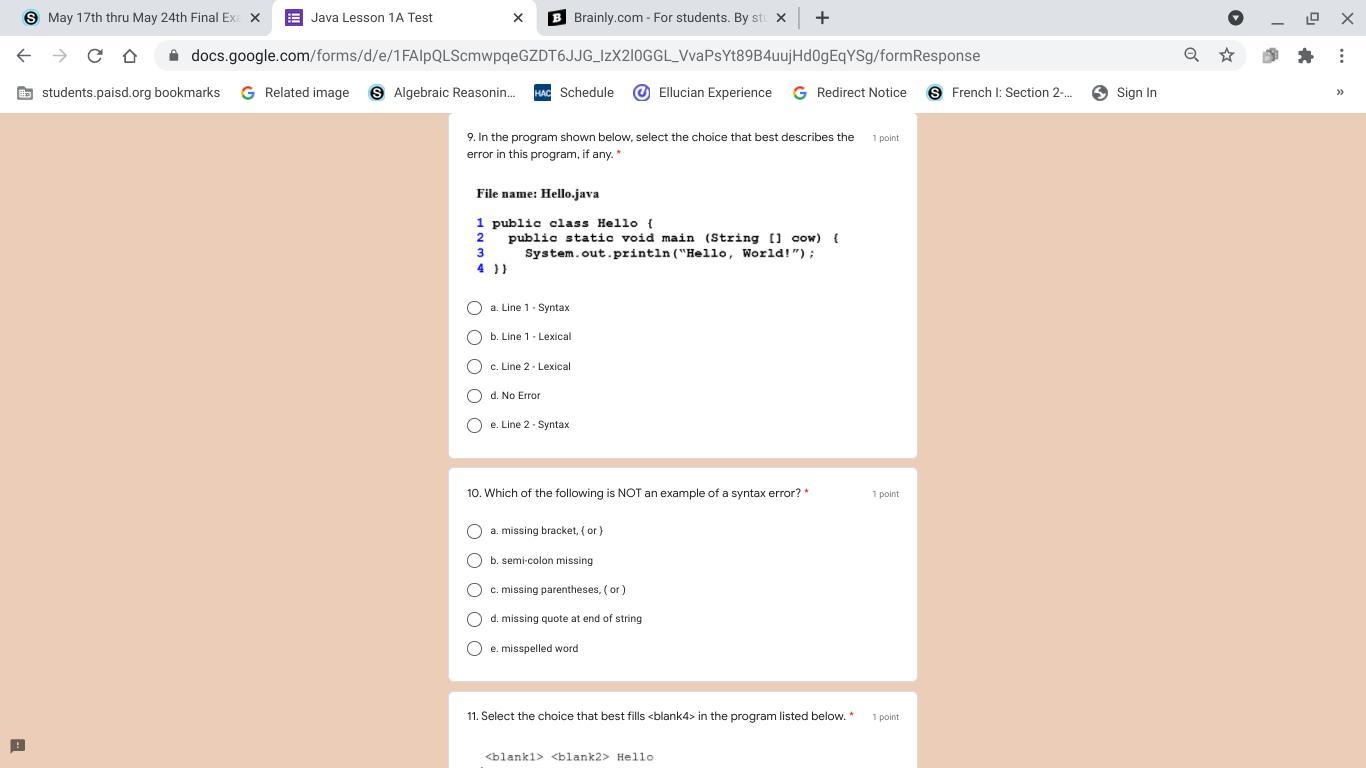
Answers
Answer: me no comprende coding
Explanation:
sorry
function of microprocessor
Answers
Answer:
The microprocessor is the central unit of a computer system that performs arithmetic and logic operations, which generally include adding, subtracting, transferring numbers from one area to another, and comparing two numbers. It's often known simply as a processor, a central processing unit, or as a logic chip.
Write a declaration that creates an Arc object that is centered at point (50, 50) and sweeps across the top half of the underlying ellipse. Base it on an ellipse with a horizontal radius of 40 and a vertical radius of 100.
Answers
Arc arc = new Arc(50, 50, 40, 100, 0, 180); This declaration creates an Arc object that is centered at point (50, 50) and sweeps across the top half of an ellipse with a horizontal radius of 40 and a vertical radius of 100.
The Arc class is commonly used in computer graphics and represents a portion of an ellipse or a circle. In this case, the start angle is 0 degrees and the sweep angle is 180 degrees, which results in the arc spanning the top half of the ellipse. The parameters specify the center coordinates, radii, and the start and sweep angles of the arc.
Learn more about ellipse here:
https://brainly.com/question/20393030
#SPJ11
PLS HELP ASAP! WILL GIVE BRANLIEST TO THE FIRST PERSON TO ANSWER. 100 points!
Use the information under the Nutrients That the Human Body Needs title to create a multilevel list. Your list should meet these requirements.
a. The first level should be the name of the nutrient.
b. The second level should contain the subheadings “Uses” and “Sources.”
c. The third level should contain the specific information about the second level.
What I did so far:
1) Carbohydrates
a)
Answers
Answer:
Carbohydrates are found in a wide array of both healthy and unhealthy foods eg potatoes, cookies, etc.
Explanation:
Answer:
1) carbohydrates
what do you mean by a)?
How to write your own consumer java.
Answers
public class ConsumerInterfaceExample {
static void printMessage(String name){
System.out.println("Hello "+name);
}
static void printValue(int val){
System.out.println(val);
}
public static void main(String[] args) {
// Referring method to String type Consumer interface
Consumer consumer1 = ConsumerInterfaceExample::printMessage;
consumer1.accept("John"); // Calling Consumer method
// Referring method to Integer type Consumer interface
Consumer consumer2 = ConsumerInterfaceExample::printValue;
consumer2.accept(12); // Calling Consumer method
}
}
(50 points) The discipline of computer science focuses on software programming. It includes learning how to develop application software, expert systems, artificial intelligence (AI), websites, embedded coding, and robotics.
A. True
B. False
Answers
Computer literacy is understanding the role of information in generating and using business intelligence. True or false?.
Answers
The statement "Computer literacy is understanding the role of information in generating and using business intelligence." is false.
What is computer literacy?Computer literacy is the knowledge and information about using a computer. It includes knowing the computer, how it works, and knowing the language of the computer. The skills that are needed for computers.
It is not about understanding the role of information in business, it is different from computer knowledge. Business knowledge is a different ts subject, it is studied under business subject.
Thus, the statement is false.
To learn more about computer literacy, refer to the link:
https://brainly.com/question/20892584
#SPJ4
Give three examples of the following types of data?
Give three examples for each category in the software domain ?
CCDI :)??


Answers
An example of transactional data are:
Sales ordersPurchase ordersShipping documentsIts software domain are: Personal meeting, a telephone call, and a Video call
An example of financial data are: assets, liabilities, and equity. The software are: CORE Banking, Retail Banking, and Private banking
An example of intellectual property data are: books, music, inventions. The software domain are Patents, trademarks, and copyrights
What types of software are used in the financial industry?Through sales and marketing tools, data-driven contact management, and workflow automation, customer relationship management (CRM) software assists financial services organizations in fostering new relationships and maximizing the value of existing customers.
You can see how your consumers are utilizing your website to complete a transaction by using transaction management software. It may demonstrate both how each website element functions on its own and as a part of the overall technological infrastructure.
Note that Information that is gathered from transactions is referred to as transactional data. It keeps track of the date and location of the transaction, the time it took place, the price ranges of the goods purchased, the mode of payment used, any discounts applied, and other quantities and characteristics related to the transaction.
Learn more about transactional data from
https://brainly.com/question/28081430
#SPJ1
what is data Communications
Answers
Transmission of digital data between 2 or more computers and a computer network or data network
Answer:
Data transmission and data reception is the transfer and reception of data over a point-to-point or point-to-multipoint communication channel. Examples of such channels are copper wires, optical fibers, wireless communication channels, storage media and computer buses.
Derek wants to remove columns from Query he doesn't need. To do so, he can select the columns he wants to remove with Ctrl+Click. Then he can select Remove Columns > Remove Columns in the Query Editor ribbon.True False
Answers
The given statement "Derek wants to remove columns from Query he doesn't need. To do so, he can select the columns he wants to remove with Ctrl+Click. Then he can select Remove Columns > Remove Columns in the Query Editor ribbon" is True.
In Microsoft Office Access, the ribbon is the strip of tabs and icons that sits above the work area. It contains the fundamental commands for working with a database. The Ribbon is a context-sensitive tool that displays the commands that are relevant to the task being performed, such as table design or form creation.
The Query Editor Ribbon, located at the top of the Microsoft Power Query editor window, provides quick access to various commonly used commands. To remove columns from Query in Microsoft Power Query Editor, you can select the columns you want to remove with Ctrl+Click.
Then, in the Query Editor Ribbon, you can select Remove Columns > Remove Columns. The selected columns will be removed from the Query.
You can learn more about Query Editor at: brainly.com/question/30154538
#SPJ11
examine the multicast and broadcast packets that you captured, looking at the details of the source and destination addresses. most likely one has the broadcast ethernet address, as broadcast frames tend to be more common than multicast frames. look at a broadcast frame to see what address is used for broadcast by ethernet. expand the ethernet address fields of either broadcast or multicast frames to see which bit is set to distinguish broadcast/multicast or group traffic from unicast traffic. answer the following questions: 1. what is the broadcast ethernet address, written in standard form as wireshark displays it? 2. which bit of the ethernet address is used to determine whether it is unicast or mul-ticast/broadcast?
Answers
In local area networks, metropolitan area networks, and wide area networks, Ethernet is a family of wired computer networking protocols. It was initially standardized as IEEE 802.3 in 1983 after being commercially released in 1980.
What purposes does Ethernet serve?Ethernet is still a widely used type of network connection and is used to connect devices in a network. Ethernet is utilized for local networks because of its high speed, security, and dependability in places where it is specifically needed, including company offices, campuses of educational institutions, and hospitals.In general, an Ethernet connection is quicker than a WiFi connection and offers more security and dependability.Here's how to get a faster connection while connecting to the internet without Wi-Fi. You can physically connect your computer to the internet using an Ethernet cable. Wi-Fi connections are rarely quicker than Ethernet connections, and Ethernet connections are typically more reliable.Users from all around the world are linked together by the internet in a single, global network. The global infrastructure allows devices connected to the internet to communicate with one another. Local area networks (LANs), a much smaller group of networked devices, are connected by Ethernet.To learn more about Ethernet refer to:
https://brainly.com/question/1637942
#SPJ4
Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
I WILL MARK BRAINLIEST
Create a concept for a new social media service based on new technologies. The service must include functions or features that require using rich media and geolocation or some other location-sharing technology that you have researched.
Submit your plan using both text and visual elements (graphics or drawings).
These are some key points you need to cover in your concept document:
What type of social media service is it?
What is the purpose of the service?
List the functions that the service provides.
List the features that the service provides
What makes the service unique?
Who is the target audience?
What type of layout did you use for the service?
Answers
Answer:... what are the answers u got
Explanation:
Write 3 places clay can be found
Answers
Answer:
sediments , volcanic deposits
Explanation:
_______ codes are supplemental codes used to help researchers collect data, track illness and disease, and measure quality of care
Answers
Answer:
Category II CPT codes are supplemental tracking codes, also referred to as performance measurement codes. These numeric alpha codes [e.g., 2029F: complete physical skin exam performed] are used to collect data related to quality of care.